Pharmaceutical Company “Pfizer” Leaked Private Client Data
- “Pfizer” exposed private U.S. customer data after misconfiguring a Google bucket for public access.
- The details that have been leaked online are highly sensitive and could be used for phishing.
- Pfizer didn’t move too quickly and only secured the bucket 45 days later, so hackers may have accessed it.
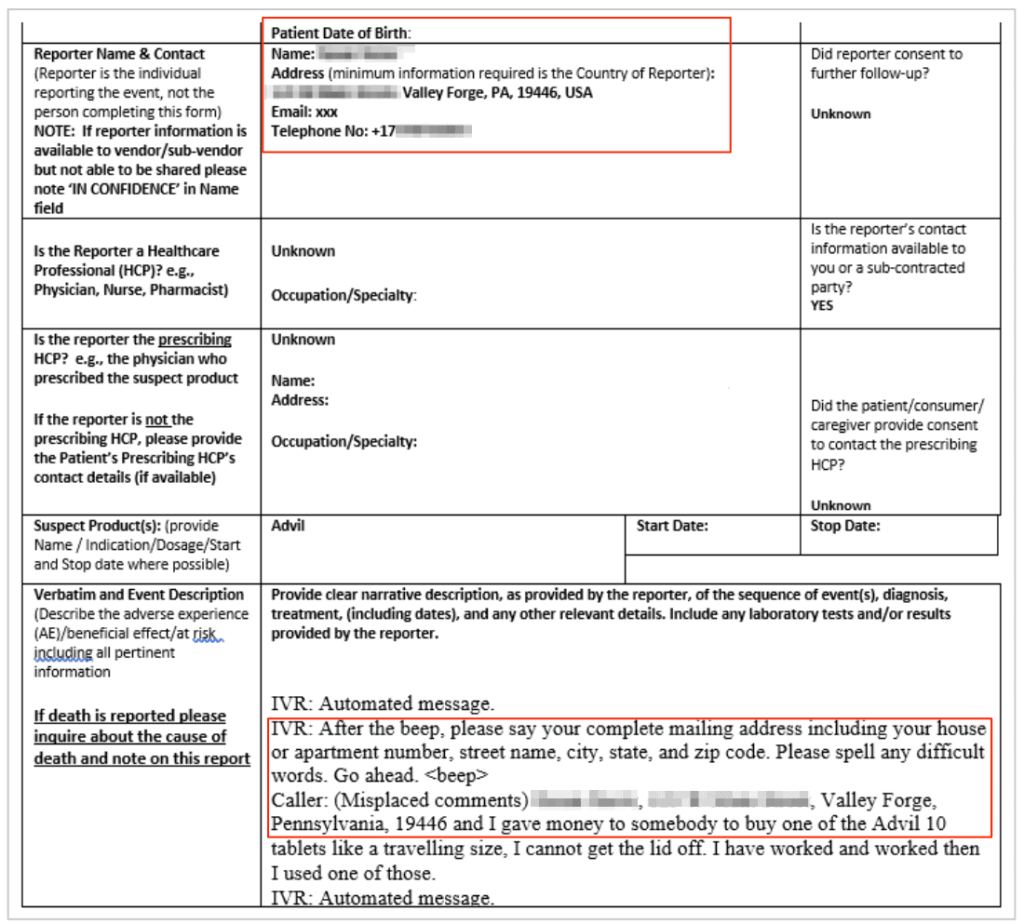
Pfizer, one of the largest pharmaceutical companies in the world, has made a critical mistake in the configuration of one of their buckets and left it accessible by anyone with a web browser. This “typical” error has severe implications for the exposed people’s privacy as the particular bucket contained prescription drug details, full names, home addresses, email addresses, phone numbers, and some details on their medical status.
The discovery of this bucket was made by researchers N. Rotem and R. Locar on July 9, 2020. The vendors were contacted four days later but failed to respond. The researchers sent a new notice on July 19, 2020, and then a third one on September 22, 2020. Pfizer finally responded to the third notice and took action to secure the bucket on September 23, 2020, so the total period of exposure was at least 45 days.
Further Reading: How Long Before Hackers Scrape AWS Credentials on Public GitHub Repos?
The transcripts that were exposed along with the data mentioned above concern the following drugs:
- Advil: an anti-inflammatory and pain relief medicine
- Aromasin: an anti-estrogen used to fight breast cancer.
- Chantix: treatment for nicotine addiction.
- Depo-Medrol: a medicine used in a huge number of treatments for skin diseases, certain cancers, asthma, and much more.
- Ibrance: used in treatment for breast cancer.
- Lyrica: medication for epilepsy, neuropathic pain, fibromyalgia, restless leg syndrome, and generalized anxiety disorder.
- Premarin: Primarily used in menopausal hormone therapy.
- Viagra: Used to treat erectile dysfunction and pulmonary arterial hypertension.
This information is key for scammers and phishing actors. There are entire conversations between Pfizer customer support agents and the clients who called them, with the PII mentioned right there on the same files. All that said, the exposure is dire and introduces a wide spectrum of potential malicious exploitation scenarios.
If you have contacted Pfizer about any of the above drugs, you should contact them again to ask about whether this incident has impacted you or not. If you receive any emails, calls, or SMS claiming to come from Pfizer, be very cautious as it could be scammers attempting to phish you.