Researchers Add More Pieces to the ‘EGoManiac’ Turkish Actor Puzzle
- The Turkish actor‘EGoManiac has been connected with a modular malware toolkit called “Rad”.
- The discovery came by performing a more wide-spectrum analysis on the code of a large set of malware samples.
- The malware was correlated with a set of hardcoded email addresses that led to a 2016 spyware operation.
‘EGoManiac’ is a Turkish actor linked to the ‘Octopus Brain’ campaign, which targeted OdaTV journalists, artificially incriminating them right before their arrest. Now, researchers at Sentinel Labs have done some digging into the actor’s operations, which apparently started over a decade ago, and offer some fresh insight in their latest report. Most notably, they present a toolkit called “Rad,” which is attributed to the particular actors and found in the trace of several of their campaigns over the years.
As Sentinel Labs explains, their investigation into ‘EGoManiac’ went cold in 2017, when they reached a dead end. Today, advances in code analysis tools have enabled them to revisit the case and look into larger chunks instead of smaller snippets, identifying underlying crumbs such as compiler IDs, optimization approaches, statically-linked library rates, etc. This has created a cluster of correlations between the various malware samples that Sentinel Labs held, so they were able to connect the pieces.
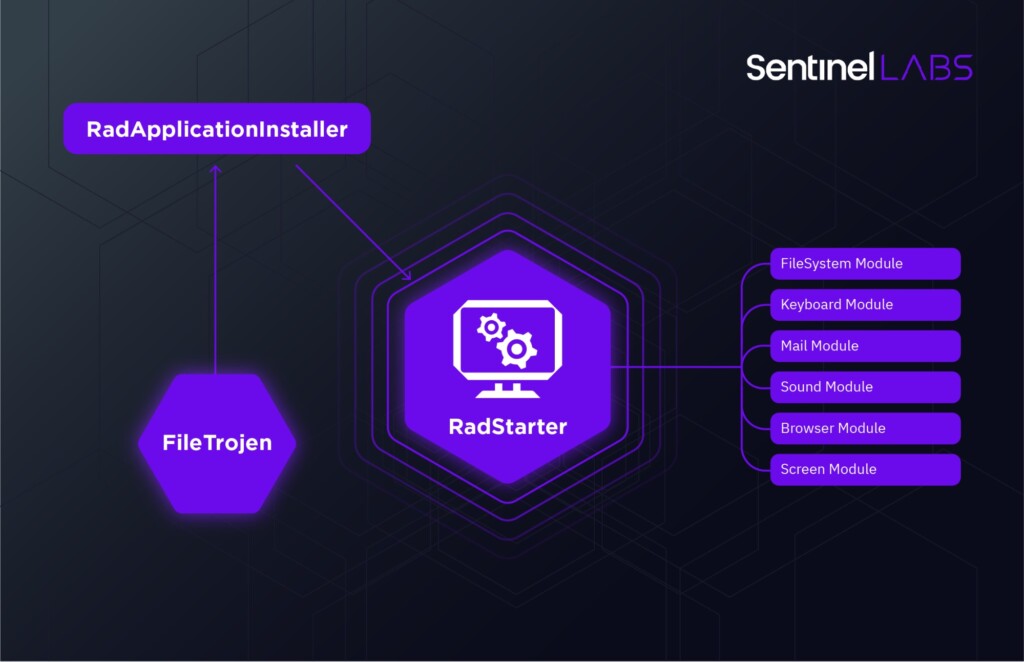
What they found was the “Rad” modular espionage toolkit, encompassing more than 50 malware samples and sub-components. The main module, “wsms.exe,” runs from a registry key set by the installer and launches all other modules as separate processes. These can be keyloggers, microphone recorders, browser cookie extractors, screen capturing tools, file search utilities, and data-exfiltration communication modules.
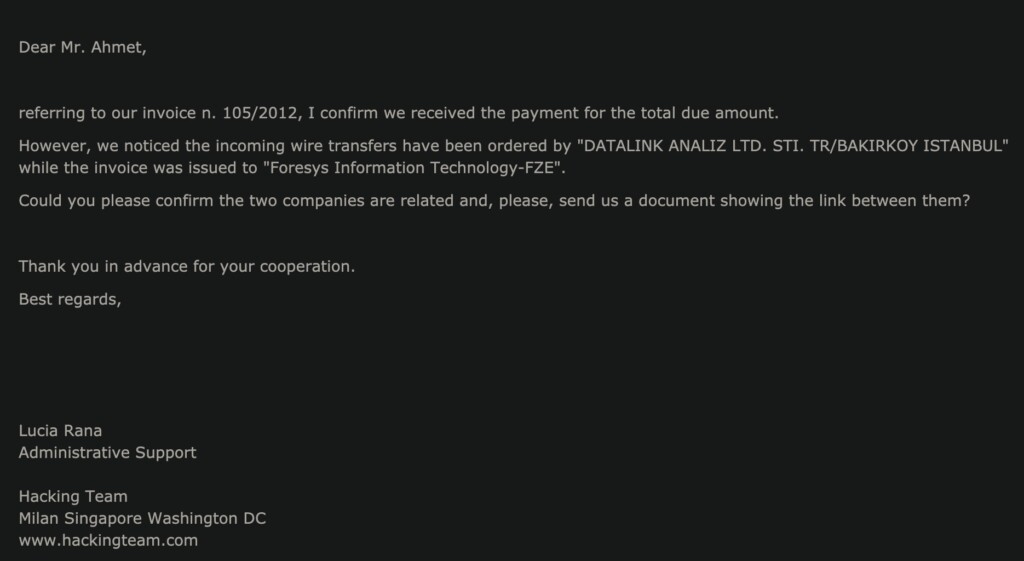
Interestingly, the Rad toolkit has got a set of hardcoded emails that the researchers could use as stepping stones in their investigation. One of them, johndown@woxmail.com, has been used as the data exfiltration address in a 2016 operation involving a Turkish IT company called ‘Datalink,’ which was reported to be leaking key info on active police operations. These leaks were used by FETO/Gülenist movement social media accounts, which weren’t in alliance with president Erdoğan at the time.
In that operation, a spyware called ‘HORTUM’ had been deployed to siphon data from the compromised devices, which was also linked to Hacking Team’s ‘Da Vinci.’ Turkey has been confirmed as a customer of the Hacking Team, but who the exact client is remains a mystery. Sentinel Labs has made a connection there, but the strand is thin.
In conclusion, ‘EGoManiac’ appears to hit both friends and foes depending on who’s paying them, entrapping journalists who criticize and expose the government in one case - and then giving food for anti-government campaigns on social media in the other. This makes another case for the perils of shady spyware deployment, unregulated use of malware, and the very integrity of the rule of law and evidence evaluation standards.