Researchers Discovered Nine-Year-Old Bug Used in 278,800 Projects
- A team of researchers has discovered a nasty flaw in a widely used npm package called “netmask”.
- The vulnerability has received a rating of 9.8, so it’s highly critical and has a wide spectrum of exploitation.
- Unfortunately, the fixes that have been applied don’t cover all cases, so developers should turn to mitigations.
A team of researchers consisting of ‘Sick.Codes’, John Jackson, Kelly Kaoudis, Victor Viale, and Nick Sahler has discovered a vulnerability in a universal “netmask” npm package that has been lurking for nine years already. Given the identifier CVE-2021-28918, the flaw could enable a malicious actor to perform server-side request forgery, remote file inclusion, local file inclusion, and more. Unfortunately, the particular npm package is enjoying massive success and popularity, having been downloaded over 238 million times and being used in 278,800 software projects in GitHub.
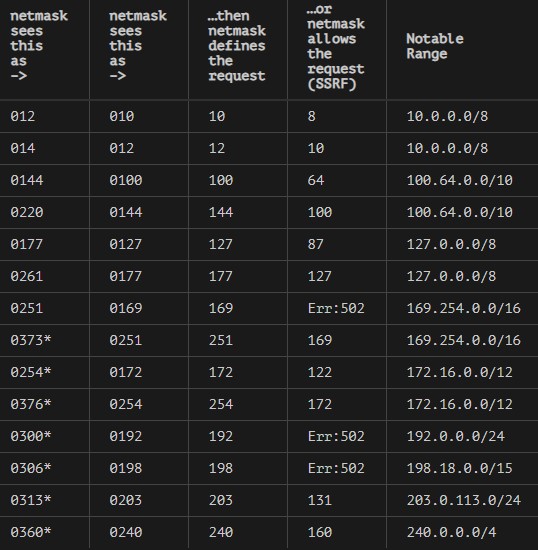
The issue lies in the way that IPv4 addresses are interpreted if prefixed with a “0”, and in the case of the netmask package, any octal input data is parsed as decimal so the zeros at the beginning of an IPv4 address are simply ignored and discarded. The researchers created the following table as an example of what happens.
This opens up a galore of exploit opportunities for malicious actors (or even non-malicious), from directing users to ending up in untrustworthy destinations to offloading malware through laced apps. There’s a range of possibilities when a public URL takes you to private localhost or even the other way around. There are literally countless exploitation scenarios that arise from CVE-2021-28918, so we’re only drawing a rough context here.
Obviously, the researchers couldn’t scrutinize all the projects that use the particular nmp package and figure out which one leads to potentially dangerous places or which one is clearly being exploited. We had a chat with Sick.Codes, and he told us that considering the large pool of projects using the netmask package, the bug might be already under active exploitation. After all, this flaw has been around for nine years, which dramatically increases the chances of others, apart from the researchers, having already discovered it.
As for how such a serious vulnerability in a widely-deployed npm package remained undetected for so long, Sick.Codes tell us that sometimes, the most basic fundamental packages we rely on have the most trivial vulnerabilities, yet it’s equally easy to miss them because they are so widely used that everyone trusts them almost “automatically”. It’s a psychological element that goes to show that everything has a role in infosec.
The team contacted the maintainer of the package, and they collectively tried several fixing approaches, but unfortunately, they haven’t nailed it yet. The new version (2.0.0) of the netmask is safer than before, but the risks aren’t fully mitigated as there are still problems with the node js. Apart from waiting for the final, fixed version of a netmask, the projects using the package could possibly apply the mitigation of enabling strict mode, so only octal literals are evaluated.