‘Paleohacks’ Has Exposed the PII of 70,000 of Its Customers
- ‘Paleohacks’ has had a lengthy data leak via an unprotected Amazon AWS S3 bucket.
- The firm doesn’t care and hasn’t fixed the problem even after three months since its report.
- The exposed data includes names, email and IP addresses, locations, profile pictures, and more.
The paleo diet online resource ‘Paleohacks’ has failed to secure its Amazon AWS S3 bucket properly, leaving the sensitive details of over 70,000 of its customers exposed online. The data ranges between 2015 and 2020, so it could be a backup - while the scope is global, as the platform has visitors from around the world.
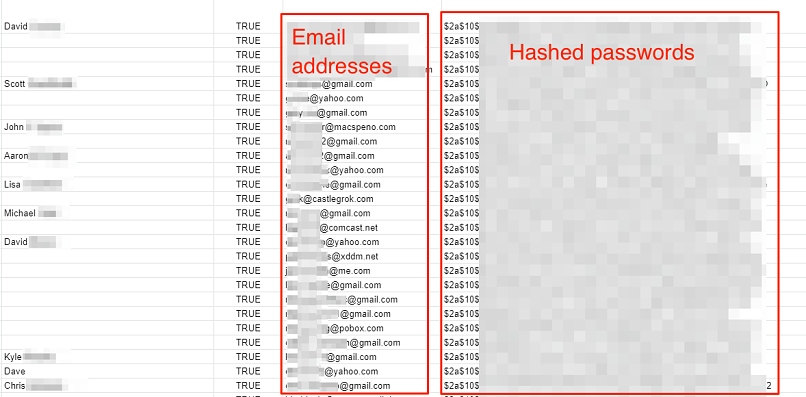
According to researchers of the vpnMentor team led by Noam Rotem, the private personal data that was accessible by anyone with a web browser are the following:
- Full names
- Usernames
- Email addresses
- Hashed passwords
- IP addresses
- Timestamps for logins
- Profile descriptions (bios)
- Employers and company details
- Location
- Personal websites
- Date of birth
- Avatar URL (profile picture)
- Points earned on Paleohacks products
The researchers informed Paleohacks about the security problem on February 7, 2021, but got no response. They reached out again four more times, most recently on April 19, 2021, when finally, a representative responded. What that person told the vpnMentor team was that they’re not interested in the data breach, and that’s why nobody bothered to reply to their repeated attempts for communication. As such, we can only assume that the database is still online and accessible.
If you are a registered member of Paleohacks, beware of risks of financial fraud, identity theft, phishing emails, scamming attempts, etc. If you are based in the EU, this data leak violates GDPR, so you should contact your data protection officer and report it. Also, the company is based in California, where the CCPA applies, so we would expect a relevant investigation from the authorities there too. If you are based in California, make sure to reach out to the relevant authorities.
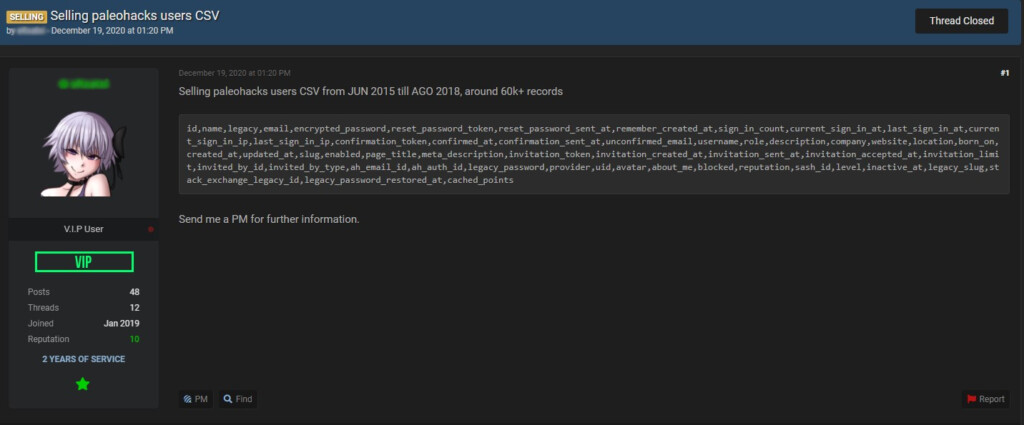
Interested in the time of exposure, which according to the researchers’ findings is at least three months, we dug deeper to see if there’s anything relevant on offer out there. Indeed, we were able to find two listings on a popular hacking forum, both posted in December 2020.
The seller listed CSV database extraction with the data dates ranging from June 2015 until 2018, comprising around 60,000 records. The contents are similar to what Noam Rotem saw in the unprotected bucket, so this bucket may have been exposed for a very long time now.