“Rampant Kitten”, an Iranian Surveillance Operation Coming to Light
- Iranian expats, minority groups, and people who oppose the government are being targeted by a new surveillance campaign.
- The hackers who launch the attack use a diverse and powerful set of tools, including an Android backdoor and Windows info-stealers.
- The focus of the attackers is Telegram, account credentials, and the collection of information in general.
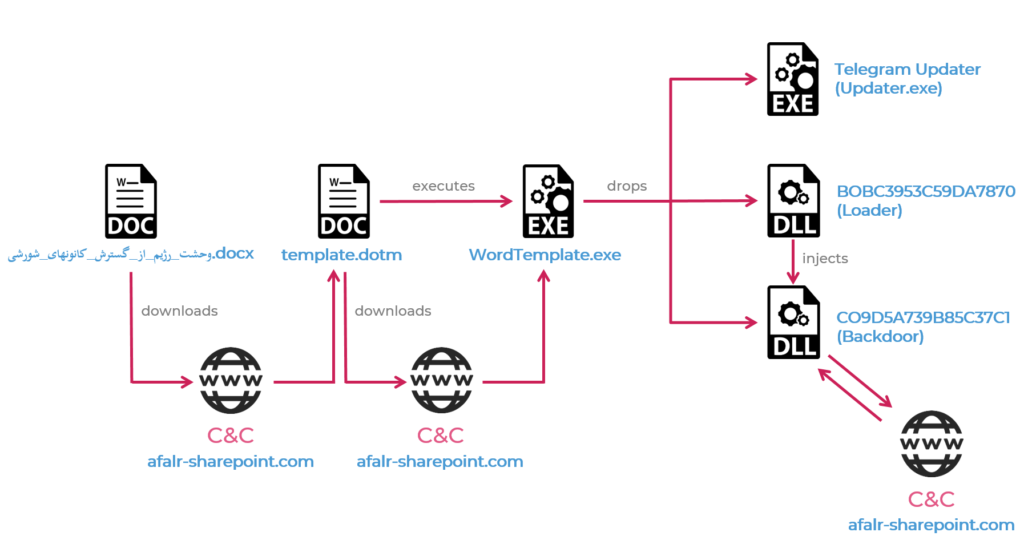
Check Point Research has discovered a massive espionage operation set up by Iranian entities, and which targets mainly expats and dissidents. The tools that are deployed in the still ongoing operation are highly sophisticated, including an Android backdoor that can extract two-factor authentication codes from SMS messages, Telegram phishing pages, and four variants for Windows info-stealers that steal both documents and account credentials.
The confirmed targets of the campaign include the Balochistan people, the Azerbaijan National Resistance Organization, and the Association of Families of Camp Ashraf and Liberty Residents (AFALR).
Source: Check Point
The initial compromise of the victims happens through laced documents that carry a malicious payload. The malware is actually an info-stealer that focuses a lot on Telegram because most of the aforementioned activists trust and use Telegram for their communications. So, the payload checks if Telegram is installed on the machine, and if it is, it injects a modified updater.
From there, the malware can steal Telegram accounts, information from the KeePass (password manager), log clipboard data, take screenshots from the desktop, and even download and install additional modules. The malware stays persistent even if the user updates their Telegram installation, so this is no way to unroot it.
Source: Check Point
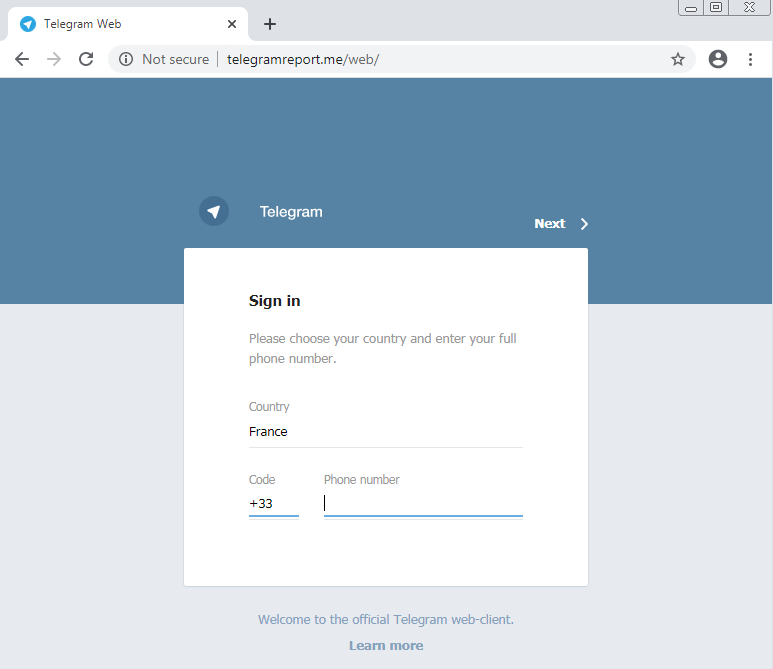
The Android backdoor masquerades as a service for Persian speakers in Sweden, so it targets expats there. Its capabilities include the stealing of SMS messages, 2FA code exfiltration, contact list retrieval, voice recording, microphone activation, Google account phishing, tampering with running processes, and more. Again, Telegram is actively targeted, and victims are regularly pointed to phishing pages that are themed accordingly.
Source: Check Point
We know who the targets are, and we can assume who could be behind the "Rampant Kitten" operation, but Check Point couldn't make any definitive attributions. The traces that were left from the threat group or entity point to domains that were registered by spoofed or fake identities, while one of the email addresses were used to register on Iranian hacking forums too.
The focus on Telegram and KeePass denotes that the hackers' goal is to collect information, so there seem to be no financial motives involved. The Iranian government has tried to ban the use of Telegram in the past, and when COVID-19 hit the country, they spawned apps that were basically spyware, contracting a developer known for putting shady Telegram forks out there. Still, we can't attribute "Rampant Kitten" to the Iranian state, but the pieces definitely fit.