Oldsmar Water Treatment Facility Hackers Used ‘Watering Hole’ Website to Gain Access
- Analysts have found the ‘watering hole’ site that almost certainly led to the Oldsmar incident.
- An employee of the water treatment facility visited the malicious site on the day of the attack.
- The reason for the specific targeting is unclear, but the motive appears to be the improvement of a botnet.
Back in February, the American public was shocked to learn about hackers accessing the control systems of a water treatment facility in Oldsmar, Florida, and attempting to raise caustic chemicals to dangerous levels. Almost by pure chance, this took place while on-site operators were present, so they identified the change and reverted the action immediately. The first assumption was that the hackers used a vulnerability on the outdated OS of the facility computers to access TeamViewer and assume control of the water systems.
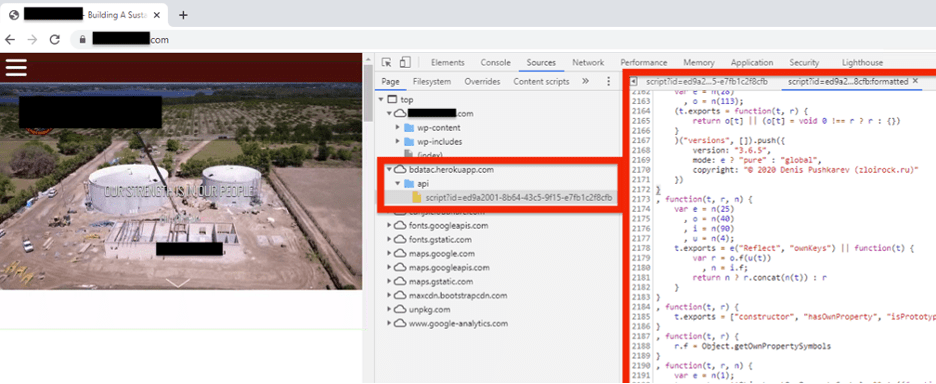
The Dragos team was called to investigate, and they are now in a position to give the public some details about how exactly the attack unfolded. According to their detailed report, the actors managed to compromise the site of a contractor of the Florida facility, inserting malicious code into the footer file. The hackers exploited a vulnerability in one of the multiple outdated WordPress plugins used on the site at that time, so that part wasn’t fairly uncomplicated.
According to the logs examined by the Dragos team, on February 8, 2021, mere hours before the chemical changing action took place, someone from the Oldsmar facility visited the ‘watering hole’ website. But that employee wasn’t the only person to visit the dangerous site.
The telemetry data reveals that during the 58 days the watering hole kept on sucking victims in, over a thousand users visited it. It is unknown if the actors only got to exploit the Oldsmar opportunity and why they may have opted to keep things limited to it.
Dragos reverse-engineered the script used on the site and found that it could draw the following information from the site visitors:
- Operating system and CPU
- Browser, including available languages
- Touch points, input methods, presence of camera, accelerometer, microphone
- Video card display adapter details, and
- Time zone, geolocation, video codecs, screen dimensions, browser plugins
The script also directed the visitor to two separate browser cipher fingerprinting sites, to collect TLS and also JA SSL cipher fingerprint hashes.
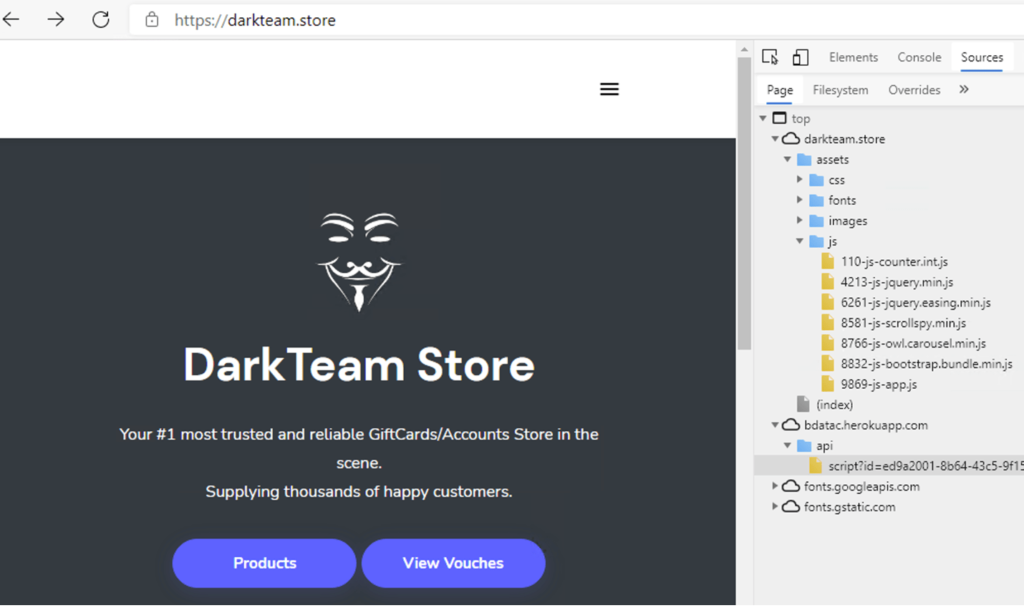
By digging deeper, Dragos found a link to an actor called “DarkTeam,” which is connected with the botnet malware “Tofsee.” All in all, it looks like the actor selected the specific site at random to test the botnet in the wild and improve its ability to evade detection. Of course, that still doesn’t explain why someone tried to fiddle with the water quality at the Oldsmar facility, but it was a wake-up call for everyone in the country, no doubt.