Novel “Kraken” Attacks Abuse the Windows Error Reporting Service
- An unidentified APT group is using spear phishing to launch file-less attacks on Windows systems.
- The method involves abusing the Windows Error Reporting service, leading to shellcode injection on target processes.
- The researchers who discovered the campaign have reasons to believe this is the work of Vietnamese hackers.
There’s a new type of attack called “Kraken,” which involves injecting a payload into the Windows Error Reporting (WER) service. This service handles errors in the operating system and the applications that run on it, so fiddling with it means that the hackers can exploit a deeper level of Windows API functions.
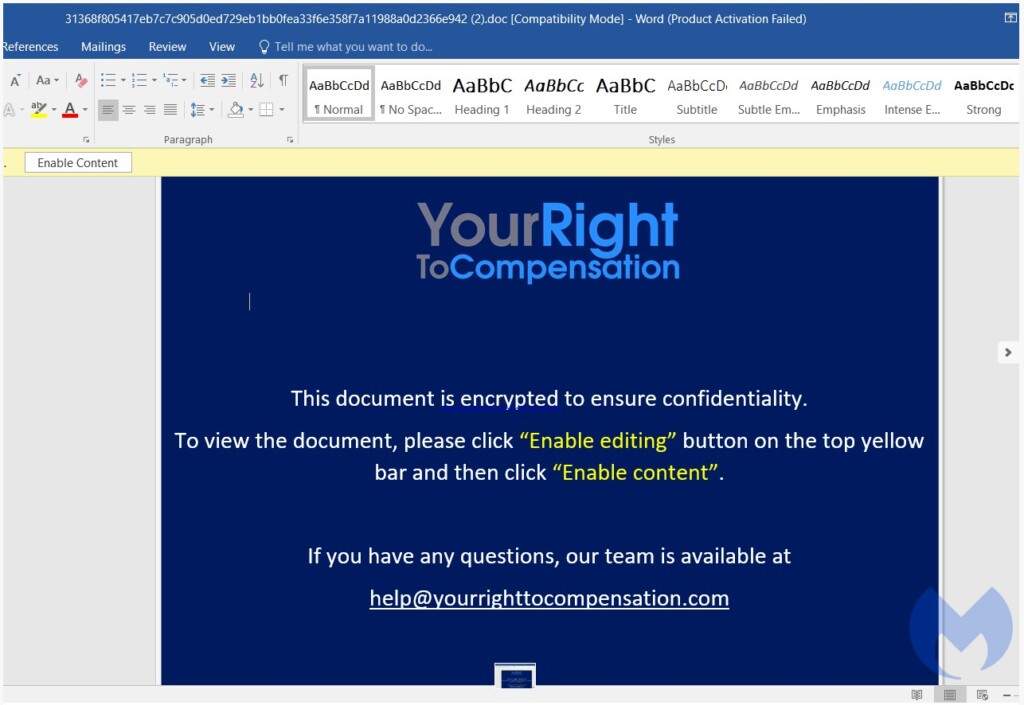
Malwarebytes, who has been following this campaign, believes that the attacks are launched by an APT group, potentially the Vietnamese APT32, but there can be no confident attribution. The actors launch their attacks using spear-phishing techniques and a document titled “Compensation manual.doc,” and with so many people having lost or on the verge of losing their jobs right now, this theme is very alluring.
For pretense reasons of confidentiality, the document is supposedly encrypted, and the recipient is advised to “enable content” in order to view it. This is a trick to make the victim enable macros on their Office suite, which then downloads a custom version of the CactusTorch VBA module, eventually resulting in the execution of shellcode.
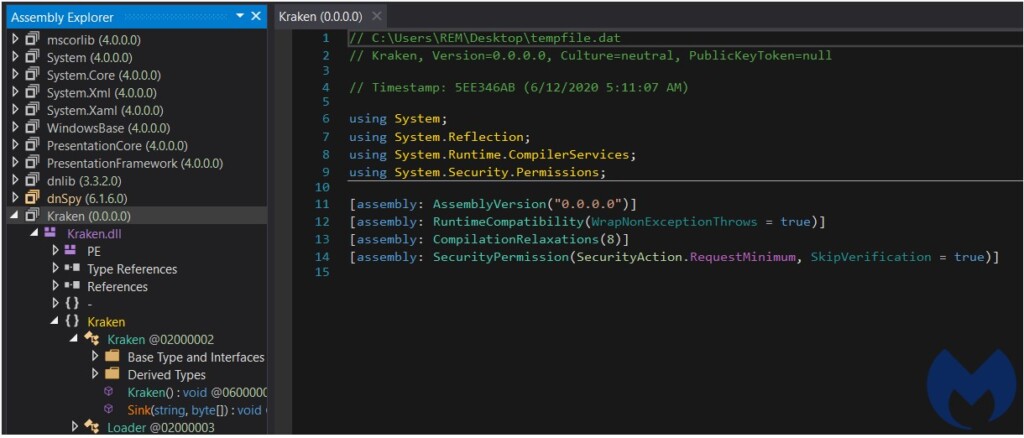
Next, a .Net payload is loaded into the memory and an entry class defined with a “Kraken.Kraken” value is created. Upon the execution of the payload, the injection to the WER is carried out, setting things up for pushing shellcode into target processes via Windows API calls.
Read More: Newly Unearthed APT Group “XDSpy” Has Been Around Since 2011
After de-obfuscating the injected shellcode, Malwarebytes researchers figured that the payload is capable of detecting if it runs inside a sandbox environment and stops to avoid analysis. Anti-debugging features are also present and actually quite extensive.
The API calls that are supported by the shellcode are the following:
- VirtualAlloc
- VirtualProtect
- CreateThread
- VirtualAllocEx
- VirtualProtectEx
- WriteProcessMemory
- GetEnvironmentVariableW
- CreateProcessW
- CreateRemoteThread
- GetThreadContext
- SetThreadContext
- ResumeThread
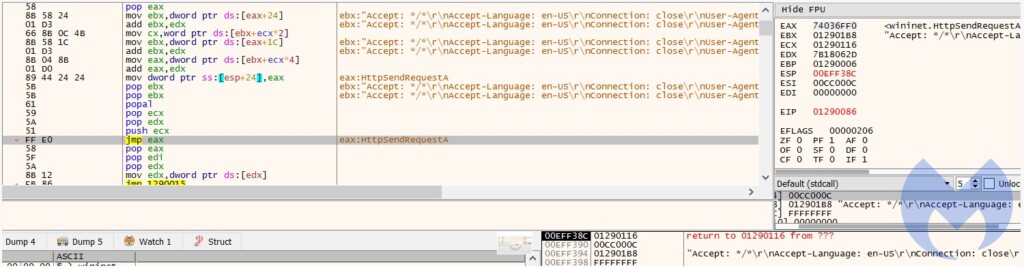
The fetching of the additional shellcode that is injected into the target processes is done via an HTTP request, pointing to compromised websites such as the “asia-kotoba.net.”
MalwareBytes mentions several similarities to previously recorded APT32 activity, like the use of CactusTorch, but since they couldn’t get the final payload, they are not in a position to attribute this campaign to anyone with certainty. The malicious archives are hosted in a domain registered in Ho Chi Minh, Vietnam, which is consistent with the APT32 assumption, but this is still no solid proof.