Phishing Attack Uses Invisible Characters in Email Subject Lines to Bypass Filters
- Novel Evasion Tactic: A sophisticated phishing technique has been identified that uses invisible Unicode characters in email subject lines.
- MIME Encoding Abuse: Attackers leverage MIME "encoded-word" formatting, splitting the subject into Base64-encoded parts to bypass security filters.
- Security Blind Spot: The technique evades automated detection systems that primarily focus on keywords, since the subject line appears normal to the end user.
Security researchers have identified a sophisticated phishing method that weaponizes invisible characters in email subject lines to bypass automated security filters. This Unicode phishing evasion technique involves embedding soft hyphens (Unicode character U+00AD) throughout the subject text.
Fragmentation, combined with invisible characters, poses a significant challenge for many current email security threat detection engines.
How MIME Encoding Facilitates the Threat
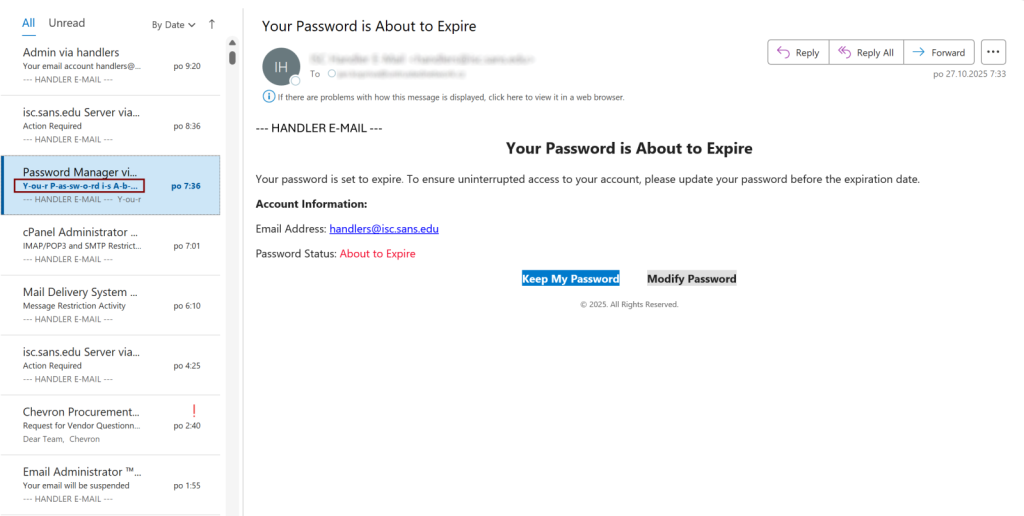
The analyzed phishing campaign debuts with an email purporting that the recipient’s password is about to expire, creating a sense of urgency. The link inside the message led to a generic Webmail login page designed to steal credentials.
This attack's effectiveness relies on the abuse of MIME encoding phishing tactics. According to RFC 2047, email headers can use an "encoded-word" format to handle non-ASCII characters. Attackers are exploiting this by splitting the subject line into multiple Base64-encoded segments, SANS Technology Institute said in a recent report.
Each segment contains parts of the text interspersed with soft hyphens, which are also present in the email body. When an email gateway scans the raw header, it sees a series of seemingly random encoded strings rather than a cohesive, malicious phrase.
While these characters are not rendered in most email clients like Outlook, they effectively break up keywords and signatures that security solutions are designed to detect. The end-user sees a normal, readable subject line, but the underlying code is fragmented, allowing the malicious email to slip past defenses.
Implications for Email Security and Defense
The use of invisible characters in subject lines, while previously noted as a theoretical possibility, represents an uncommon and evolving evasion strategy. This method highlights a potential blind spot in security systems that may not perform deep analysis on MIME-encoded headers or properly interpret Unicode characters used for obfuscation.
To counter this phishing attack with invisible characters, security administrators must ensure their filtering policies can decode and analyze the content of MIME-encoded headers thoroughly.
Implementing more advanced content analysis capable of recognizing such obfuscation is critical to defending against this and similar emerging threats.
Other recent malicious campaigns that started with phishing emails include the Western Sydney University data breach, which led to attackers attempting to steal data from students, and a social engineering operation targeting Japanese users with fake business inquiries to deliver MostereRAT.
Earlier this year, a Cisco Talos report said that hidden text salting phishing techniques saw a surge in the previous months.