Phishing Actors Return to ‘Good Old’ Morse Code for Obfuscation
- Microsoft noticed the use of Morse code in a year-long phishing campaign that went through several method changes.
- The actors tried many things to evade detection and increase their success rates, but Morse code wasn’t very effective.
- Simply setting HTML files to be stripped in your inbox policies would render these phishing efforts impotent.
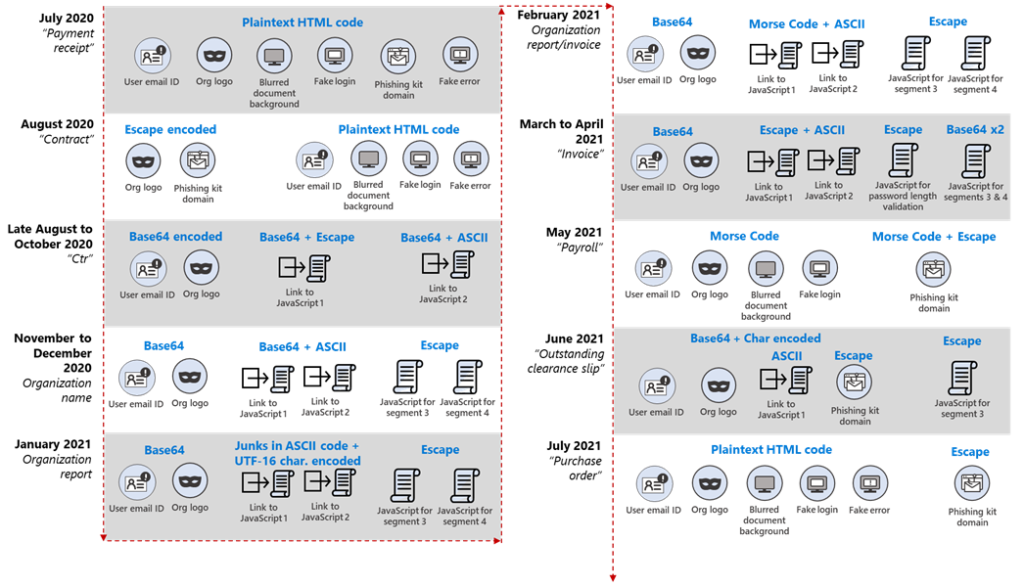
It appears that phishing actors rotate their encryption and obfuscation methods so frequently that passing through some classics like using Morse code is inevitable even if it has been proven to be largely ineffective multiple times in the recent past. As Microsoft’s Threat Intelligence team reports, phishing campaigns change tricks every 37 days on average, testing out new obfuscation methods and evaluating them based on the success rates against the targets. Microsoft followed a particular campaign from July 2020 to July 2021, recording the following evolution in the actors’ methods.
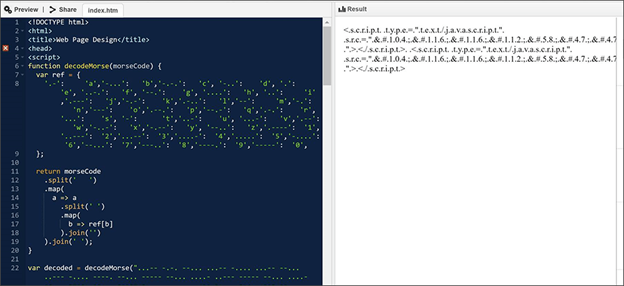
The use of Morse code first appeared in February 2021 and then returned for a second run in May 2021. Morse code is an old Latin text encoding method that uses dots and dashes, appreciated for its simplicity and reliability in telecommunications, aviation, radio, assistive technology, navigation, and other special cases. In computing, though, it is pretty unusual as it’s neither efficient nor very effective. The phishing actors still gave it a try twice, encoding their JavaScript in February in ASCII and then Morse, while in May, they went straight from HTML to Morse.
Apart from the actual phishing that typically involved the abuse of Office 365 logos and login prompts, the actors also delivered an info-stealing module starting in May 2021, which was capable of fetching credentials automatically, as well as the user’s IP address and country data. In some cases, Microsoft noticed the actors using the organization's logo the target worked for, so there was clearly some level of reconnaissance operations involved, too, depending on the perceived value of the victim.
On the matter of the success that this campaign had in the wild, it is obvious that Microsoft could follow it closely. Hence, the actors never really managed to fly under the radar no matter how many times they tried to bypass detection systems. The Defender for Office 365 checks the email header properties, the sender’s IP address reputation, “detonates” files and URLs in its built-in sandbox, and tests JavaScript files on the fly in a contained environment. As such, no matter the obfuscation, Defender’s checks will determine what is spoofed and what’s legitimate.
To stay safe against these attacks, set your mail flow rules or Group Policy for Outlook to strip .HTML and .HTM file types that aren’t required for business anyway, turn on “Safe Attachments” and “Safe Links,” and finally activate 2FA on your account.