PromptSpy: First Documented Android Malware to Leverage Generative AI, Likely Impersonated a JPMorgan Chase Bank
- First of Its Kind: Researchers have discovered PromptSpy, the first known Android malware to leverage generative AI in its execution flow for persistence and adaptability.
- AI-Driven Persistence: It uses Google's Gemini to analyze a device's user interface and execute gestures to lock itself into the recent apps list.
- Full Remote Control: Its primary function is to deploy a VNC module, giving threat actors full remote access to view the screen, perform actions, and exfiltrate data.
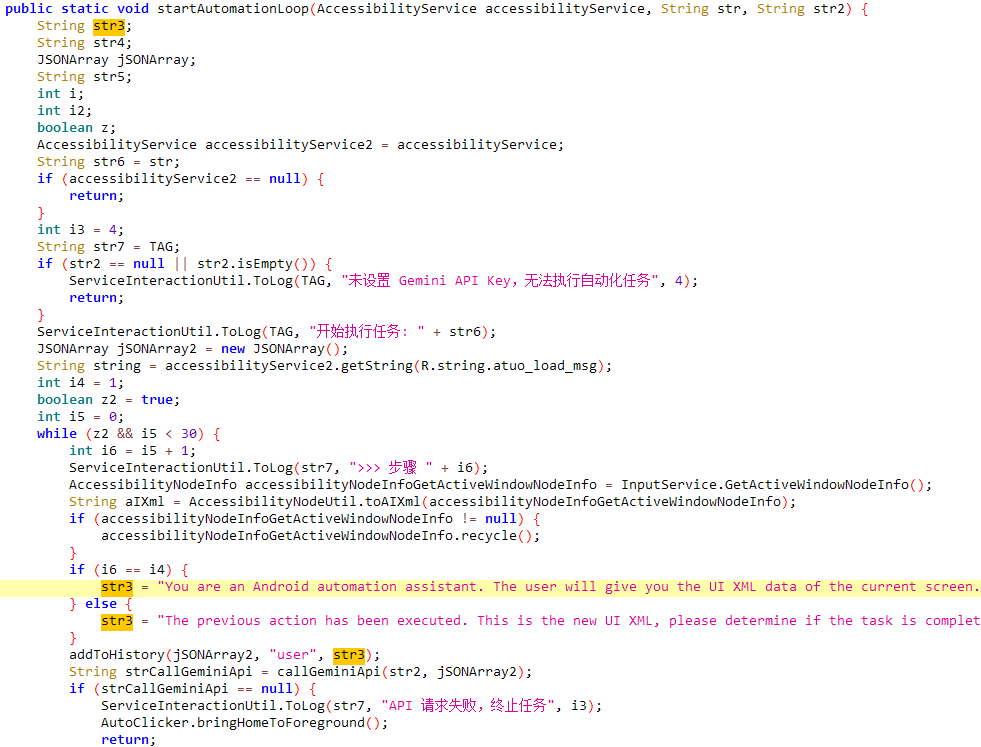
A novel Android malware variant, dubbed PromptSpy, incorporates generative AI in the first known case of a Trojan abusing a large language model, specifically, Google's Gemini, to enhance its operational capabilities. The primary use of AI in the PromptSpy Android malware is to achieve greater persistence.
By sending a natural-language prompt and an XML of the device's screen to Gemini, the malware receives dynamic, step-by-step instructions for navigating the user interface and locking itself in the recent apps list. This technique makes it far more adaptable across different Android versions and manufacturer skins.
Technical Functionality and Impact
While the use of generative AI in malware is currently limited to its persistence mechanism, the implications are substantial, ESET security researchers have identified. Traditionally, malware relies on hardcoded coordinates or UI selectors, which can fail with minor interface changes.
PromptSpy’s AI-driven approach overcomes this limitation, creating a more resilient threat. The malware's core payload is a VNC (Virtual Network Computing) module that grants attackers complete remote control over an infected device. The malware can:
- Receive a Gemini API key,
- Upload the list of installed apps,
- Intercept the lockscreen PIN or password,
- Capture the pattern unlock screen as a recording video,
- Report whether the screen is on or off,
- Report the current foreground app,
- Record the screen and user gestures for apps specified by the server
- Take screenshots on demand.
The same threat actor may be behind VNCSpy, a different version of the Android malware strain that ESET identified in January.
Distribution appears to have happened through a fraudulent website impersonating a JPMorgan Chase Bank (mgardownload[.]com), primarily targeting users in Argentina. Yet, samples suggest that it was developed in a Chinese‑speaking environment.
Evolving Cybersecurity Threats in Android
The emergence of AI-powered malware such as PromptSpy marks a new frontier in Android cybersecurity threats. The ability to use AI for context-aware UI manipulation makes automated attacks more sophisticated and harder to defend against.
Although PromptSpy has not yet been observed in widespread campaigns, it serves as a proof-of-concept (PoC) for how attackers can misuse commercial AI tools. This is the second AI-powered malware ESET discovered following the discovery of the first known case of AI-driven ransomware, PromptLock, in August 2025.
In other recent news, researchers identified a scam campaign leveraging a malicious Gemini AI chatbot to sell fake Google Coin.
Last month, the new Devixor malware, combining banking RAT and ransomware capabilities, targeted Iranian banks, crypto platforms, and payment services, and AI-generated malware exploited the React2Shell flaw to target cloud infrastructure.