Open-Source Red Team Tool Adaptix Framework Exploited by Cybercriminals with Russian Ties, Including Akira
- Legitimate tool: Adaptix, an open-source post-exploitation framework for penetration testers, is being actively used by cybercriminals to deliver malicious payloads.
- Russian underworld: This framework’s ties with the Russian criminal underground include a key dev who manages a Russian-language Telegram channel for the tool.
- Major campaigns: Adaptix is used with the CountLoader malware loader and in global ransomware campaigns, including by affiliates of the Akira ransomware group.
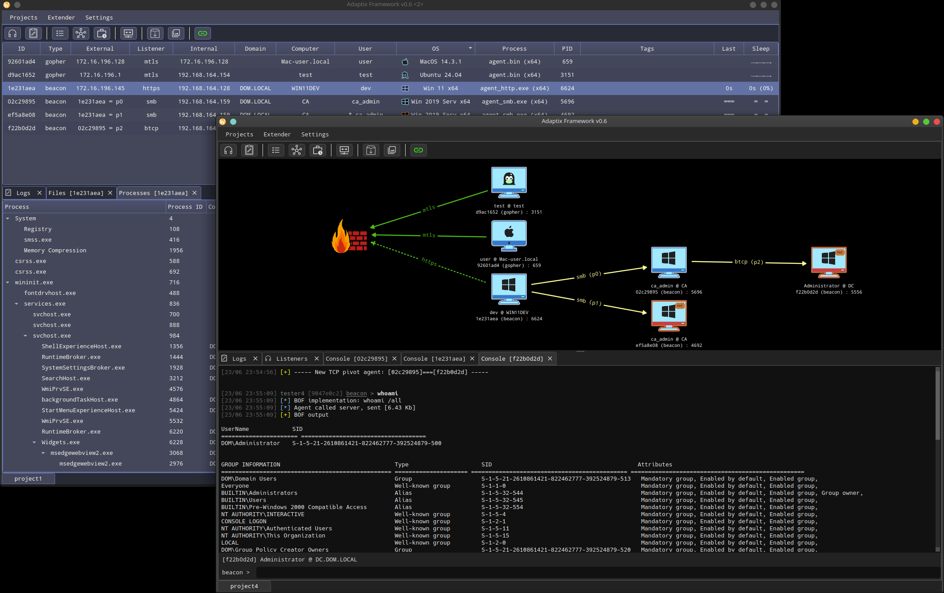
Cybercriminals widely abuse Adaptix, turning a legitimate penetration testing tool into a weapon for delivering malicious payloads. Adaptix is an open-source post-exploitation framework intended for security professionals and red teams to simulate attacks and identify vulnerabilities.
However, recent findings from Silent Push reveal its growing adoption by threat actors, including its use in campaigns deploying the Akira ransomware. The line between ethical hacking tools and criminal instruments continues to blur, creating significant cybersecurity threats.
Adaptix Ties to Russian Hackers and Criminal Forums
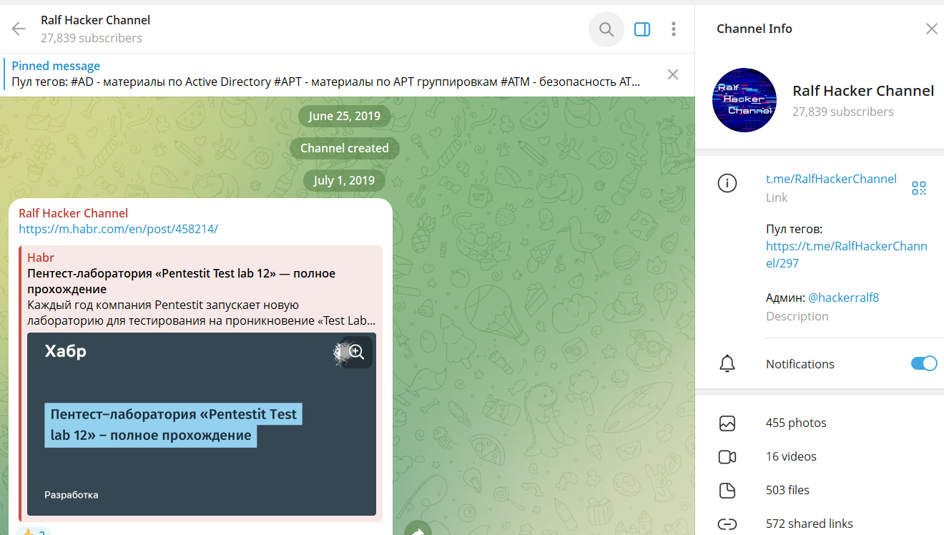
Investigations into the framework have revealed strong ties between Adaptix and Russian hackers. A key developer, known as "RalfHacker," actively maintains the tool's GitHub repository and promotes it on a Russian-language Telegram channel.
This individual, who self-identifies as a "maldev" (malware developer), has also been linked to known hacking forums.
“While we can confirm that the lead developer for AdaptixC2 manages a Telegram advertising channel in Russian, this only gives us a certain degree of confidence about their actual location or nationality,” Kasey Best, Director of Threat Intelligence at Silent Push, told TechNadu.
While the developer's direct involvement in malicious activities remains unclear, the tool's marketing within Russian criminal circles and its subsequent use by threat actors raise significant red flags for the security community.
Servers hosting Adaptix C2 are likely being used for attacks, not solely for pen testing, Kasey Best said. Bumblebee and AdaptixC2 also delivered Akira in August.
“Our team is currently tracking more Adaptix C2 IPs hosted in China vs anywhere else, with additional live infrastructure in both Singapore and Hong Kong,” Best added. “There are significant numbers of servers in the U.S. and several other countries, including Russia.”
Delivering Malicious Payloads with Adaptix
Threat actors are leveraging Adaptix to drop malicious payloads onto compromised systems. The abuse was first noted during research into the CountLoader malware, where attacker infrastructure was found serving malicious Adaptix payloads. This indicates a preference among criminals for using both tools in concert.
The exploitation of legitimate, extensible frameworks like Adaptix complicates mitigation efforts for defenders, as they must distinguish between ethical and malicious use, providing an additional layer of obfuscation for cybercriminals.
Software extensibility refers to the ability to easily enhance, modify, or adapt a system with new functionalities or capabilities without altering its core architecture or significant rewrites of existing code.
The relatively new CountLoader malware loader is strongly associated with Russian ransomware gangs LockBit, BlackBasta, and Qilin. “During our analysis of CountLoader malware, we were able to discover a ransomware affiliate with ties to the LockBit, BlackBasta, and Qilin ransomware groups who has used Adaptix C2,” Kasey Best said.
In May 2024, a Europol-led effort dismantled infrastructure linked to multiple malware families, including SmokeLoader, Bumblebee, TrickBot, and IcedID. Bumblebee and AdaptixC2 also delivered Akira in August 2025.
Palo Alto’s September report on Adaptix C2 offers detailed information that can help defenders better understand how this may appear in an organization’s device and/or network logs.