Operation ShadowHammer Hits ASUS Owners With Backdoor Malware
- A stealthy and highly targeted attack against specific ASUS hardware owners took place last year and was discovered in January by Kaspersky.
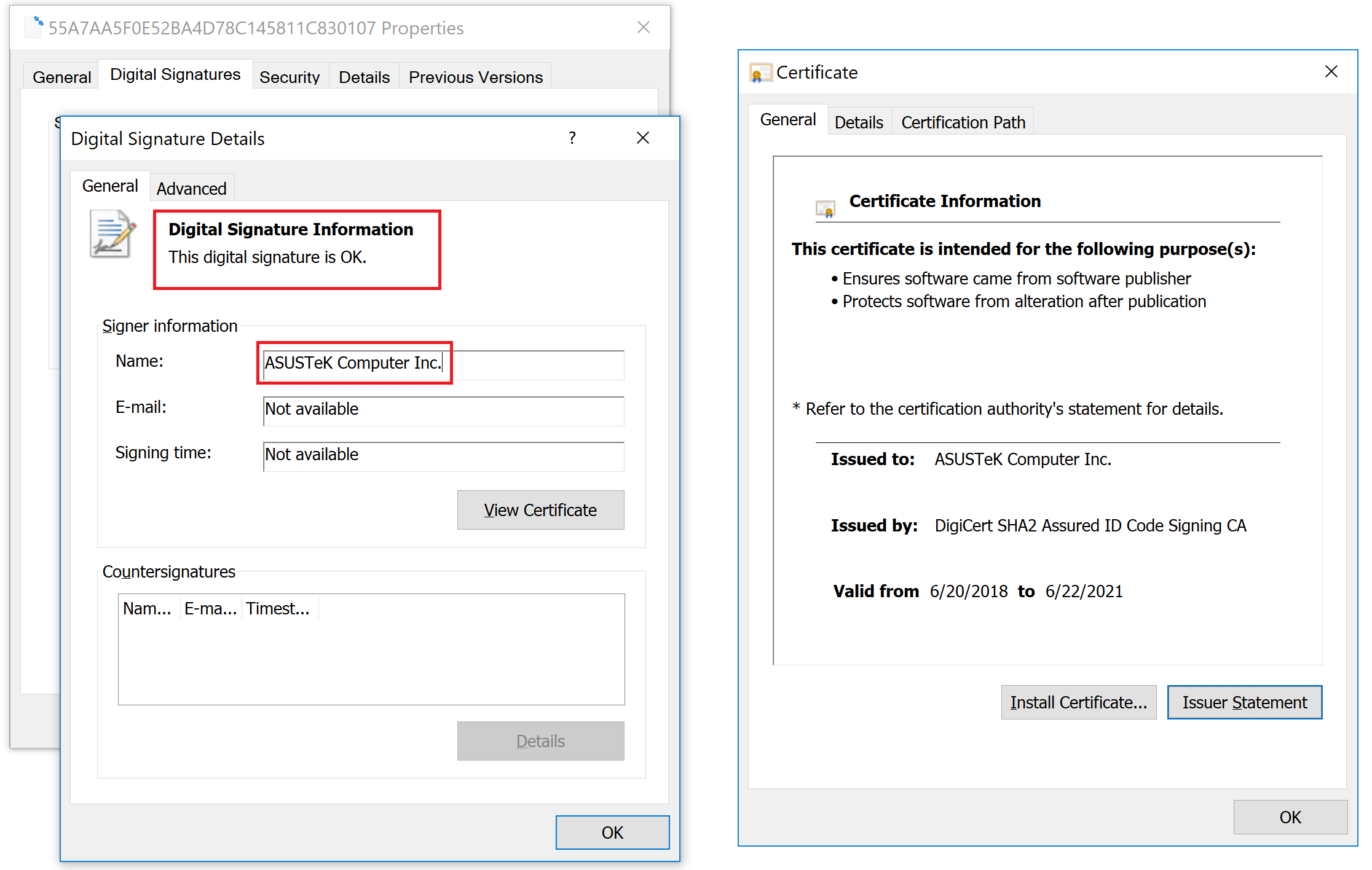
- The attack was based on a backdoor that was planted via an ASUS Live Update Utility update, signed with legitimate certificates.
- ASUS did little to remedy the situation following their briefing and chose not to inform any of their customers.
According to an absolutely staggering revelation by the Kaspersky Lab, ASUS has fallen victim to a sophisticated supply chain attack that compromised their systems to distribute certified (“trusted”) updates through the ASUS Live Update Utility, that actually came with a specially crafted malware tool. It is estimated that over a million owners of ASUS hardware have already downloaded the multi-stage backdoor on a worldwide scale, with Kaspersky confirming 57000 from their customer pool. Although the full details of the operation which is named “ShadowHammer” will be disclosed in the upcoming SAS conference in Singapore, ASUS’s inertness concerning this crucial matter has led to a premature uncovering.
The operation surgically targeted a number of users who were specified based on the MAC address of their network adapters. The malware contains a list of those addresses and compares those of the infected machines with the hardcoded list. This way it decides whether it should get activated or not. Kaspersky researchers managed to extract at least 600 entries, but there are almost certainly more. That said, there’s a large number of people who have the malware hiding in their system, but staying dormant. Kaspersky has created a tool that will help you check if your MAC address is one of the targets (and also a webpage), but it won't tell you if you have the malware backdoor planted in your system or not.
The ASUS Live Update tool is a utility that automatically fetches updates for UEFI, and hardware drivers when available, so it prompts the user to install them when ready. Since the compromise of ASUS’s system occurred at the legitimate update servers level, the malware payload is signed by a valid certificate with the name “ASUSTeK Computer Inc." This lowers the chances of the user ever suspecting that something is wrong, and made it hard to discover even for ASUS.
image source: securelist.com
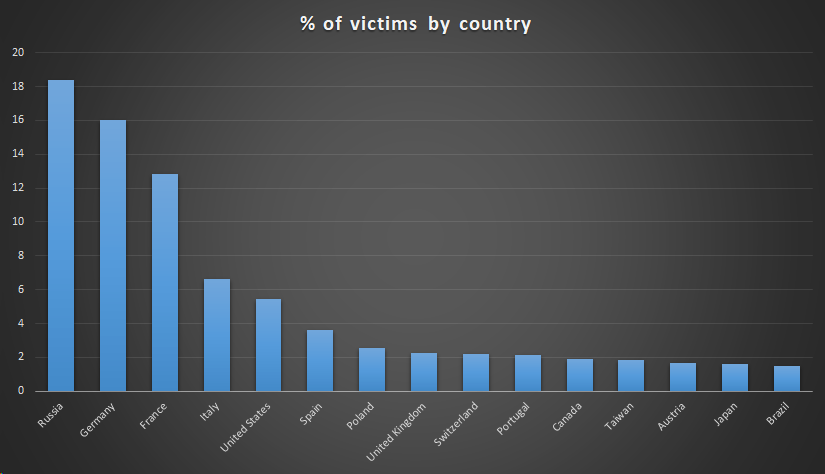
According to Kaspersky reports, the discovery was made in January this year, but the attack took place between June and November 2018. As the attack is no longer underway, the C&C server that delivered the second payload to the active backdoor is now down, and the malicious actors cannot be tracked anymore. The victim distribution graph below shows that Russia, Germany, and France were the most targeted countries, but there’s a number of targets in many other countries as well. Kaspersky notified ASUS on the day that followed the discovery, and they collaborated on the determination of the indicators of compromise since then, but the Taiwanese hardware manufacturer has not notified the affected users as they should have done by now.
image source: securelist.com
This is not the first time that ASUS falls victim of a supply chain attack, risking the security of their customers, but it’s the first that we see such a high level of sophistication and narrow targeting. In previous cases, ASUS was proven to have known about the vulnerabilities that led to the attacks, and they had even established a robust security program following pressure from the FTC (Federal Trade Commission). With this latest news, it is clear that the program didn’t help prevent yet another serious incident, so ASUS will surely get in trouble with the regulatory and customer protection authorities again. The story also goes to show that we can no longer trust the established system of hardware updates, which is based on the signing of certificates that derive from corporate servers.
Care to share your view on the above? Feel free to do it in the comments section below, or on our socials, on Facebook and Twitter.