PureVPN Suffers from Two Vulnerabilities That Can Leak Passwords [Updated]
- Security researchers have found two critical vulnerabilities in popular VPN service PureVPN.
- Both vulnerabilities allow hackers access to stored user passwords through files created by the VPN client.
- One of the two vulnerabilities has been patched while the other is still active.
Popular VPN service provider PureVPN has suffered from two critical vulnerabilities that can leak user passwords. The vulnerabilities were tested and confirmed by security researcher Manuel Nader from Trustwave and the security team of PureVPN as well.
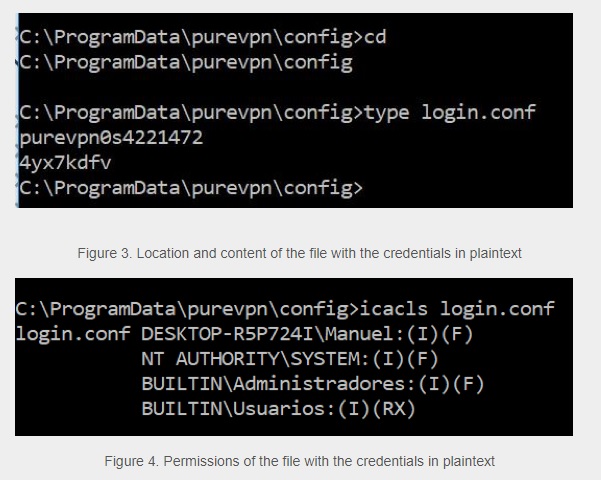
Out of the two vulnerabilities, one of them have already been patched out by the developers while the other is still active and PureVPN is aware of the risks that it poses. The vulnerability was caused due to saved passwords being stored in plain text format. It is not the first time that a service has been caught storing passwords in plaintext format with multiple other services being found guilty of the same.
Image Courtesy of TrustWave
Any user could access and read the password by opening the file using Command Prompt. Stealing the password would require physical access to a system or the ability to get access remotely through other hacking methods. The VPN service provider has recommended users to update to the latest version which contains a patch to one of the two vulnerabilities.
The VPN service provider revealed in a statement “The PureVPN Windows Client provided by PureVPN may allow a local attacker to retrieve the stored password of the last user who successfully logged in to the PureVPN service. Because of this, a local attacker may obtain another user's PureVPN credentials when a Windows machine has multiple users if they have successfully logged in. The attack is done exclusively through the GUI (Graphical User Interface), there's no need to use an external tool.”
The company has not yet revealed when the software will be patched to remove the remaining vulnerability. It is recommended to temporarily use a different VPN if you do not want to put yourself at any risk at all until the vulnerability is fixed. Our team has reached out to PureVPN and waiting for their response about this issue.
--Update--
Kelly from PureVPN responded to our mail, "Our systems work a bit different than most of the other VPN providers. For enhanced security, we use separate passwords for Member Area and VPN access. Member Area password which is more privileged is not shown in apps, it's the VPN access password that is the subject of this feature. Furthermore, by default, our VPN passwords are system generated and not set by users. This curtails the risk of users using the same password for VPN accounts that they use for their sensitive accounts elsewhere on the Internet. On the other hand, this enhanced security design proved a little difficult for quite a few of our users and hence we offered a way for them to easily retrieve their VPN password."
She also stated "For now, the community has raised concerns and is confusing it as a vulnerability, we have temporarily removed the feature and released a newer version 6.2.2. To those users of our who pretty much use this feature to retrieve the separate password for VPN, we would like to inform that we plan to redesign the future, keeping these concerns in mind, and release it back in our November 2018 release."
What do you think about the vulnerabilities found in the VPN service? Let us know in the comments below. Also, don’t forget to follow us on Facebook and Twitter. Thanks!