‘Pay2Key’ Ransomware Quickly Passes to the Data-Stealing Extortion Model
- The ‘Pay2Key’ ransomware group has set up a data leak site, and there are three entries there already.
- The actors move against Israeli firms and entities, so it appears that they are Iranians.
- The encryption scheme used by the new ransomware strain is without any obvious flaws.
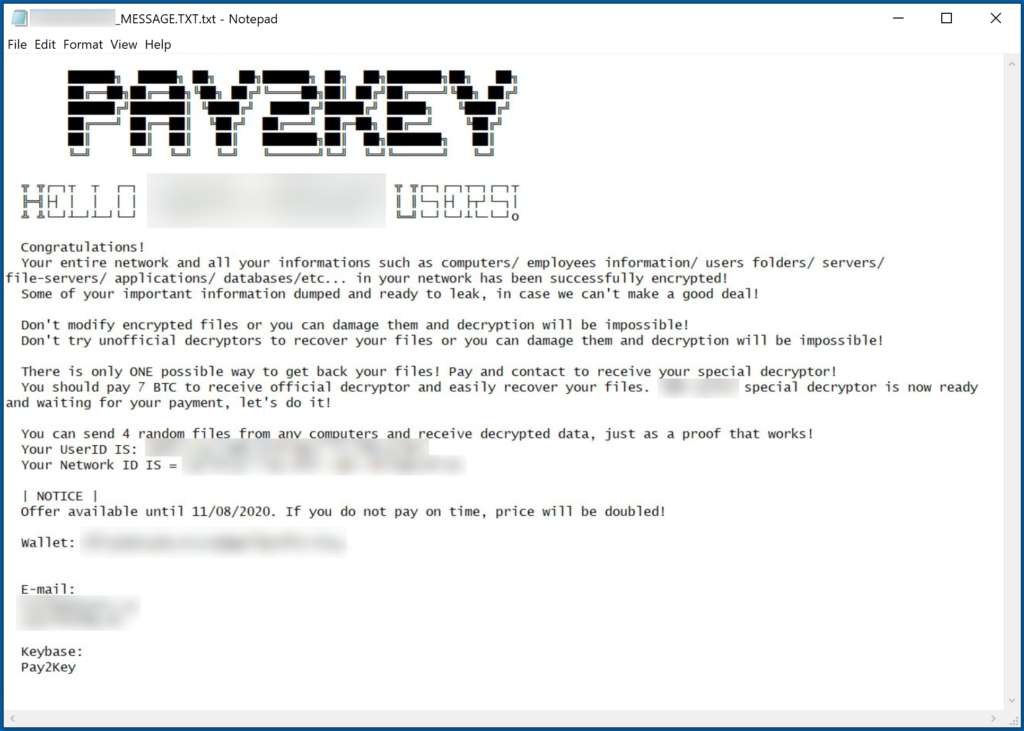
As if the ransomware actors who are engaging in data-stealing extortion operations weren’t enough, we now have ‘Pay2Key’ added to this group. The new ransomware strain has been under the microscope of CheckPoint researchers since the beginning of the month, but the fact that it’s evolving so quickly obliges us to return to it. As Tomas Meskauskas reports now, Pay2Key is now operating a dedicated leak site to publish samples of the data stolen by the victimized networks.
The particular group of actors warned their victims that they were stealing data from their networks since the very beginning of their operation, but since they hadn’t set up a data leak site, these threats could very well be empty. Now, the leak website already has three entries, with one belonging to a law firm and a second one concerning a game development company. Both companies are based in Israel, which matches the early indications that Iranian hackers hide behind ‘Pay2Key’.
However, there is still no concrete evidence that the Pay2Key group is state-sponsored, and the crypto laundering procedure is taking place on “naked” exchanges, so it all seems to be happening for financial benefits. If Pay2Key was state-supported, they would be more focused on collecting information and cyber-espionage, while any money made would pass through better hidden channels.
As for the malware itself, more information about it has surfaced thanks to the ongoing analysis, and it appears to be a strain that was built entirely from scratch. It relies heavily on object-orientated programming methodologies rather than logic functions, it uses several third-party libraries like “Boost”, and makes extensive use of logs. That last part has helped white-hat researchers analyze the malware, so newer versions make an effort to delete the logs.
The encryption scheme used is a hybrid between symmetric and asymmetric, while AES, RC4, and RSA algorithms are deployed using a key supplied by the C2 server. For this reason, the ransomware is not capable of performing offline encryption. So far, the researchers’ analysis hasn’t yielded anything that would make the development of a decryptor possible, and the encryption process of the ‘Pay2Key’ appears to be solidly implemented.