Red Hat Confirms Security Breach of Consulting GitLab Instance, Hackers Claim Stealing 570GB and Client Data
- Incident confirmed: Red Hat has confirmed unauthorized access to a GitLab instance used by its consulting team for select client engagements.
- Exfiltration claims: A hacker group claims to have stolen nearly 570GB of data, including around 800 Customer Engagement Reports (CERs).
- Customer impact: The compromised data may contain project specifications, code snippets, and infrastructure details for certain consulting clients.
Red Hat has officially confirmed it is investigating a cybersecurity incident involving unauthorized access to an internal GitLab environment. The breach was isolated to a specific instance used by the Red Hat Consulting team for collaboration on certain customer projects.
Hackers Claim Data Theft
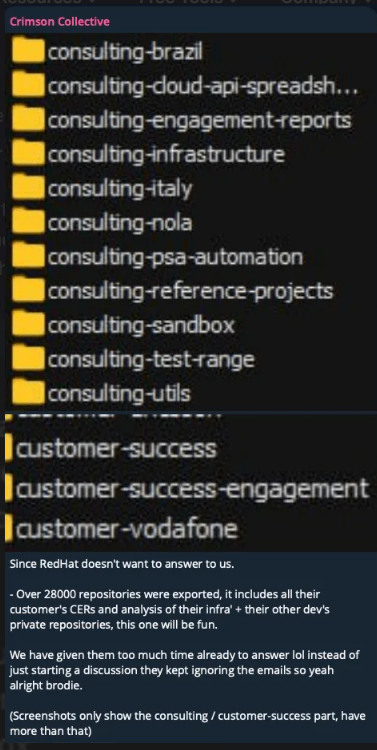
The Crimson Collective hacking group has claimed responsibility, alleging the theft of nearly 570GB of data that includes information from approximately 28,000 internal projects and, more critically, around 800 customer engagement reports (CERs) from 2020 to 2025.
The hacking group also published the allegedly stolen GitLab repositories and a CERs list on Telegram to support their claims. Victims listed include:
- Bank of America,
- T-Mobile,
- AT&T,
- Verizon,
- Fidelity,
- Walmart,
- Costco,
- the U.S. Navy’s Naval Surface Warfare Center,
- National Security Agency (NSA),
- the Department of Energy,
- the National Institute of Standards and Technology (NIST),
- IBM,
- Citi,
- Siemens,
- Bosch,
- JPMorgan Chase,
- HSBC,
- Telefónica.
These reports could contain sensitive information such as client infrastructure details, configuration data, and authentication keys. The Centre for Cybersecurity Belgium (CCB) stated that the Crimson Collective already used leaked authentication tokens to access customer systems.
“We recently detected unauthorized access to a GitLab instance used for internal Red Hat Consulting collaboration in select engagements,” the Red Hat announcement reads.
Upon detecting the intrusion, Red Hat reports that it immediately removed the unauthorized party's access, isolated the system, and initiated a full investigation.
However, the company stated this incident is unrelated to its core products or software supply chain. “At this time, we have no reason to believe this security issue impacts any of our other Red Hat services or products, including our software supply chain or downloading Red Hat software from official channels.”
This incident is unrelated to a Red Hat OpenShift AI vulnerability (CVE-2025-10725) that was recently announced.
Potential Impact on Consulting Customers
While Red Hat has stated that the compromised GitLab instance does not typically house sensitive personal data, the alleged exfiltration of CERs may pose a significant risk to affected consulting clients.
Information within these reports could potentially be used by malicious actors to target downstream customer networks.
CCB assesses that this data breach poses a high risk for organisations that used Red Hat Consulting services or shared sensitive information (e.g., credentials, tokens, network data) with Red Hat and recommends:
- Revoking and rotating all tokens, keys, and credentials shared with Red Hat or used in integrations.
- Engaging third parties – ask your IT providers or partners whether they used Red Hat Consulting and assess your potential exposure.
- Contacting Red Hat for guidance on your specific exposure
- Increasing the monitoring of authentication events, API calls, and system access for anomalies.
In other recent news, the U.S. Air Force is investigating a suspected SharePoint breach that exposed sensitive data.