Patch Bypass PoC for Pulse Connect Secure Calls for Emergency Update
- Researcher finds a way to bypass 2020 Pulse Connect Secure mitigation for severe RCE flaw.
- It took the company two months to assess the report and one more month to release a fix.
- The proof of concept exploit is out in the form of a screenshot, but more details will be published soon.
Pulse Connect Secure, the widely deployed business-grade VPN by Ivanti, needs to be updated to version 9.1R12 as soon as possible, as a bypass PoC (proof of concept) exploit for a bug that was fixed last year is already out there. The vulnerability is ‘CVE-2020-8260’, which was thought to affect versions below 9.1R9, allowing an authenticated attacker to perform arbitrary code execution using uncontrolled gzip extraction. However, as researchers at the NCC Group explain, the validations that were added to prevent exploitation can be bypassed.
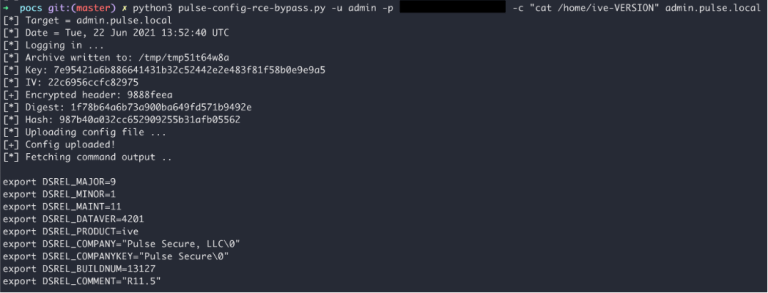
By simply changing a single POST parameter variable in the original CVE-2020-8260 exploit, the extraction vulnerability can be displaced elsewhere (CGI files), so code execution would be achieved on the latest and fully patched Pulse Connect Secure products. As the researcher explains, adjusting the PoC for the 2020 bug to exploit the VPN software today was pretty trivial.
This was discovered and reported to Ivanti on May 12, 2021, through the HackerOne platform. The firm wasn’t quick to respond and confirm the problem, as it took them two months to get back to the researcher’s (Richard Warren) report. The fix eventually landed on August 2, 2021, and now, an advisory to give away some details was published.
Version 9.1R12 addresses a total of six vulnerabilities, all categorized as critical, with the bypass plug being CVE-2021-22937. To clarify, the PoC published by the researcher only shows a screenshot, as it’s too early to give away everything only three days after the patch was made available to users of the product. However, sophisticated actors may have already gotten all they needed to proceed with weaponization, so delaying the update shouldn’t be an option.
Also, it is worth pointing out that an attacker would still need to access an administrator account to exploit this vulnerability, so some form of phishing or credential stuffing must occur beforehand. This somewhat lessens the severity and limits the scope, but organizations shouldn’t rely on that.