PRC-Nexus Espionage Campaign Targets Diplomats with Web Traffic Hijacking to Deliver Malware
- PRC-nexus espionage: A UNC6384 cyber operation demonstrates escalated capabilities in state-sponsored cyber espionage.
- Who is targeted: The multi-stage attack chain is aimed at diplomatic entities across Southeast Asia.
- Attack details: Attackers deploy the SOGU.SEC malware variant via AitM techniques and legitimate infrastructure hijacking.
A sophisticated PRC-nexus espionage campaign, orchestrated by threat actor UNC6384, targets diplomatic entities across Southeast Asia through an advanced, multi-stage attack chain, employing adversary-in-the-middle (AitM) techniques and legitimate infrastructure hijacking to deploy the SOGU.SEC malware variant.
Captive Portal Hijacking and Social Engineering
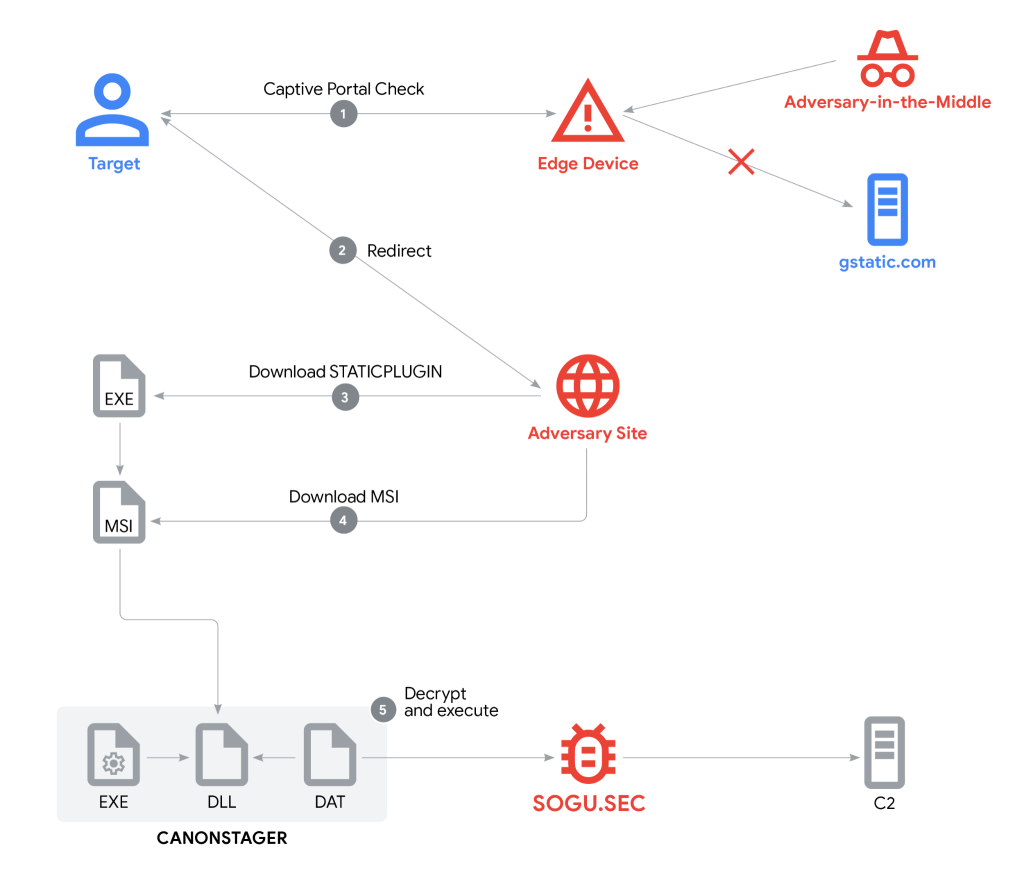
The attack initiates through captive portal manipulation, exploiting the standard browser mechanism that tests internet connectivity via HTTP requests to legitimate domains.
Google Threat Intelligence Group (GTIG) has discovered evidence of compromised edge devices facilitating AitM attacks, redirecting targets from legitimate Google infrastructure to threat actor-controlled domains.
The diplomatic cyberattacks leverage sophisticated social engineering, presenting victims with convincing Adobe plugin update notifications hosted on HTTPS-secured domains with valid Let's Encrypt certificates.
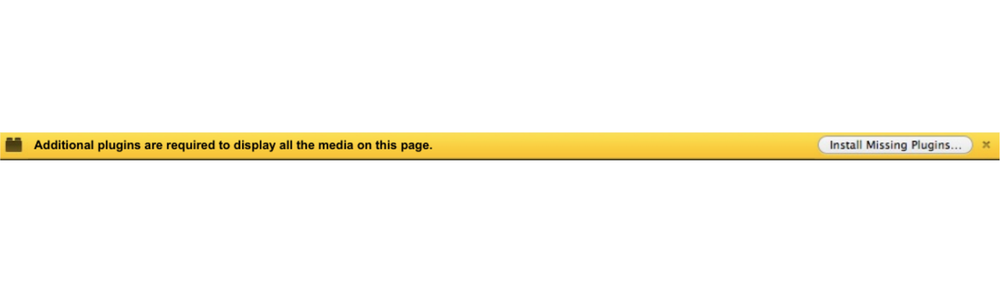
The China-nexus threat actors implemented comprehensive deception strategies, including blank landing pages with yellow notification bars prompting users to "Install Missing Plugins."
Background JavaScript executes automatically, displaying detailed bypass instructions for Windows security protections while initiating downloads of digitally signed malware disguised as legitimate software updates.
Multi-Stage Malware Deployment Chain
The campaign employs STATICPLUGIN, a digitally signed downloader utilizing certificates from Chengdu Nuoxin Times Technology Co., Ltd. This initial payload retrieves MSI packages containing three components:
- a legitimate Canon printer executable
- a novel side-loaded DLL tracked as the CANONSTAGER launcher
- encrypted SOGU.SEC payload data
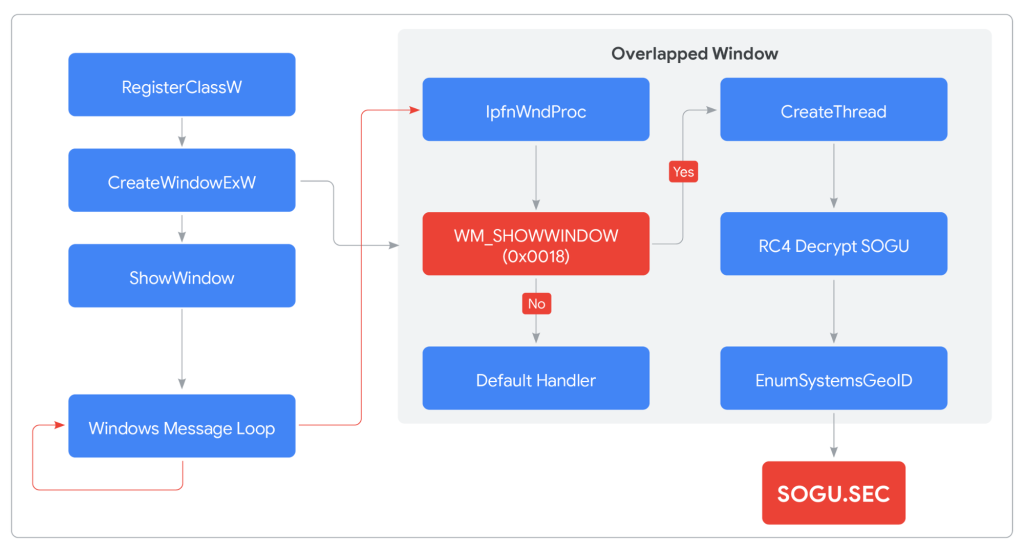
CANONSTAGER demonstrates advanced evasion techniques, implementing custom API hashing with Thread Local Storage (TLS) for function address concealment.
The malware leverages Windows message queues and callback functions for indirect code execution, creating zero-pixel windows to remain undetected while processing WM_SHOWWINDOW messages that trigger payload decryption.
Attribution and Strategic Implications
GTIG attributes this campaign to UNC6384, associated with TEMP.Hex (Mustang Panda), based on tooling similarities, targeting patterns, and command and control (C2) infrastructure overlaps. The threat actor's focus on Southeast Asian diplomatic targets aligns with the strategic intelligence collection priorities of the People's Republic of China.
The campaign represents a significant evolution in PRC-nexus operational capabilities, combining legitimate certificate abuse, infrastructure compromise, and in-memory execution techniques.
Google has implemented comprehensive protective measures, including government-backed attacker alerts for affected Gmail and Workspace users and Safe Browsing updates blocking identified malicious resources.
In July, TechNadu reported that the U.S. National Guard was hacked by China's Salt Typhoon, which maintained access for almost a year. The same threat actor was linked to the Viasat hack.