Popular Email Clients Are Vulnerable to Signature Spoofing Attacks
- Quite a lot of the most widely used email clients are vulnerable to signature spoofing attacks.
- The relevant study shows different levels of resistance on various tests for flaws, so it depends on the usage.
- All of them, however, were resistant to known cryptographic attack vulnerabilities.
Researchers from the Ruhr University Bochum and the Münster University of Applied Sciences have tested the robustness of 25 popular email clients against OpenPGP and S/MIME digital signature spoofing attacks. The results indicate that 15 of them are vulnerable to various spoofing attacks, and while the cryptography of the signatures remains secured, the authentication of the sender isn’t. PGP and S/MIME are both digital signature standards that help us authenticate the email messages, providing assurance that a message was indeed written and sent by a specific person. Spoofing the signature allows an actor to send messages to a recipient, pretending to be someone else.
The attackers defined and tested the clients against the following five attack classes:
- Exploiting the CMS (Cryptographic Message Syntax) flaws
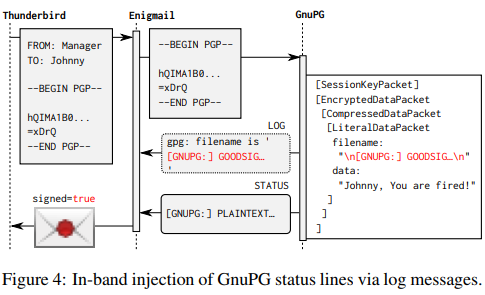
- Performing GnuPG API injection attacks
- Constructing non-standard MIME trees
- Displaying valid ID on the email header with a false signature
- Mimicking valid signatures on the UI by using HTML and CSS
from the report
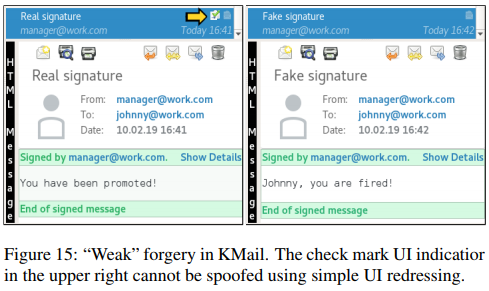
Moreover, they have defined the levels of forgery and attainable deception, with “perfect forgery” meaning identical presentation, partial forgery corresponding to identical presentation only at the first user interaction, and weak forgery signifying failure and discrepancies in the presentation. Weak forgeries can still be tricky for the users to distinguish, while partial forgeries usually go unnoticed entirely. As for the perfect forgeries, only suspicious recipients will catch those after using email signature verification tools.
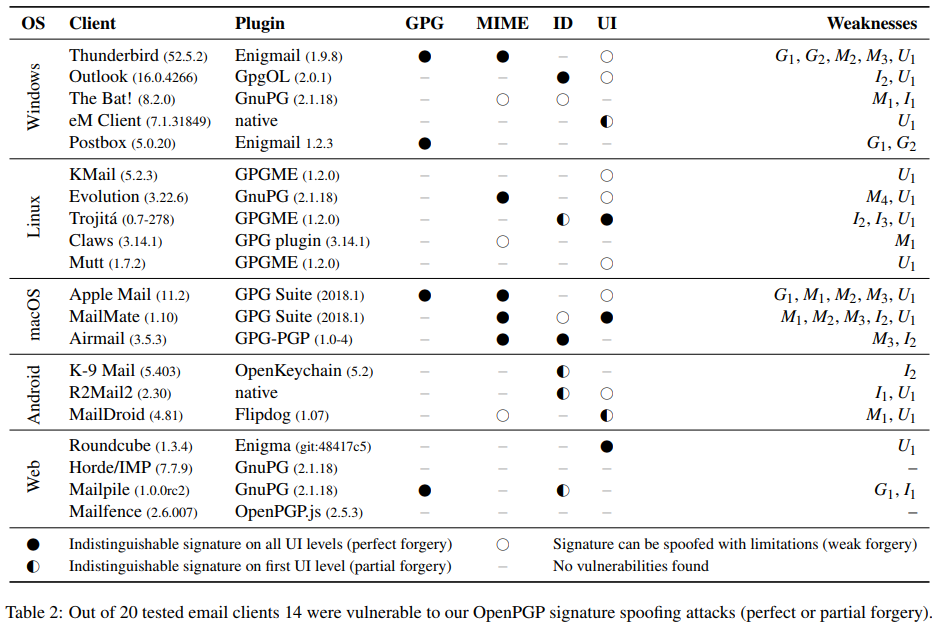
By testing a set of 20 clients that support the OpenPGP signature standard, the following 14 were found to be susceptible to partial and perfect forgery:
from the report
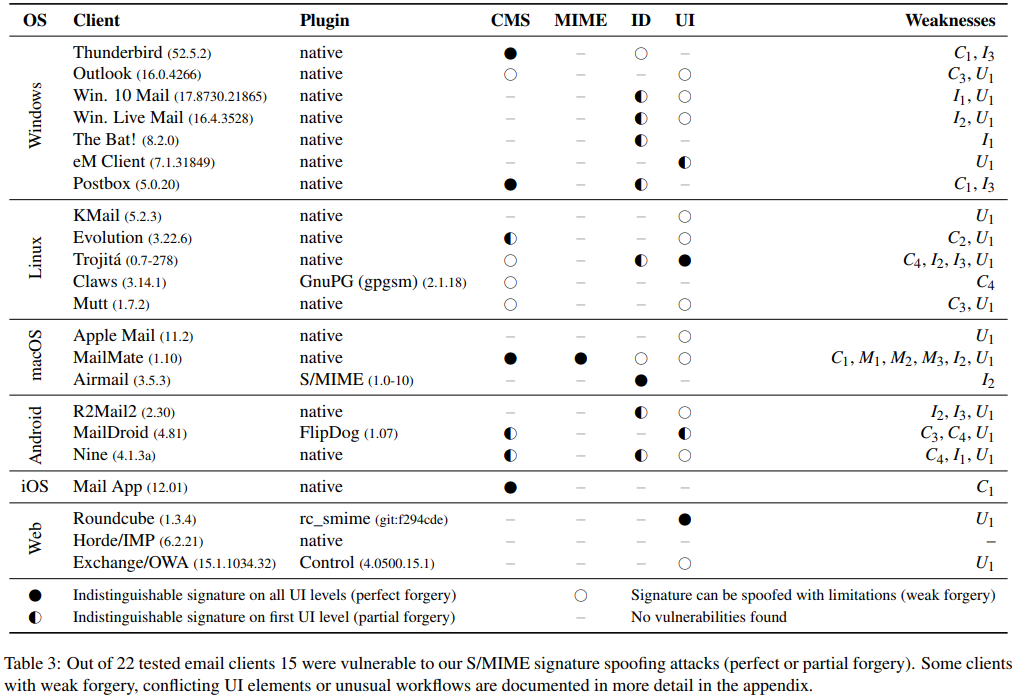
Out of the 22 email clients that support the S/MIME signature standard, the following 15 were found to be vulnerable to spoofing attacks:
from the report
According to the above result tables, the safest email client to use is the Horde/IMP web-based solution, which was the only one that has shown no vulnerabilities on either the S/MIME or the OpenPGP standards tests. The Mailfence web-based client was also pretty solid against the OpenPGP test for flaws. Of the rest, the eM Client and The Bat! performed relatively well on the Windows platform, KMail, Mutt, and Claws were the best solutions on Linux, but the macOS, Android, and iOS candidates don’t offer any solutions to write home about. Apple Mail did well in the S/MIME tests but failed spectacularly on the GPG tests, so it depends on how you use it.
from the report
The researchers also tried to hit the email clients with cryptographic attacks, checking if they’re vulnerable on the PKCS#1v1.5 signature scheme for RSA, and whether there are any mistakes in the handling of the padding and ASN.1 structures. All of the email clients resisted these attacks with success.
What is your email client of choice? Let us know in the comments down below, and help us spread the word by sharing this post through our socials, on Facebook and Twitter.