Qilin Becomes Leading Ransomware Group in April Following RansomHub’s Alleged Fall
- Qilin Ransomware sees a rise as RansomHub falters amid uncertainty regarding the latter’s future.
- The group had the highest number of victims last month, yet a decline in the total number of ransomware attacks was seen in April.
- Qilin was followed closely by Akira Ransomware, then Play Ransomware in the third place.
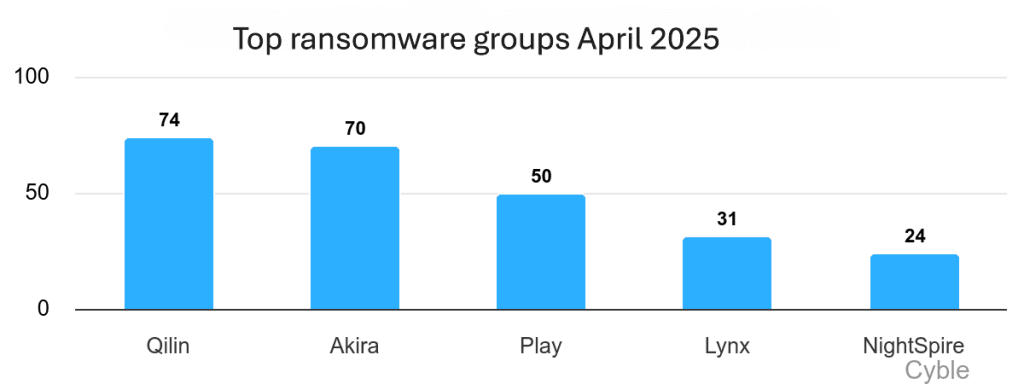
The ransomware landscape continues to evolve as Qilin emerged as the most active ransomware group in April, claiming the highest number of victims, while the total volume of ransomware attacks declined.
April saw major disruption amongst ransomware groups due to internal upheaval at RansomHub, according to a detailed report by Cyble.
The group’s data leak site went offline on April 1, and DragonForce subsequently claimed to have taken over RansomHub’s infrastructure, urging its affiliates to join forces. However, it appears that Qilin capitalized most effectively on the chaos.
Cyble’s findings indicate that Qilin had the highest activity in April, claiming 74 victims. Conversely, DragonForce concluded the month with only 21 claimed victims.
The report from Cyble noted that this situation exemplifies the volatility within cybercriminal networks and highlighted the intense competition driving the rapid evolution of ransomware-as-a-service (RaaS) capabilities.
Despite Qilin’s rise, the total number of ransomware attacks recorded in April declined compared to the previous month. Cyble documented 450 ransomware victims in April, down from 564 in March.
Although this marks a temporary slowdown, Cyble warned that long-term trends demonstrate a rising trajectory. The report suggests that April’s decline may reverse quickly as new RaaS leaders emerge.
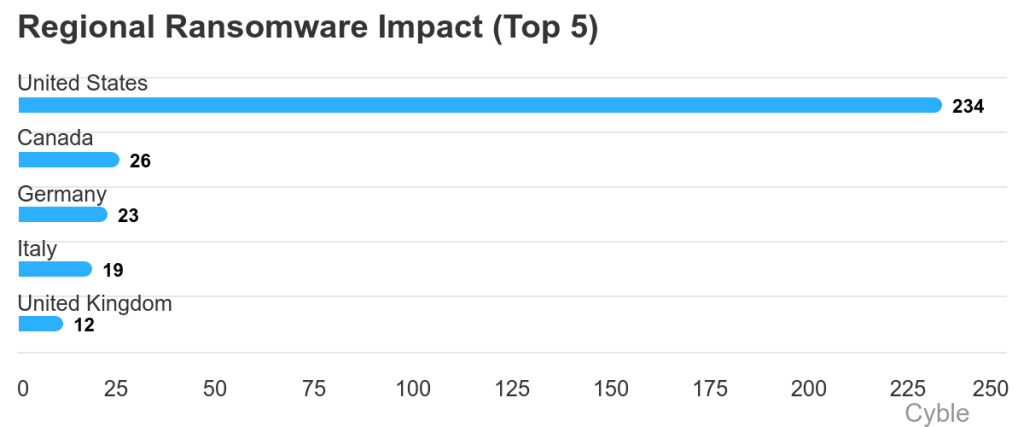
Regionally, the U.S. remained the primary target, representing 52% of global attacks at 234 incidents, more than doubling Europe’s share of 108. Play was the most active ransomware group targeting U.S.-based organizations, with 42 claims of compromise.
Globally, newer groups like RALord and Sarcoma showed prominence in the META and Asia-Pacific regions, respectively, further diversifying the regional spread of ransomware activity.
Cyble identified two new ransomware groups in April, Silent Team and Gunra, which claimed a few victims. Despite the decline in attack volume, significant incidents raised concerns about software supply chain vulnerabilities and potential downstream impacts.
Akira ransomware targeted a U.S. energy cooperative serving northeastern Georgia counties.
Play ransomware compromised two U.S.-based software providers, triggering fears of supply chain disruptions.
Qilin ransomware victimized a France-based software company active in transportation logistics, resulting in the exfiltration of source code and other sensitive data.
DragonForce’s DevMan affiliate compromised a Chinese infrastructure company and targeted organizations in Taiwan and the UAE.
Additionally, Hellcat and Rhysida ransomware groups reported notable claims in the engineering, technology, and manufacturing sectors, underlining the overlap between critical infrastructure and cybercriminal focus.