Researchers Discover Multiple Risks in Default Apps of Android Smartphones
- Universities from the US and Spain find out that many Android devices are risky by default.
- Almost all of them had at least one pre-installed package that posed some form of a risk to the user.
- The researchers didn’t have enough time or resources to get to the bottom of this, but the picture they painted is already very worrying.
Taking your shiny new Android phone out of the box is immediately a risky endeavor according to a recent paper by a team of researchers from the UC Berkeley ICSI and the Universidad Carlos III de Madrid. While the associated user data collection and activity tracking problems that stem from Android itself are more or less known, the researchers have focused on the pre-installed software that comes with a new smartphone, also known as the “bloatware”. Many of these apps are integral to the functionality of the phone, so the permissions that they have been granted to them by default are a de facto situation.
The problem is an extensive one, as Android phones are pre-loaded with software from their respective manufacturers, the mobile carriers, and even advertisers who are affiliated with these companies. By studying Android devices of more than 200 vendors, the researchers have found that the vast majority of them are plagued by some form of a risky software. The participants in the study comprise 2748 volunteers, using 1742 devices, in 130 countries, who voluntarily allowed the researchers to collect and study firmware and traffic information from their devices.
from the paper
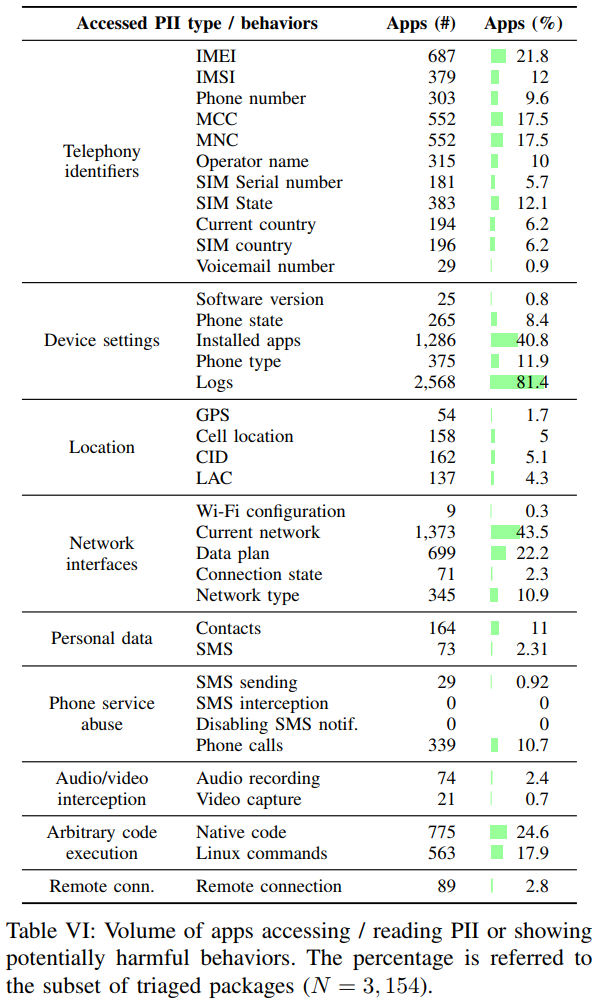
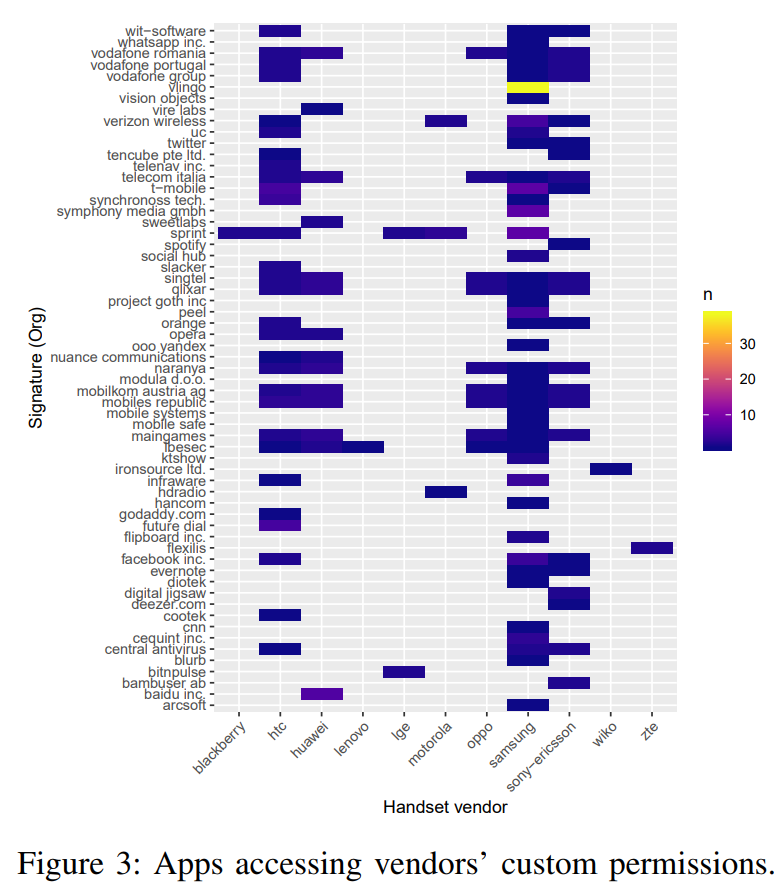
The examples of alarming findings are many in the paper, including custom permissions, over-numbered permissions, risky TPL embedding, and component exposure. For example, the researchers discovered that Samsung, Huawei, and Sony are overly aggressive when it comes to declaring custom permissions. This results in attack surface expansion, and possibly core services exposure. The number of permissions requested by the pre-installed packages is also worrying. 4736 apps asked for at least one permission, and 55 of them asked more than 100! You would think that these 55 are multi-operational utilities, but this is not the case either. For example, the calculator app of Xiaomi Mi 4c requests the user’s location, phone state, IMEI, access to UIDs, and many more.
from the paper
During manual analysis, the team found known malware samples lurking in the system partition, mostly in low-end devices, but also in several high-end models as well. The researchers clarify that their study and the resulting paper are only scratching the surface of what is going on, and since they had a set of 82500 APKs to analyze within a year’s time, it was impossible to study them all, and so they reverted to randomization for the picking of the samples. However, the published results are more than enough to raise alarms and call for more in-depth studies that will be focused on the Android supply chain ecosystem.
Do you trust your Android device’s vendor bloatware? Let us know of your smartphone model in the comments down below. Also, don’t forget to subscribe to our socials on Facebook and Twitter, to get daily fresh news.