Researcher Demonstrates How Easy It Is to Create Malicious Proxies on Chrome
- A security researcher has released the “CursedChrome” extension, which can set up proxies on target browsers.
- This way to compromise systems is helpful when malware planting isn’t possible, and it's also a stealthy way to launch attacks.
- Already, there are mitigation measures and tools available out there, with one coming from the extension’s author.
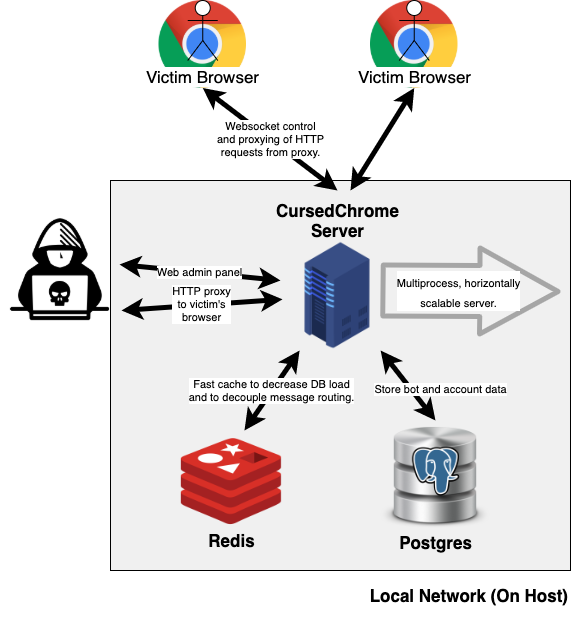
Security researcher Matthew Bryant has created a Chrome extension that he named “CursedChrome,” and released its code on GitHub. The extension is meant to be used as a demonstration of how easy it is to plant something that turns the target’s Chrome browser into a fully-functional HTTP proxy. By using such proxies, attackers could potentially hide behind their victims’ computers to launch attacks to other systems without risking their identification, as well as to hijack the victims’ web sessions.
Source: GitHub
The researcher released the extension as an open-source to help everyone analyze it and bolster their security practices. This also implies that attackers will have their chance now. The duration of the “period of grace” for malicious actors will depend on how soon the security community responds. Right now, everything is moving to the Web browser, and hijacking Web sessions is becoming hotter for hackers. As the author points out, his creation is particularly stealthy, as all requests come with the appropriate source-IP, cookies, client-certificates, etc
Source: GitHub
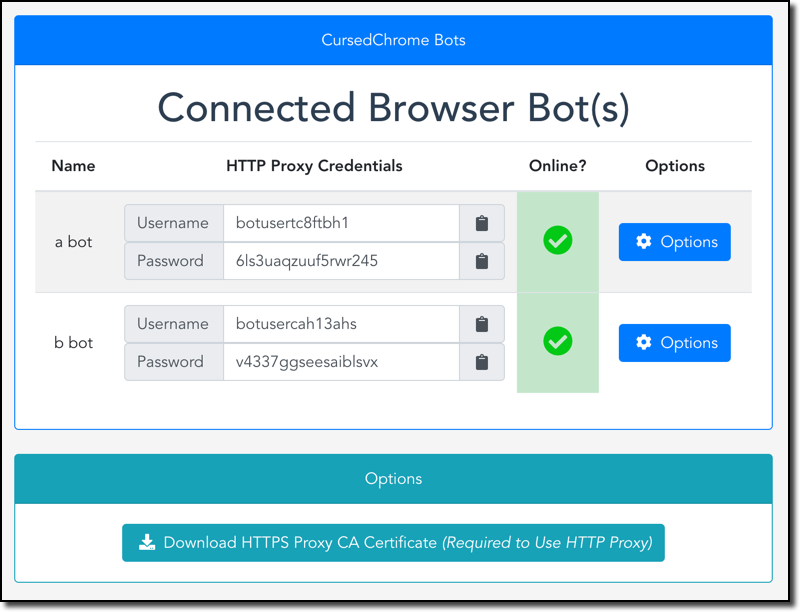
There’s even a comfortable panel from where the attackers may pick which infected host they want to connect to. Once they do, they can hijack the logged-in sessions and access all areas where the victims have already authenticated to, including corporate VPN networks and enterprise apps. This takes out the need to steal credentials or plant malware, and in systems like Chrome OS, the scenario of planting malware isn’t even a possibility.
All that said, you shouldn’t fear seeing this extension on the official Chrome Web Store, as having it pass through Google’s reviews without detection is highly unlikely. An attacker would have to install it via an enterprise policy or through the developer mode on Chrome.
The researcher stated that he was initially reluctant to release this offensive security tool to the public. Still, he eventually figured that it would have a positive impact on the security of companies right now. He suggests one crucial mitigation that happens to be another project of his, the “Galvanizer.” By using this tool, one can generate Chrome enterprise policies that would prevent risks like the “CursedChrome.” That said, it all seems like a security practice meant to raise awareness, as well as to bolster the security of corporate networks. The only ones who will lose from this code release are those who opt to remain uninformed.