Researchers Disclose Five Vulnerabilities Affecting Three D-Link Routers
- Three D-Link routers are vulnerable to local or remote exploitation, depending on their configuration.
- The five flaws that have been disclosed are relatively simple to exploit, although there are some conditions.
- Two of the vulnerable routers have reached their EOL, so they won’t receive fixing updates.
Researchers at LoginSoft have found three flaws affecting the DIR-816L Wireless AC750 Dual-Band Cloud Router, and more specifically, firmware versions 2.06 and 2.06.B09_BETA, which is the latest available right now. D-Link also acknowledged another two flaws affecting the same product and also D-Link DAP-1520 and DAP-1522, so they bundled all five vulnerabilities under a single security advisory that goes as far back as in February 2019.
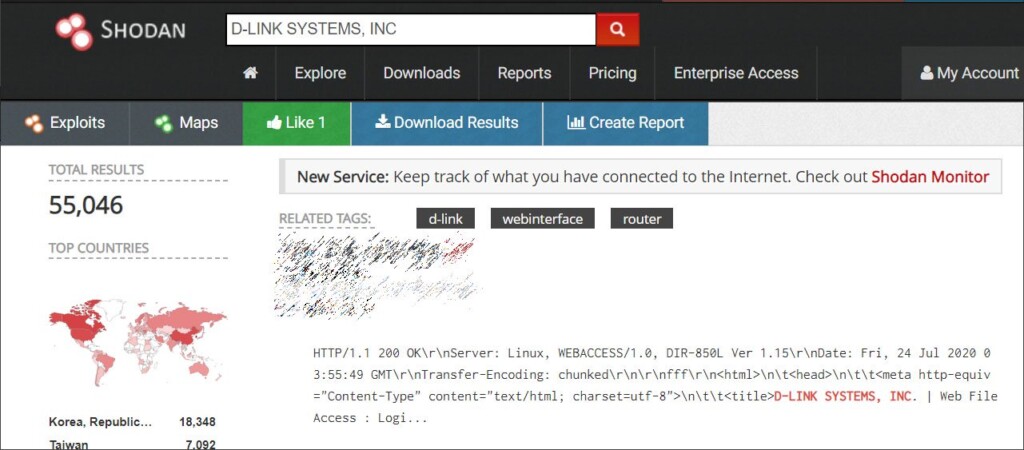
Being an affordable router with powerful features, it is widely deployed out there. According to Bleeping Computer, who conducted a targeted search on Shodan, there are over 55,000 accessible D-Link routers online.
Source: Bleeping Computer
The vulnerabilities are the following:
- CVE-2020-15892 – Buffer Overflow
- CVE-2020-15893 – Command Injection
- CVE-2020-15894 – Information Exposure
- CVE-2020-15895 – Cross-Site Scripting (XSS)
- CVE-2020-15896 – Information Exposure
For most of the above, the attacker would need to have a presence in the target router’s network in order to access the web admin interface. If the user has enabled remote access to the router’s interface, things can be opened up for remote exploitation and even complete take-over.
Related: More D-Link Routers Vulnerable to Remote Command Execution
The proof-of-concept exploits that were published by LoginSoft demonstrate how easy it is to exploit the three flaws by accessing the products’ public IPs. In the case of the CVE-2020-15896, the exploit looks very similar to methods that were first published ten years ago, denoting unacceptable levels of negligence from router vendors like D-Link.
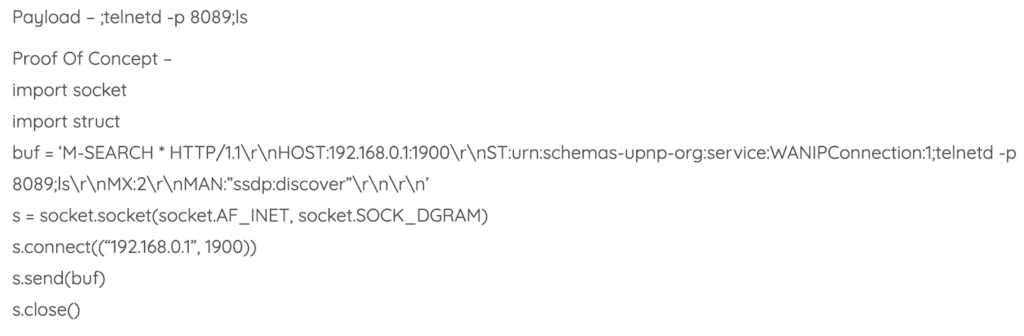
Another interesting exploit concerning the DIR-816L is the one targeting CVE-2020-15893. An attacker can trigger a command injection vulnerability by using a specially crafted M-SEARCH packet. This is made possible by having UPnP (Universal Plug and Play) active by default on port 1900 - which is receiving requests from anyone.
The researchers have demonstrated how a simple python script can provide a gateway for the attacker through telnet service on port 8089, as long as the presence in the target network prerequisite is met.
Source: LoginSoft
As for the official response from D-Link, users of the DAP-1520 are advised to upgrade their firmware to v1.10b04Beta02 or later, which addresses the flaws.
However, the DAP-1522 and DIR-816L models have reached their end of support at this point, so D-Link is not planning to push a fixing firmware update for these products. It means that if you’re using either of them, you should just buy a new router.