Powload Still Alive, Powerful, and Continually Evolving
- Powload is here to stay, as attackers are continuously putting an effort in its development.
- From its victim targeting process to its malicious code delivering, everything has grown more targeted and persistent.
- Even the spam mail content has been polished to trick victims and weaker spam filters.
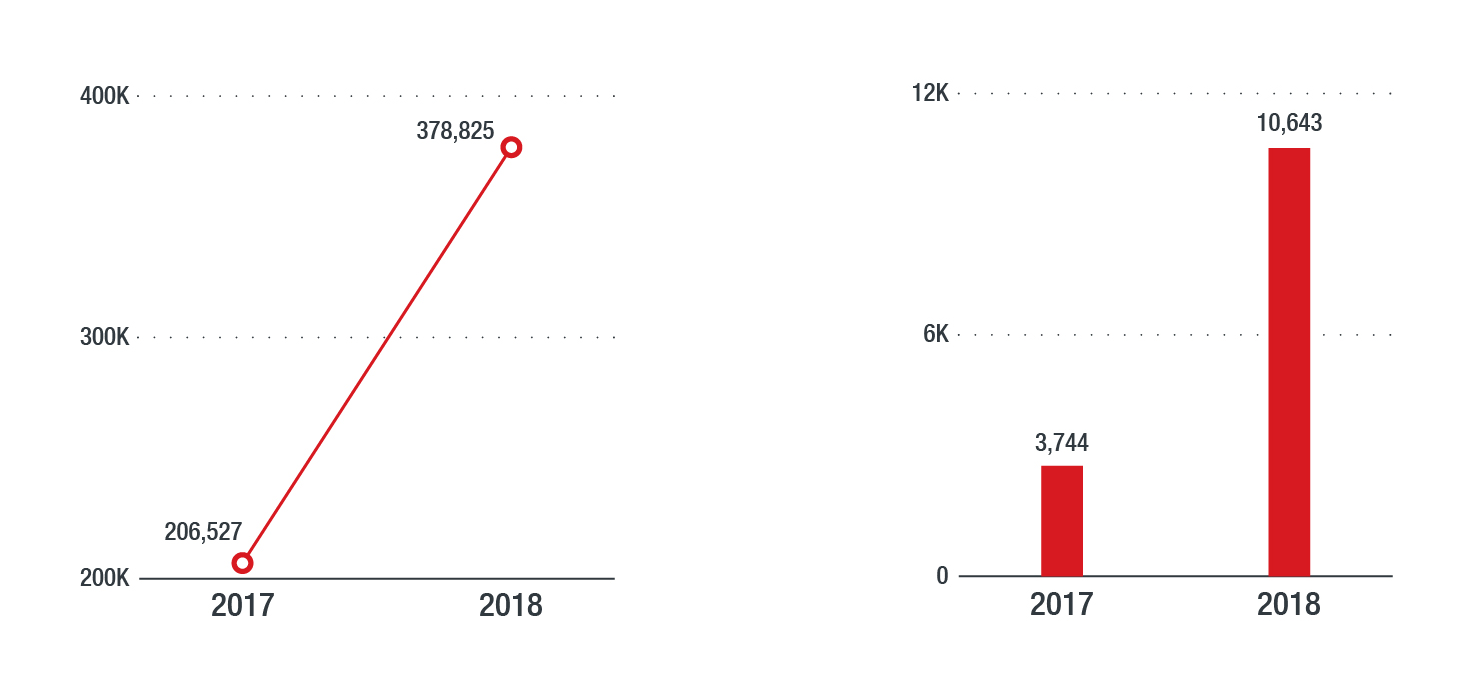
A report by Trend Micro researchers focuses on the Powload threat, and how far the trojan has gone since it was first discovered about a year ago. In fact, the report places Powload at the epicenter of the macro malware distribution action this past year, delivering payloads such as Emotet and Ursnif, and getting empowered by new techniques that allow it to bypass security layers and achieve infection nonetheless. From file-less methods to using steganography in document preview mode, and from hijacked email accounts to massive scale spamming, Powload has evolved into being one of the most pervasive threats right now.
source: blog.trendmicro.com
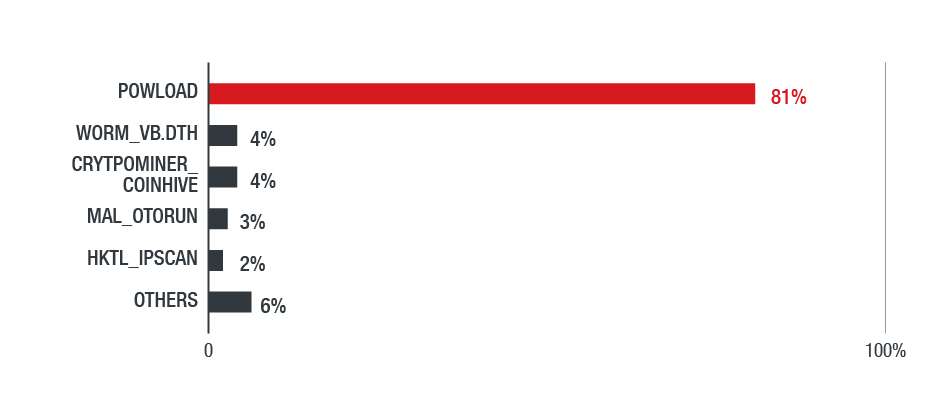
According to the analysis findings of the most recent Powload samples, the threat has not grown into a more persistent, but also a more targeted one. Predominately, Powload is focused on the North American region and is mainly delivering information stealers which are the top infection problem at this time. More specifically, it accounts for 81% of the total malicious payload distribution tools that were used to infect systems in North America in 2018. This means that Powload is utilized in 4 out of 5 attacks!
source: trendmicro.com
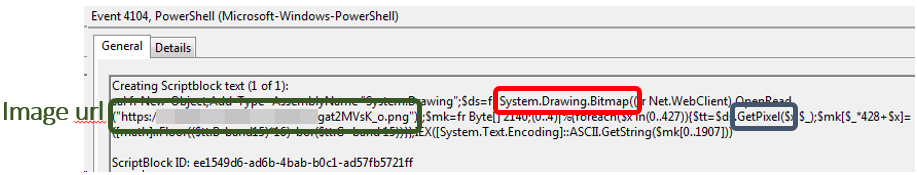
Proceeding further, Powload is now using steganography (malicious code hidden in an image) after executing PowerShell scripts that download the images, and then acquires the code that is hidden inside to proceed through the various steps of the infection chain. While no significant evolution in the routines has been noticed, in some cases, there has been the addition of another stage that helps evade detection.
Even the composition of the spam emails content that reaches the potential victims has been refined over time. Trend Micro researchers have noticed the use of region-specific vocabulary, which can greatly increase the persuasive power over the recipients, as well as trick the lesser spam email filtering systems. What is also interesting is that Powload uses a set of methods to determine the system’s location, like the “Get-Culture” PowerShell command, the value of the xlCountrySetting property, or the IP address.
source: blog.trendmicro.com
As the report points out, it doesn’t really matter if a threat is old or new, but whether it is actively developed and improved. In the case of Powload, we are dealing with an especially persistent threat that has evolved to become better and more versatile against threat detection tools, with the numbers indicating a clear prevalence. To protect against email-based attacks, use a sandbox to open attachments from untrusted sources, configure denser email spam filters, disable macros in the office suite, and use an email security gateway product.
Care to share your thoughts on the above? You may do so in the comments section beneath, or on our socials, Facebook and Twitter.