Popular MFA Keys Vulnerable to Side-Channel Attacks
- Some of the most widely-used MFA keys are vulnerable to a novel electromagnetic wave attack.
- This could result in the derivation of the ECSDA key, making the cloning of the key possible.
- The attacks require physical access, opening up the key, and using specialized and expensive equipment.
A recently released security report compiled by researchers V. Lomme and T. Roche details how a novel side-channel attack against widely-used MFA keys would work out. Side-channel attacks are typically exploiting the flow of information stemming from an indirect source or subsystem, translating it to the “useful target” - like the decryption key, for example.
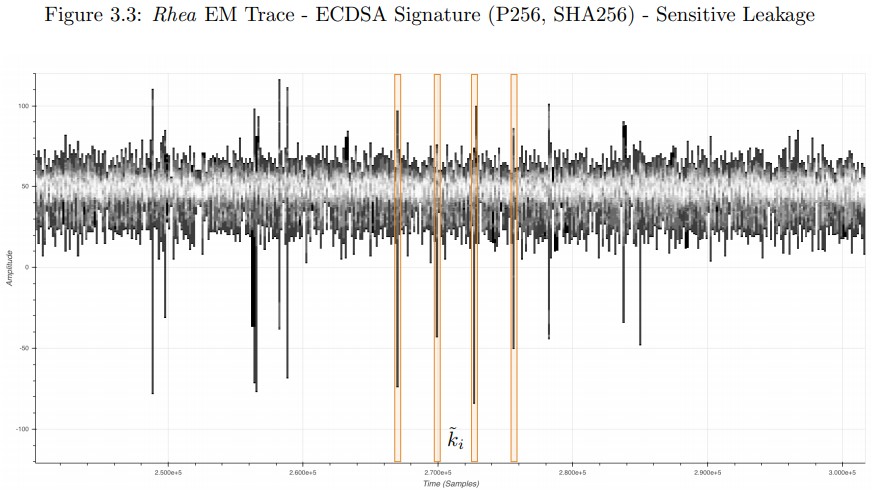
In this particular case, it would be the ECDSA (Elliptic Curve Digital Signature Algorithm) private key, which is exactly what could be used for the creation of a cloned MFA key.
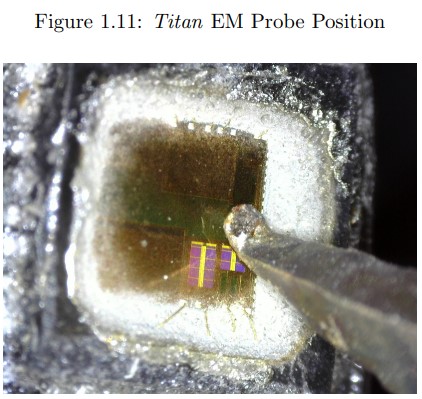
The vulnerability that is exploited for this attack has been given the identifier “CVE-2021-3011,” and the side-channel element is an electromagnetic wave. The target, and point of vulnerability, is the NXP A7005a chip, which is the main microcontroller that controls thousands of operations inside these keys.
The devices that are using the particular chip are the following:
- All EU and US versions of the Google Titan Security Key
- Yubico Yubikey Neo
- Feitian FIDO NFC USB-A / K9
- Feitian MultiPass FIDO / K13
- Feitian ePass FIDO USB-C / K21
- Feitian FIDO NFC USB-C / K40
- NXP J3D145 M59 and variants
- NXP J3E145 M64 and variants
- NXP J3D081 M59 (and DF) and variants
Before you throw away your MFA key, you should note that an attacker would need special knowledge (relation between electromagnetic radiation and cryptographic operations processing), custom software, and expensive equipment to pull this attack off. Of course, the very key would need to be in possession of the attacker, too, so we’re talking about a physical act here. That said, if your Yubikey stays in your pocket, you have nothing to fear.
As the researchers detail, one would have to actually open the device to access the NXP A7005a microcontroller, so even if someone “borrows” your key, the marks left from the opening of its casing would make the fiddling pretty obvious. These keys are pretty hard to cleave in most cases, so there’s no discreet way of pulling this off.
This moderate attack potential has convinced the vendors not to do much on the mitigation front, so while the bug was accepted and acknowledge, there are no plans about it. Also, because the issue is not on the vendor’s side, there were no bounty rewards approved for the reporting of the issue.
Finally, in the case of the Titan keys, Google’s FIDO U2F counters would recognize cloned devices anyway, so even successful attacks wouldn’t yield anything useful for the actors.