Post Office Phishing Campaign Targets People in 26 Countries
- There’s a large-scale phishing campaign impersonating the post office services of 26 countries.
- The actors send something relevant to an item that cannot be delivered and ask the recipient to take action.
- The victim is then taken to a phishing page where they are requested to enter their credit card details.
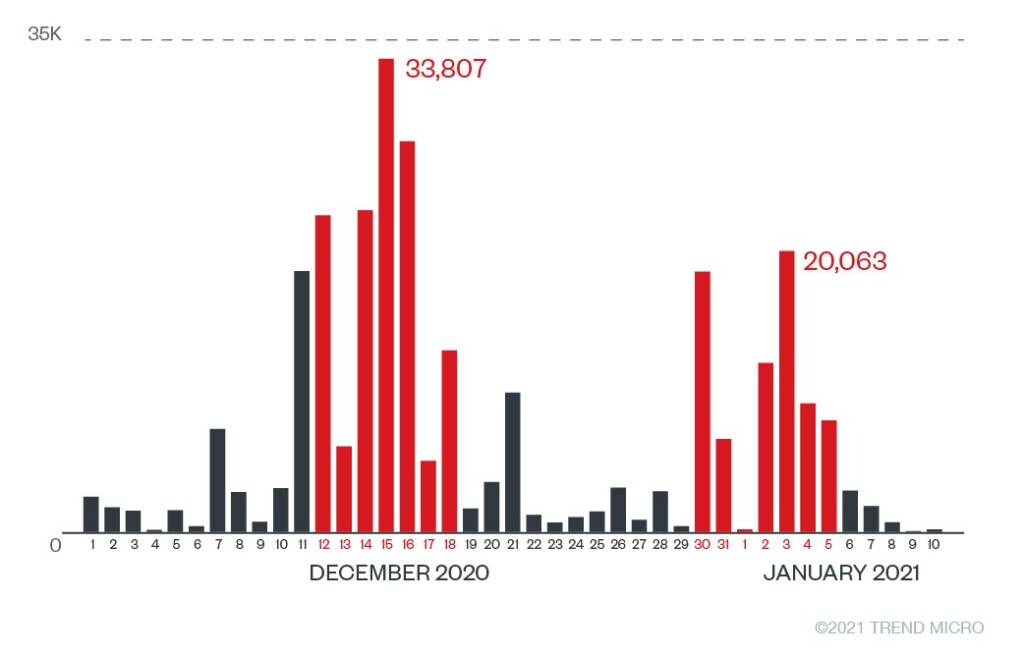
Researchers from Trend Micro have been following a widespread phishing campaign that targets users from at least 26 countries, using emails that pretend to come from their national post offices. According to the shared stats, about 280,000 emails of this kind have been distributed between December 1, 2020, and January 10, 2021.
The actors attempted to take advantage of the holiday shopping spree that was further amplified by the lockdowns. This is similar to what we’ve seen by other phishing groups at the start of last December, sending emails that pretended to come from shipping companies.
The list of the affected countries and the spoofed post offices are the following:
- Australia: Australia Post
- Netherlands: PostNL
- Brazil: Correios Post
- New Zealand: New Zealand Post (NZ Post)
- Canada: Canada Post
- Philippines: PHL Post
- Chile: Correos de Chile (aka CorreosChile)
- Portugal: Correios de Portugal (Portugal CTT)
- Finland: Posti
- Singapore: Singapore Post
- France: Chrono Post
- Slovakia: Slovakia Post
- Germany: Deutsche Post
- Sweden: Post Nord
- Hong Kong: Hong Kong Post
- Switzerland: Swiss Post
- Ireland: An Post
- Taiwan: Chunghwa Post
- Israel: Israel Post
- Turkey: Posta ve Telgraf Teşkilatı (PTT)
- Japan: Japan Post
- UK: Post Office
- Korea: Korea Post
- United Arab Emirates: Emirates Post
- Malaysia: Malaysia Post
- US: United States Postal Service (USPS)
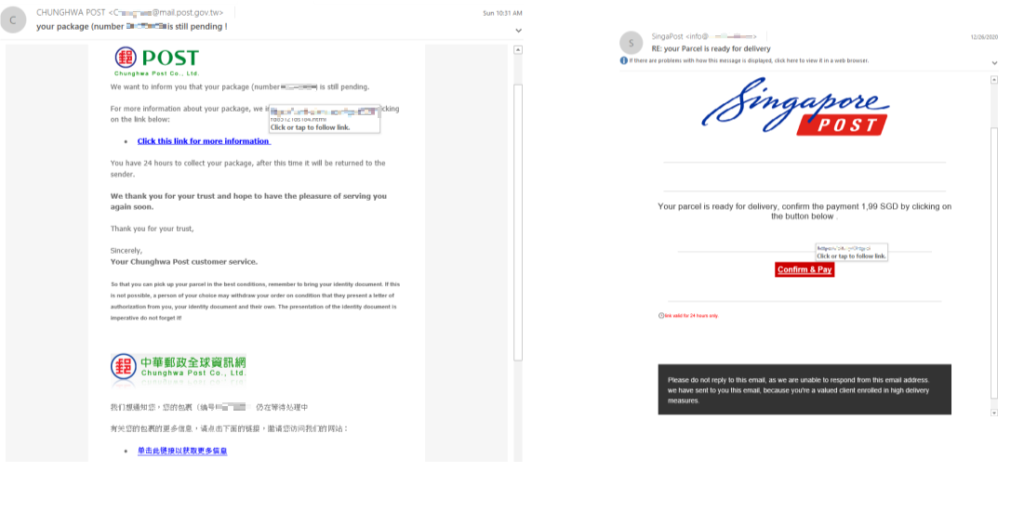
The messages typically contain the keyword “your package,” and the headlines mention something relevant to delivery failure, pending delivery, inability to locate the recipient, shipping notification, last reminder, etc. So, all of the messages are attempting to create a sense of urgency for the recipient and set the ground for action.
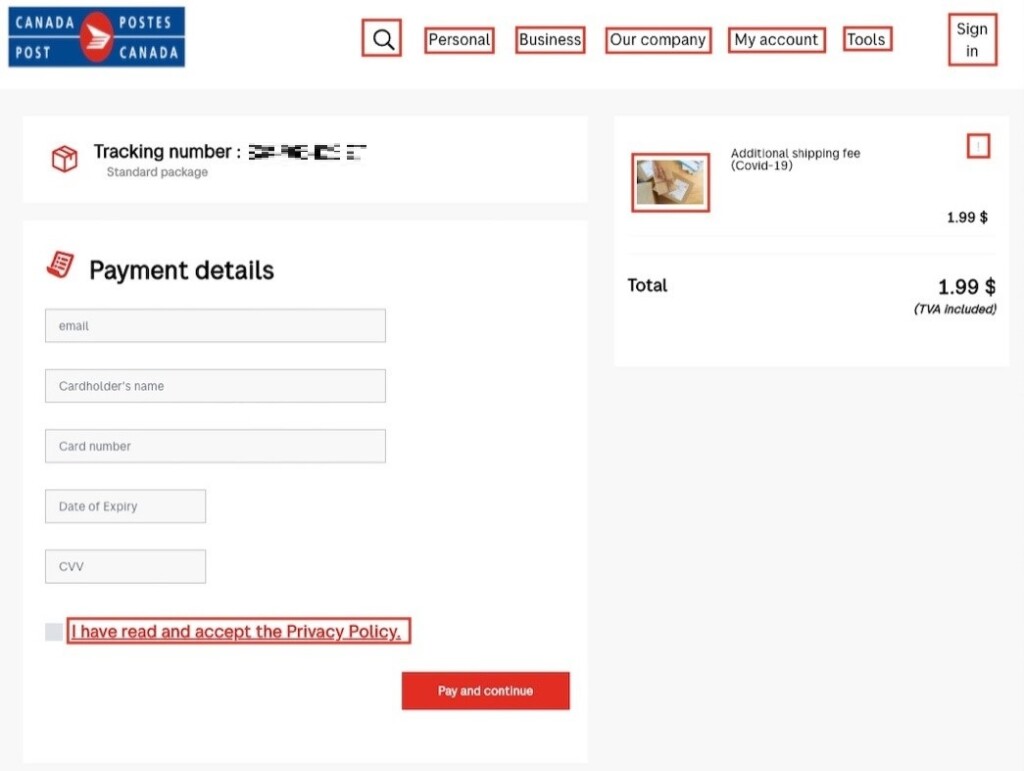
That action is to give away sensitive personal details like the credit card data, for example, which is supposedly needed for the delivery of the item. The phishing page where the victim lands if they click on the button/link that’s embedded on the message body is attempting to continue the impersonation of the post firm through the use of logos.
Up to a point, it manages to reach a convincing result. If the visitor starts clicking on other links on that website, though, they will quickly realize that nothing works, so the page is clearly a scam.
To avoid getting tricked by phishing campaigns of this kind, practice keeping your composure and treat all incoming communications with a suspicious mind. Do not jump on pages through links or buttons contained on emails, do not enter sensitive information on forms willy-nilly, and carefully inspect both the message you’re reading and the website you are on. Usually, there are several tell-tale signs to indicate that you’re dealing with fraudsters.