The “PerSwaysion” Phishing Campaign Is Targeting High-Rank Executives
- A new phishing campaign is working impressively well and moves quickly, targeting company executives.
- The malicious actors are abusing Microsoft Sway to create convincing Office 365 sharing pages.
- Already, 156 members of high-level management have given away their email login credentials.
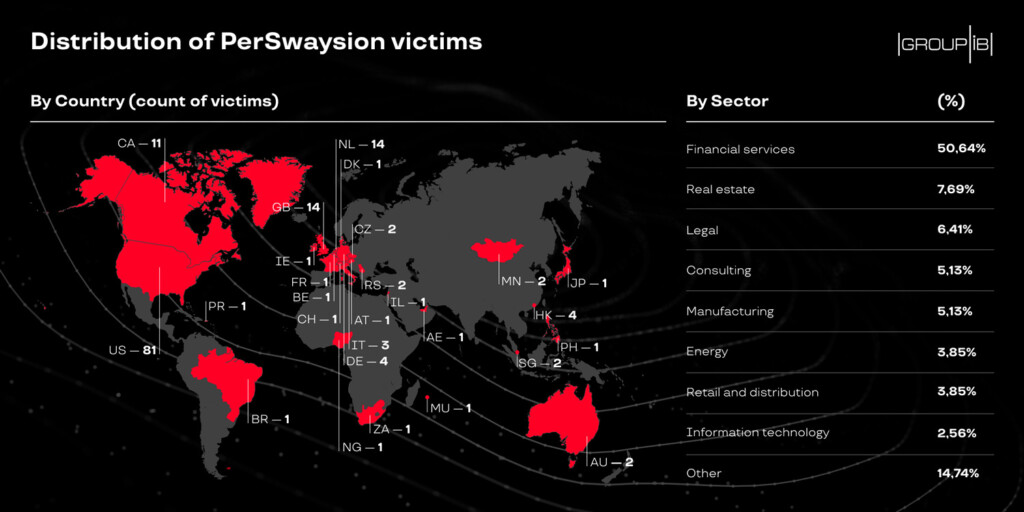
Called “PerSwaysion” due to the extensive abuse of Microsoft Sway, this highly-targeted phishing campaign has been discovered by Group-IB, and it looks like this is one of the most effective campaigns of its kind. The Singaporean cybersecurity company believes that “PerSwaysion” has been going on since at least mid-2019, while they have seen some connection with Vietnamese, South African, and Nigerian hacking groups. The actors use compromised email accounts to engage in BEC operations against targets who hold important positions in the companies where they’re employed. As for the industries that are targeted, these are mainly law firms, real estate companies, and those offering financial and consultation services.
Source: Group-IB
There’s no malware planting involved, as everything happens purely through emails and phishing pages, so the threat is jumping from one target to the next pretty quickly. Group-IB says the actors are so skillful at this, that they usually need less than 24 hours to carry out a new phishing round based on the credentials they harvested in the previous one. It total, 156 high-rank executives were compromised by PerSwaysion, setting the ground for supply-chain attacks against the clients and contractors.
In one of the presented examples, the actors are sending a non-malicious PDF email attachment to the companies’ executives from a compromised email account. The message is short, and the notification is created in MS Sway, crafted in a way that it looks like an authentic Microsoft Office 365 file-sharing page. In reality, the actors are using a presentation slide, abusing the “borderless view” feature to hide this fact from the recipients. After clicking on the “Read Now,” victims are taken to the phishing page, which is a spoofed Microsoft Single Sign-On page. If the victim tries to visit the same URL, they will be barred, as there’s a unique serial number on the phishing kit allocating a single access token to each target.
Source: Group-IB
Group-IB says this method works so well that the threat is spreading like wildfire right now. To speed up the malicious operation, the actors dump any newly acquired credentials via API, establish the business connection, and then generate new phishing PDF files with all details included (names, emails, company name).
The cybersecurity firm has already informed the affected companies of the compromise that their executives suffered and advised them to enforce 2FA authentication steps. If your company is using cloud services, you should take every possible action to mitigate the risks of login credential theft, as the consequences could be dire.