New ‘Operation Celestial Force’ Campaign Aims Malware at Indian Targets
- A new malware campaign called ‘Operation Celestial Force’ targets entities and individuals in India.
- The campaign employs an Android-based malware and a Windows-based malware loader.
- The targets appear to be connected to official government entities.
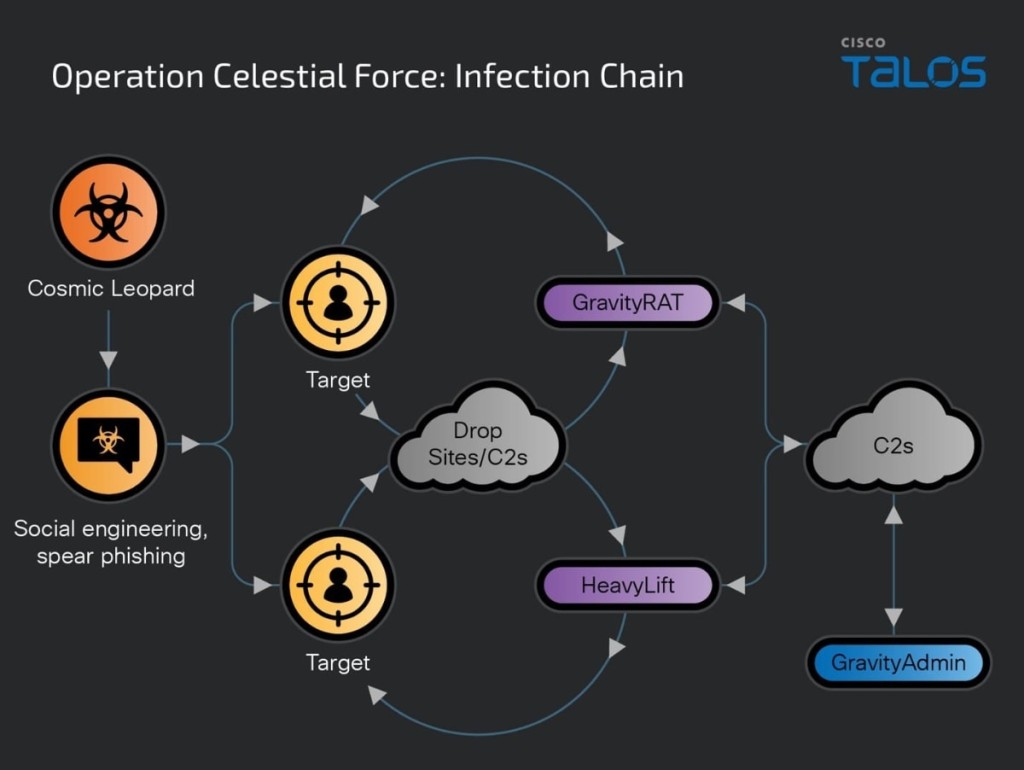
A new malware campaign called Operation Celestial Force, running since at least 2018 and still active today, employs the use of Android-based malware ‘GravityRAT’ and Windows-based malware loader tracked as ‘HeavyLift’ to target Indian entities and individuals likely belonging to defense, government, and related technology spaces, as disclosed by Cisco Talos.
Talos attributes this multiyear operation to Pakistani threat actors they call Cosmic Leopard. Their focus is on target espionage and surveillance. The campaign's main infection vectors are spear phishing and social engineering.
The suspected cyber criminals were initially observed deploying the Windows-based version of GravityRAT, a remote access trojan, via malicious documents (maldocs) in 2018, also on targets in India. They started using the Android version around 2019.
HeavyLift is an Electron-based malware loader that consists of JavaScript code communicating and controlled by a C2 server.
A standalone tool the researchers call GravityAdmin carries out malicious activities on a compromised device, administering all GravityRAT and HeavyLift infections. These custom-built panel binaries administer and run multiple campaigns simultaneously, all of which are codenamed and have their own admin panels.
For example, Android-based GravityRAT infections are given the names FOXTROT, CLOUDINFINITY and CHATICO, and attacks deploying HeavyLift are codenamed CRAFTWITHME, SEXYBER, and CVSCOUT.
The actors use spear phishing techniques, consisting of messages with the correct language, GravityRAT maldocs, and social engineering, to convince potential victims via social media to download malware, as HeavyLift primarily sends malicious installers.
The Cosmic Leopard tactics, techniques, tooling, and victimology sometime overlap with those of another suspected Pakistani APT group, Transparent Tribe, which is known for focusing on high-value targets from the Indian subcontinent, but these are not linked for now.
Recently, an increased use of mobile malware for espionage to target high-value targets, including commercial spyware, has been observed.