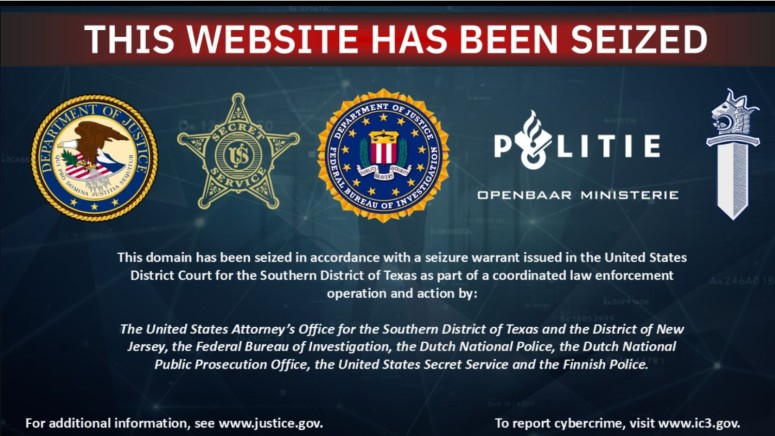
Operation Endgame: AVCheck, Key Malware Testing Tool Used Globally Dismantled by Exploiting Admin Mistakes
- The law enforcement agencies took down the AVCheck infrastructure in a coordinated effort
- The tool allowed testing the efficacy of malware on systems protected by antivirus software
- Authorities in the United States, Finland, and the Netherlands carried out this action as part of the ‘Operation Endgame’
In a coordinated international effort, 'AVCheck' has been taken down. Law enforcement agencies dismantled a tool that helped test the effectiveness of malware on systems with active antivirus.
As part of Operation Endgame, authorities from the United States, Finland, and the Netherlands seized the cybercrime tool by exploiting the mistakes of the admins, the Dutch National Police confirmed in a news release.
In the ongoing operation, the law enforcement took the AVCheck servers offline and seized the user database. They found usernames, email addresses, and payment details in the database. They will investigate and take further action based on the information.
The action on May 27 was carried out by exploiting admin errors. “The admins did not provide the security they promised,” the news release further added.
Malware developers used AVCheck to test the potential of malicious tools on targeted systems that had antivirus software to detect cyber threats. The high-speed antivirus scan time checker was one of the most crucial tools for cybercriminals worldwide.
As part of Operation Endgame, the U.S. Department of Justice federally charged 16 individuals accused of operating a Malware-as-a-Service platform, DanaBot.
A ransomware kill chain was broken this May, wherein 300 servers and 650 domains were taken down, and 20 international arrest warrants were issued.
Authorities arrested four individuals, took down over 100 servers, and disabled multiple global malware droppers during this operation.