NSO’s ‘Pegasus’ Deployed Against 36 Journalists in the Middle East
- Journalists working at media outlets that expose Middle Eastern regimes targeted by ‘Pegasus’ spyware.
- The hacks were silent and interactionless, raising no warning flags on the compromised device.
- It is believed that the discovery is only a small part of the surveillance that goes on against investigative journalists.
NSO Group’s ‘Pegasus’ spyware was found in 36 phones belonging to journalists, producers, anchors, and executives at Al Jazeera, and also the device of a journalist working at Al Araby TV. The target devices were iPhones, and the hack took place through the “KISMET” zero-click exploit chain, which lies in iMessage.
The vulnerability works on iOS 13.5.1 or earlier, which was running on the iPhone 11 last year. As KISMET probably doesn’t work on iOS 14 or later, and considering that iPhone users are quick to update their devices to the latest version of Apple’s mobile OS, these attacks must have stopped when the new system was rolled out.
The attacks took place between October and December 2019, launched by at least four different entities. According to the details given in a Citizen Lab report, one of the operators they were able to identify is the Saudi Arabian “MONARCHY,” and a second one is “SNEAKY KESTREL,” based in the United Arab Emirates. It is very possible that the 36 ‘Pegasus’ infections are only the tip of the iceberg and that a greater number of iPhone 11 / iOS 13 users were under sneaky surveillance last year.
Interactionless zero-click attacks are awesome for hackers as the target doesn’t have to do anything from their side, and thus, there's no need for social engineering or any trickery. UAE-based organizations have used such exploits to spy on iPhone users many times in the recent past, with confirmed examples starting from 2016. Usually, this spyware arrives on the devices via Apple’s ‘Push Notification Service’ (APN), which is iMessage’s protocol.
Al Jazeera’s investigative journalism is not resonating well with some of the regimes that rule in the Middle East, as the Qatar-based (and public-owned) news network has exposed their unethical practices multiple times, with details and irrefutable documents. Qatar itself has been found in the center of criticism for allegedly protecting fugitives and terrorists of neighboring countries, so in terms of international relations in the region, both the broadcaster and its owner are isolated and condemned.
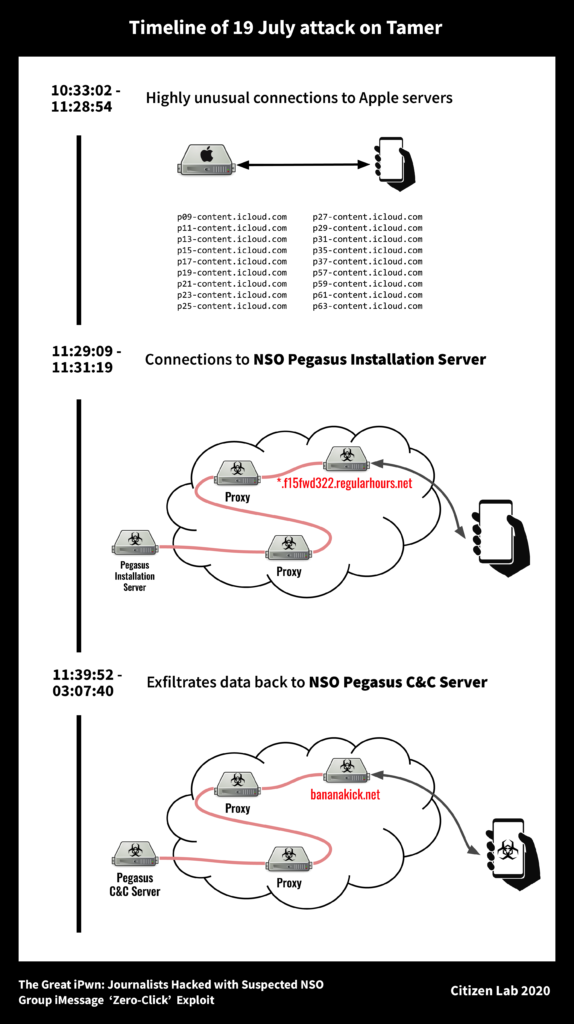
One of the journalists targeted by these attacks, Tamer Almisshal, was suspicious and talked to Citizen Lab. He agreed to install a VPN application for the researchers to analyze the internet traffic that comes and goes from his device. Indeed, they’ve found that the device was performing unusually frequent connections to Apple servers, indicative of the APN abuse, and also connected to NSO Pegasus installation and data exfiltration servers.
The ‘Al Araby TV’ journalist targeted by shady entities was Rania Dridi, who was using an iPhone Xs Max. Citizen Lab researchers found evidence that Dridi’s phone was hacked at least six individual times, even when it was running the latest available version of the iOS.
If you’re a journalist using an iPhone, you should immediately update to iOS 14 and make sure to apply any bug-fixing patches as soon as they arrive. Right now, there’s no evidence that the NSO has managed to update Pegasus to work effectively against Apple’s latest mobile OS version, but we’re sure that they’re working on it with all their power.