PassiveNeuron Cyberespionage Campaign Targets Global Organizations with Custom APT Implants
- Sophisticated implants: The campaign utilizes previously unknown APT implants, including a custom C++ modular backdoor and a .NET implant
- Targeted sectors: Infections have been identified in government, financial, and industrial organizations across Asia, Africa, and Latin America.
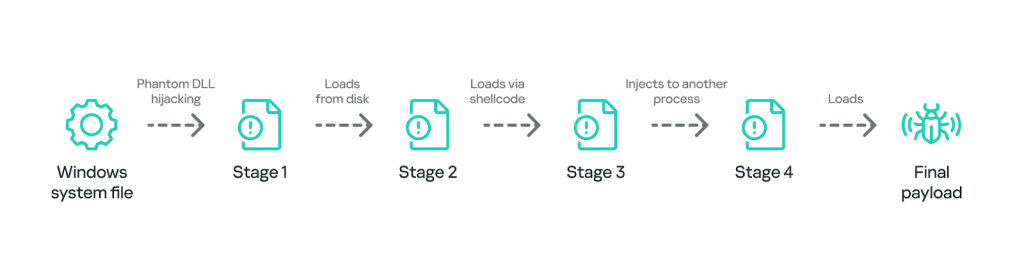
- Complex attack chain: The threat actor uses a multi-stage loading process involving Phantom DLL Hijacking for persistence and artificially inflated DLLs to evade detection.
A complex and sophisticated cyberespionage operation, dubbed the PassiveNeuron campaign, has been actively targeting high-profile organizations since at least 2024. Security researchers have identified new waves of infections occurring as recently as August 2025.
The campaign's primary targets are server machines within government, financial, and industrial sectors.
Technical Analysis of APT Implants
The initial vector of compromise often involves exploiting Microsoft SQL servers to gain remote command execution, followed by attempts to deploy web shells and more advanced malicious tools, according to the latest SecureList report.
Over the last two years, researchers observed three implants used over the course of PassiveNeuron infections:
- Neursite, a custom C++ modular backdoor used for cyberespionage activities
- NeuralExecutor, a custom .NET implant used for running additional .NET payloads
- The Cobalt Strike framework, a commercial tool for red teaming
The campaign is distinguished by its use of custom APT implants and well-known offensive security tools. The attackers deploy a multi-stage loading chain that begins with Phantom DLL Hijacking for persistence, loading an oversized (100+ MB) DLL into legitimate system processes like svchost.exe.
This chain eventually decrypts and executes the final payload. The primary implant is Neursite, a modular C++ backdoor capable of system reconnaissance, process management, and acting as a proxy for lateral movement.
Another custom tool, NeuralExecutor, is a .NET-based implant designed to load additional payloads from a command-and-control (C2) server, retrieving the contents of a file stored in a GitHub repository. Alongside these custom tools, the campaign also leverages the commercial Cobalt Strike framework.
Attribution and Broader Cybersecurity Threats
Attribution for the PassiveNeuron campaign remains challenging, though evidence points toward a Chinese-speaking threat actor with a low level of confidence.
This assessment is based on tactics, techniques, and procedures (TTPs), such as using GitHub as a dead-drop resolver for C2 addresses—a method frequently observed in other Chinese-speaking APT groups.
The focus on server-side compromises highlights significant cyberespionage threats, as these machines often serve as critical entry points into sensitive organizational networks.
The campaign underscores the importance of robust server security, patch management for applications like SQL Server, and monitoring for unusual DLL loading behavior.
In September, security researchers highlighted that a two-month Lunar Spider network intrusion leveraged Latrodectus, Brute Ratel C4, Cobalt Strike, and a custom backdoor.