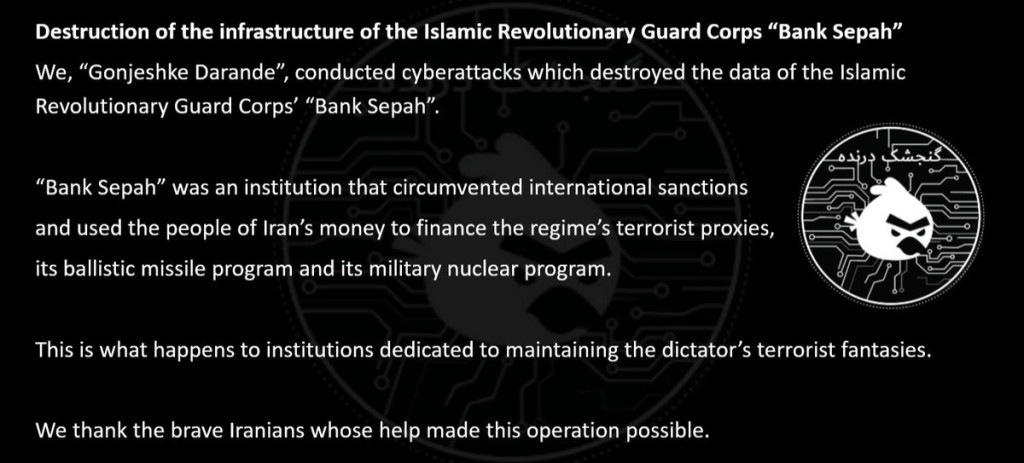
Pro-Israel Hacktivist Group ‘Predatory Sparrow’ Claims Cyberattack on Iran’s Bank Sepah
- A self-proclaimed hacktivist group that supports Israel announced an alleged breach of an Iranian bank.
- The actors said they destroyed Bank Sepah’s data due to the institution reportedly funding Iran’s ballistic and nuclear programs.
- The exact identity or affiliations of the group remain unknown, leaving their ties to any Israeli entities uncertain.
The pro-Israel hacktivist group Predatory Sparrow, also known by its Persian name Gonjeshke Darande, claimed responsibility for an alleged cyberattack on Iran’s Bank Sepah on Tuesday via X (formerly Twitter).
The group stated that it targeted and successfully destroyed Bank Sepah’s data, saying the institution was linked to the Islamic Revolutionary Guard Corps (IRGC).
The statement alleged the bank was used to circumvent international sanctions and siphon Iranian citizens’ funds to support terrorist operations, ballistic missile developments, and military nuclear programs for the Iranian regime.
Reports from the independent news source Iran International highlighted substantial banking disruptions across the country following the announcement.
Multiple Bank Sepah branches reportedly closed, with customers unable to access their accounts. Images shared by Ariel Oseran, an i24NEWS correspondent, purportedly show Iranian ATMs displaying error messages.
Attempts to independently verify the hack remain inconclusive. Efforts by reporters to obtain responses from Bank Sepah’s headquarters and affiliates were unsuccessful, as email communications returned errors, and affiliated offices in the U.K. and Italy did not comment.
Additionally, Predatory Sparrow declined inquiries sent via their X account and Telegram.
The cyberattack coincides with escalating tensions between Israel and Iran. Both nations have launched strikes targeting each other’s infrastructure, military facilities, and key personnel.
Analysts suggest the ongoing conflict over Iran’s nuclear energy facilities and military operations could intensify cyberwarfare activities.
Predatory Sparrow has a track record of targeting Iranian organizations, and cybersecurity experts affirm that their claims in past attacks have often proven credible.