Novel The Gentlemen Ransomware Group Targets Critical Industries in Over 15 Countries
- Gentlemen ransomware: The newly discovered threat actor conducts ransomware campaigns targeting mainly the U.S. and Thailand.
- Tooling: They use custom-built tools for defense evasion and abuse of both legitimate and vulnerable system components.
- Notable approach: By tailoring their tactics against specific security vendors, they show awareness of their targets’ environments.
A previously undocumented threat actor, dubbed "The Gentlemen," has demonstrated advanced capabilities, targeting critical industries across at least 17 countries with a highly adaptive and systematic approach. New Trend Micro research provides an in-depth ransomware attack analysis of the group.
Tactics, Techniques, and Procedures
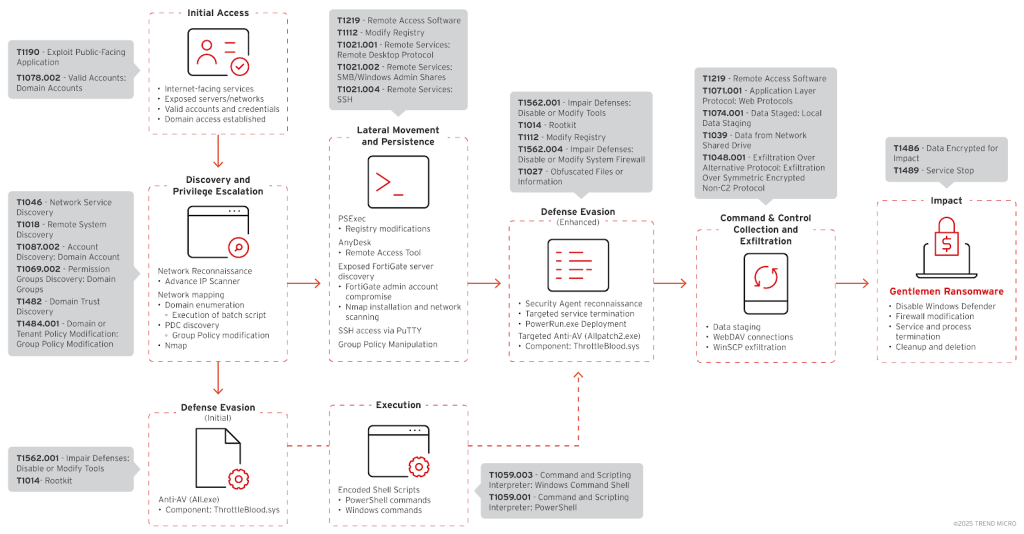
The Gentlemen ransomware group employs a sophisticated attack chain characterized by custom tools and adaptive evasion techniques. The campaign leverages the abuse of legitimate, signed drivers to achieve kernel-level manipulation, allowing them to terminate endpoint protection processes.
The actors have shown proficiency in abusing Group Policy Objects (GPOs) to facilitate domain-wide compromise, indicating a deep understanding of enterprise environments.
The group uses a combination of legitimate tools like PsExec, Nmap, and AnyDesk for lateral movement, reconnaissance, and persistence, querying local groups such as standard administrative and virtualization-specific groups like VMware.
Initial access is believed to be gained through the exploitation of internet-facing services, such as a compromised FortiGate server. Data exfiltration is conducted using encrypted channels via WinSCP, highlighting the group's operational security awareness.
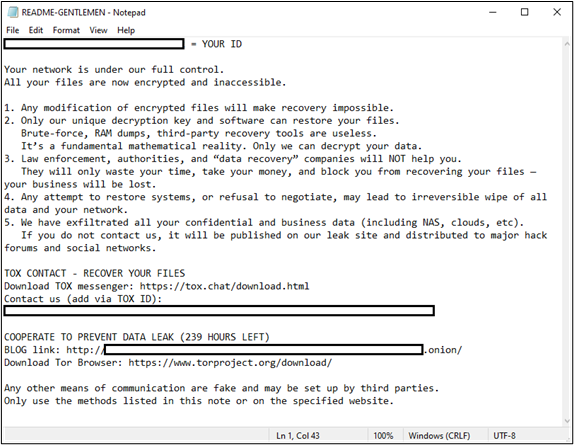
The ransomware payload itself is password-protected, likely to evade automated sandbox analysis, and is deployed through the NETLOGON share for maximum impact. Before encryption, the malware disables Windows Defender and modifies firewall rules to ensure persistent remote access.
A Cybersecurity Threat to Critical Industries
This campaign poses a significant cybersecurity threat to critical industries. Trend Micro's analysis reveals a focus on manufacturing, construction, healthcare, and insurance sectors, primarily in the Asia-Pacific region and the U.S.
Their methodical approach underscores the severe risk the Gentlemen group presents to global organizations.
A recent The DFIR Report intrusion analysis revealed overlap in RansomHub, DragonForce, and Play ransomware operations. In March, RansomHub was linked to Play, Medusa, and BianLian Ransomware via shared EDRKillShifter use, and DragonForce claimed an alleged RansomHub takeover in April.