Payroll Fraud: Direct Deposit Attacks Target Payroll Systems Like Workday via Social Engineering
- Attack Vector: Cybercriminals use social engineering to trick IT help desks, resetting employee passwords and MFA to gain account access.
- Primary Objective: Attackers infiltrate payroll platforms to alter direct deposit information, redirecting employee salaries to accounts they control.
- Evasive Methods: Threat actors often leverage a company's virtual desktop infrastructure (VDI) to masquerade as legitimate internal users, thereby bypassing many security detection tools.
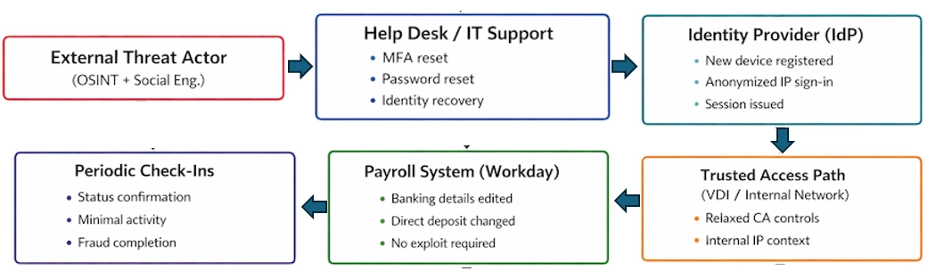
A new trend in financially motivated cybercrime is emerging, as attackers focus on direct deposit attacks that exploit human trust and internal business processes. Security researchers have identified a precise, low-noise attack method in which criminals impersonate employees, often feigning urgency, to convince IT help desk staff to reset account credentials and multi-factor authentication (MFA) tokens.
Simple social engineering provides the initial access needed to execute sophisticated payroll fraud. Once account control is established, the path to financial theft is cleared with minimal technical complexity.
Exploiting HR Systems for Financial Gain
After the initial identity takeover, attackers are targeting self-service HR and payroll platforms like Workday. In a recent incident investigated by Binary Defense, an attacker, having successfully reset a user's credentials, logged in through the organization's own trusted virtual desktop infrastructure (VDI).
After the reset, the attacker authenticated multiple times using anonymized IP addresses or VPN infrastructure and registered new authentication devices with the account. Their activity appears as legitimate internal traffic, allowing them to bypass many conditional access policies and security alerts.
Once inside the payroll system, the attacker simply modified the employee's banking details, rerouting their salary to an account controlled by the criminal. The fraud is often only discovered when the legitimate employee reports a missed paycheck.
Cybersecurity for Payroll Platforms Becomes Critical
As attackers pivot from traditional malware to exploiting identity workflows, organizations must treat employee identities as high-value assets. Experts recommend:
- Treating payroll changes as high-risk financial events,
- Elevating identity recovery workflows to the same risk tier as privileged access
- Breaking down visibility silos between security, HR, and finance
A Microsoft Threat Intelligence October 2025 report documented Payroll Pirate campaigns targeting SaaS HR platforms such as Workday to redirect employee paychecks. In August 2025, Baltimore lost $1.5 millions in a Workday vendor scam.