Phantom Taurus APT and NET-STAR Malware Espionage Campaign Targets Government and Telecom
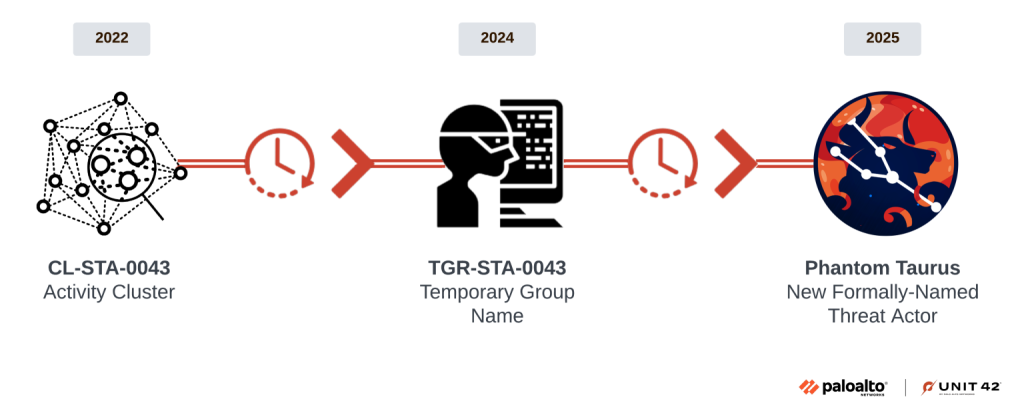
- Newly discovered: Phantom Taurus, a previously undocumented nation-state APT group, was linked to Chinese state interests.
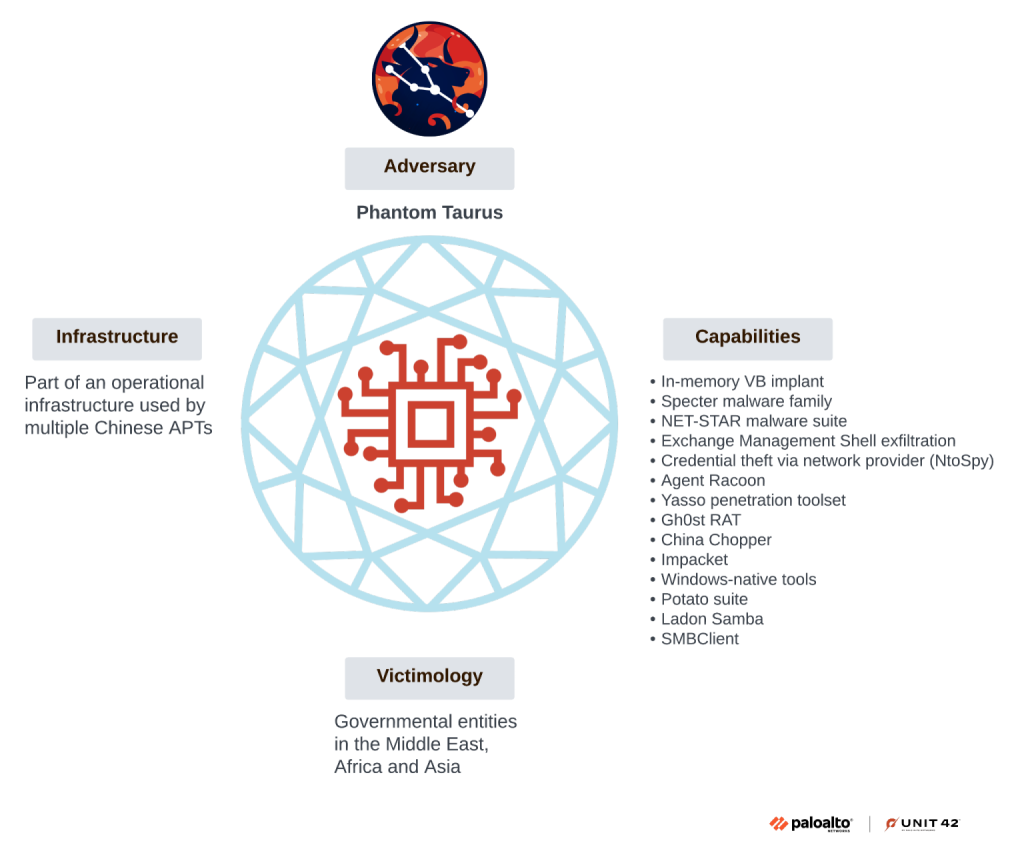
- Espionage focus: The group spies on high-value government and telecommunications organizations across Africa, the Middle East, and Asia.
- Novel malware suite: Phantom Taurus employs a new, custom .NET malware suite that creates persistent backdoors on IIS web servers.
A new nation-state threat actor, Phantom Taurus, is conducting cyberespionage operations primarily targeting government ministries, embassies, and telecommunications providers, with a focus on diplomatic communications and military operations that align with the geopolitical objectives of the People's Republic of China (PRC).
Over the past two and a half years, this group has conducted highly covert, long-term intelligence-gathering campaigns, according to Palo Alto’s Unit 42.
The NET-STAR Malware Arsenal
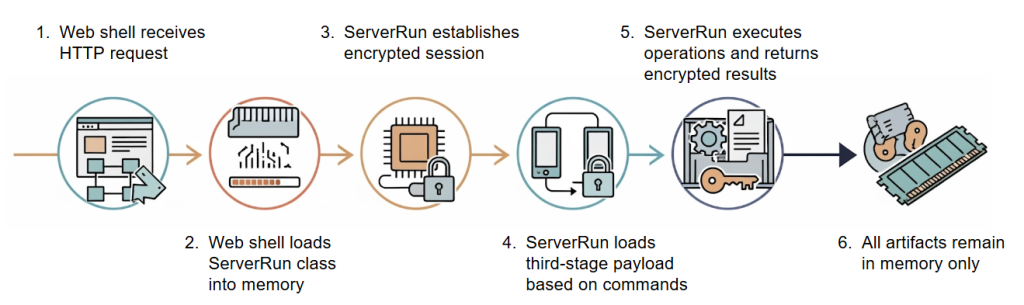
A key component of the Phantom Taurus APT operations is the previously undocumented NET-STAR malware suite, Unit 42 researchers have found. This toolkit is specifically designed to compromise and maintain persistence on Microsoft IIS web servers.
The suite consists of three primary components:
- a modular, fileless backdoor named IIServerCore
- two variants of a .NET loader called AssemblyExecuter
IIServerCore operates entirely in memory, allowing it to execute payloads and commands while evading detection.
The more advanced version of AssemblyExecuter includes capabilities to bypass Windows security features, such as the Antimalware Scan Interface (AMSI) and Event Tracing for Windows (ETW).
“By combining in-memory malware with living-off-the-land techniques (abusing legitimate tools like WMI for internal movement), threat actors can conduct espionage operations with long dwell times,” said Lauren Rucker, Senior Cyber Threat Intelligence Analyst at Deepwatch.,
Tactical Evolution and Cybersecurity Implications
The Phantom Taurus group has demonstrated an evolution in its tactics, recently shifting from email-centric attacks to direct targeting of SQL databases for data exfiltration. The use of custom, fileless malware and advanced evasion techniques highlights the growing sophistication of Chinese cyberespionage actors.
“Observing and monitoring the malicious actors better informs what they’re after, the tools, techniques, and procedures being used by those actors, and to evaluate if there are upstream opportunities to disrupt these networks,” said Trey Ford, Chief Strategy and Trust Officer at Bugcrowd.
For this specific campaign, Rucker recommends the following mitigation steps:
- Minimize IIS server footprint by removing unused modules, run web applications with unique, low-privileged accounts, and maintain rigorous patch management.
- Prohibit the use of shared administrative accounts (e.g., sa) for applications. Restrict database access to only authorized application servers via strict firewall rules and monitor for unusual query volumes or data exports.
- Use host-based firewalls to block remote WMI and PowerShell access from web servers to internal systems where possible.
- Enable enhanced logging for PowerShell (Script Block Logging) and WMI activity, forwarding these logs to a SIEM for analysis.
- Actively search for anomalous process chains, such as cmd.exe being spawned by the WMI provider host (WmiPrvSE.exe), which is a key indicator of WMI-based lateral movement.
- Create behavior-based rules to alert on suspicious WMI usage and use YARA rules to find artifacts of fileless malware.
Cybersecurity organizations must leverage threat intelligence to rapidly identify adversary tactics and translate them into actionable indicators of compromise, recommends Louis Eichenbaum, Federal CTO at ColorTokens.
“Given the speed and sophistication of modern attacks, automation and AI must play a central role,” said Eichenbaum, highlighting the need for building resilience into networks “from the ground up, starting with strong cyber hygiene practices.”
“Implementing effective endpoint detection and response (EDR) solutions and closing unnecessary ports on endpoints is key”, Eichenbaum added.
Among other fileless campaigns seen this year is a sophisticated RokRat Campaign launched by the North Korean APT-C-28 group.