Novel Interlock RAT Variant Uncovered in KongTuke FileFix Campaign Relying on Fake CAPTCHAs
- Numerous industries are targeted in a KongTuke campaign that transitions to a FileFix variant.
- Attackers employ fake CAPTCHA verifications to deploy an enhanced version of the Interlock RAT.
- It utilizes Cloudflare Tunnel to conceal the C2 server's location and employs hardcoded fallback IP addresses for resilience.
A new, highly resilient variant of the Interlock Remote Access Trojan (RAT) has surfaced, reportedly linked to the KongTuke FileFix campaign, which utilizes a delivery mechanism that includes PHP-based malware and advanced persistence techniques.
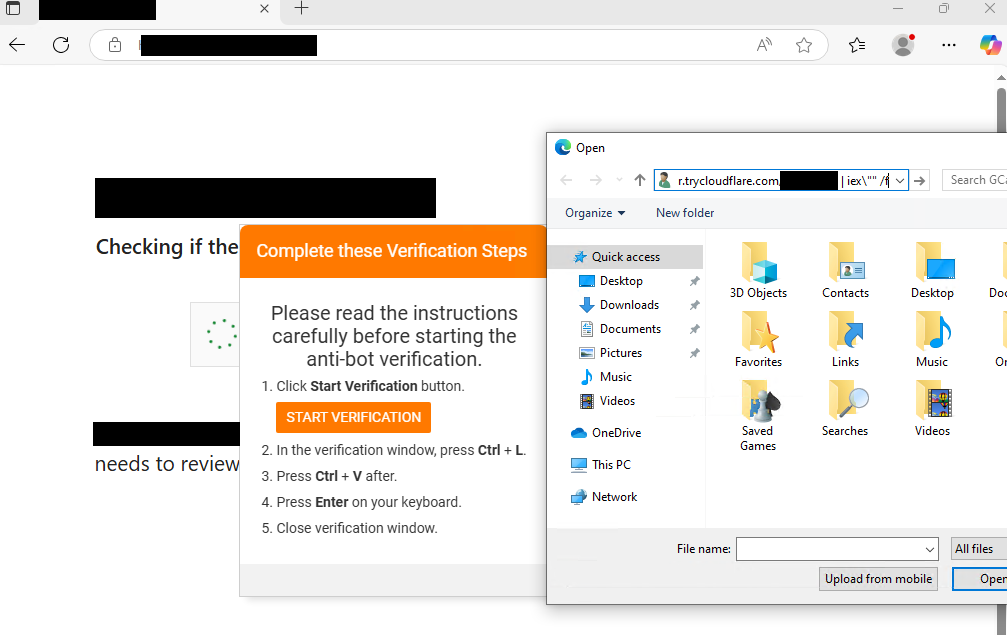
The Interlock RAT variant diverges from earlier iterations by transitioning from JavaScript-based payloads to leveraging PHP scripts, according to the latest security analysis from The DFIR Report. Delivered via compromised websites, the malware begins its attack with a malicious JavaScript web injection.
Unsuspecting users visiting infected websites encounter a fake CAPTCHA verification followed by deceptive instructions to paste content into a command prompt. These steps execute a PowerShell script that initiates the infection chain.
Researchers observed the updated delivery method introducing a FileFix variant, which deploys the PHP-based Interlock RAT payload.
The malicious PowerShell script downloads and launches a PHP executable located in the user’s AppData/Roaming directory, paired with a configuration file designed to activate the RAT’s operational functionality.
Upon execution, the Interlock RAT performs comprehensive system reconnaissance. PowerShell commands are used to collect vital system data, including processes, services, mounted drives, and local network details.
The KongTuke FileFix campaign utilizes Cloudflare’s trycloudflare.com URLs to establish secure connectivity between the compromised system and the C2 infrastructure, effectively masking the true location of its servers. The RAT also includes fallback IP addresses to ensure resilient communication in the event of disruptions.