The “RATicate” Group Is Abusing NIST Files to Drop a Wide Range of Payloads
- The “RATicate” hacking group is distributing various payloads via NIST installers.
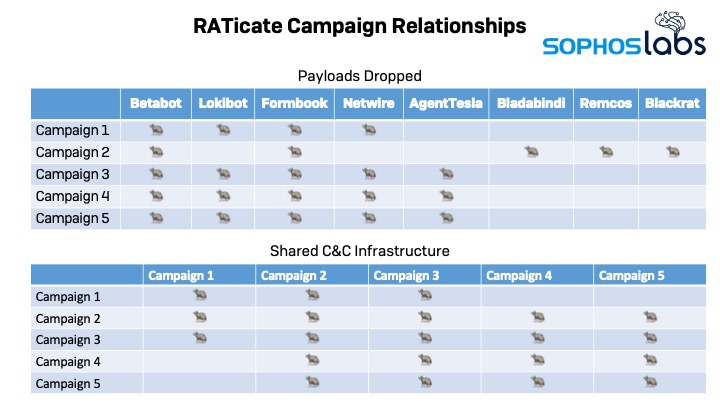
- The group has used at least eight different payloads in five attack waves that took place recently.
- The attribution is the result of common packing methods and overlapping infrastructure.
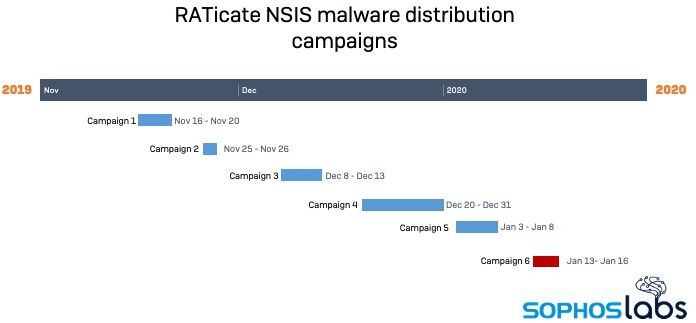
Five separate campaigns recorded between November 2019 and January 2020 have researchers believe that the threat actors group dubbed “RATicate” is out there engaging in cyber-espionage. The hackers are distributing RATs (remote administration tools) in waves - and the similarities between the payloads, as well as the overlapping of the C&C infrastructure, confirm the origin and give leads to the attribution. The targets of these campaigns were mainly industrial companies in the Middle East, Europe, and South Korea. This could mean that RATicate is a North Korean group, Russian, or even Chinese, although this remains entirely unknown at the moment.
Source: Sophos
The actors are utilizing NSIS (Nullsoft Scriptable Install System) installers, which enable them to bundle malware that features a plug-in architecture that is able to communicate with Windows OS components. During their deployment, the plug-ins that come with the payload are served as Windows DLL files, while the installer used is dropping a large amount of “junk files” that are meant to hide the actual malware by creating “noise.” The capabilities of the plug-ins that are used in general by RATicate include the following functions:
- Kill processes
- Execute Command Line-based programs
- Dynamically decompress files
- Load a DLL and call to its exports
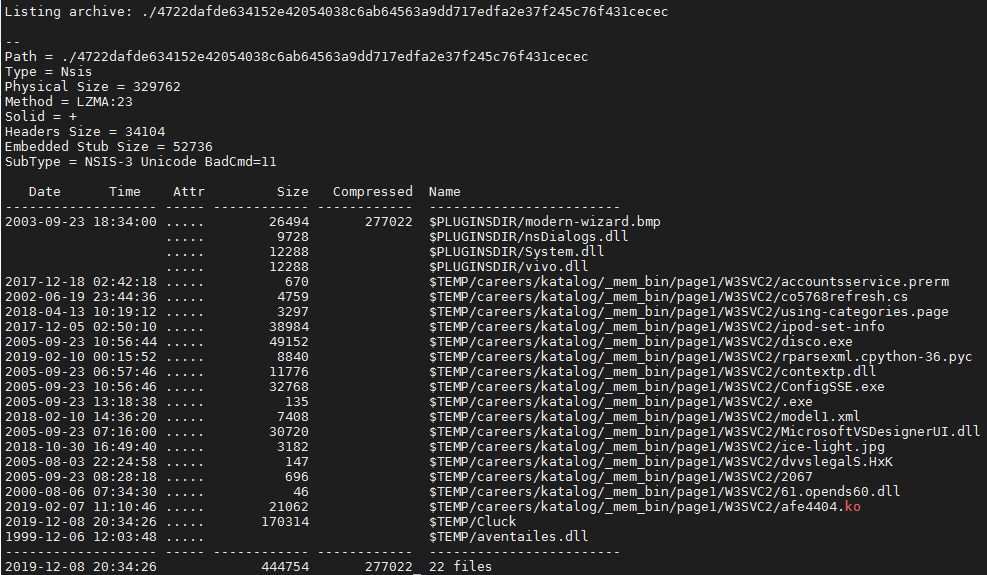
The following files are dropped into the “%TEMP%/careers/katalog/_mem_bin/page1/W3SVC2” folder. Among these, the only two that hold any value to the malware are the “aventailes.dll” (which is the initial loader) and the “Cluck” (which contains the encrypted data.
Source: Sophos
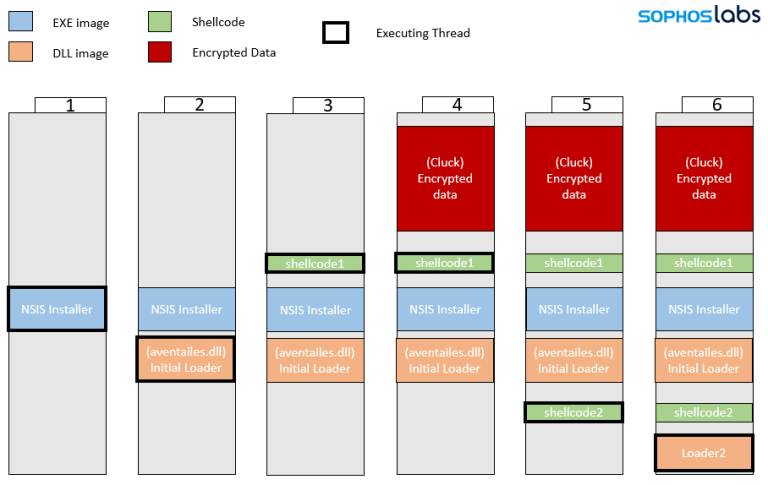
The researchers believe that the aventailes.DLL loader is a custom loader that was developed by RATicate themselves. Upon deployment, the malicious DLL performs the exporting of the encrypted shellcode. Then, the Cluck file is parsed for the decryption to take place using a xor key. In the following diagram, Sophos explains how the infection procedure takes place.
Source: Sophos
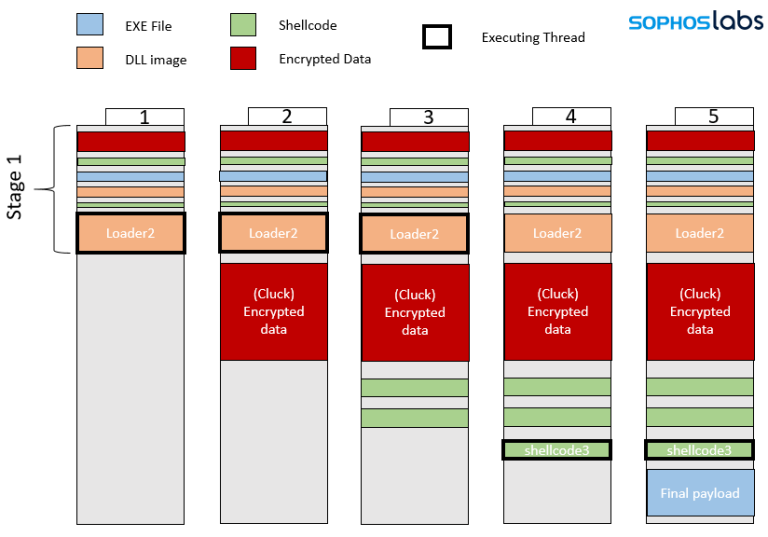
The above leads to a series of decryptions and “jumps,” which takes us to Loader2, the execution thread of which is detailed below.
Source: Sophos
RATicate deployed a wide range of payloads, including Betabot, Lokibot, Netwire, Formbook, Bladabindi, Blackrat, Remcos, and AgentTesla.
Source: Sophos
From the tools used in all of the above cases, it is evident that the group was attempting to gain access and control the target systems. To stay safe from these threats, you should avoid downloading and opening attachments that arrive on your computer via unsolicited emails, as these may contain an enriched NSIS installer. These actors target organizations and companies, which is why advanced email security systems should be in place.