Novel ‘Commando Cat’ Cryptojacker Abuses Docker Remote API Servers
- A new attack campaign called 'Commando Cat' exploits exposed Docker remote API servers to deploy crypto miners.
- The actors use Docker images from the open-source Commando project, hence the name.
- The malicious campaign has been active since the beginning of 2024.
A cryptojacking attack campaign that researchers call ‘Commando Cat’ abuses Docker remote API servers left unprotected to deploy cryptocurrency miners, a TrendMicro report says. Attackers gain initial access, distribute malicious binaries, and evade conventional security measures by exploiting Docker configurations and leveraging open-source tools.
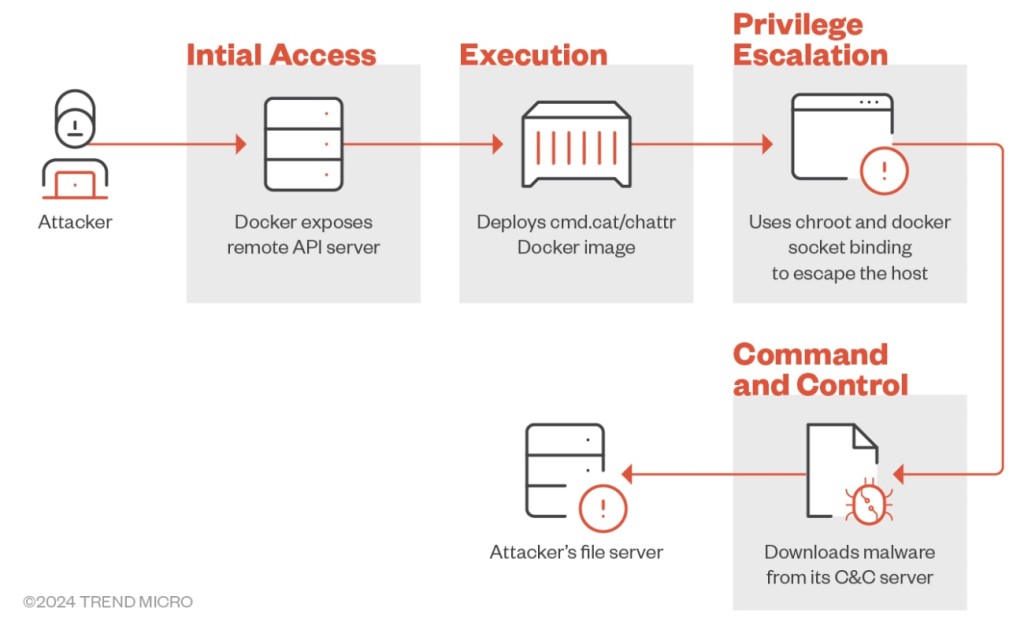
‘Commando’ is a publicly available open-source GitHub project that creates Docker images on demand for developers. This attack campaign begins with a ping to the Docker Remote API server to kickstart the chain of actions.
In the initial step, it deploys Commando via ‘cmd.cat’ to generate malicious containers for distribution. The attackers use a simple docker image named ‘cmd.cat/chattr’ for initial access, which helps evade detection. They create a docker container based on this image while executing a base64-encoded string and use it to retrieve the payload from their own command and control (C&C) servers.
The actors managed to break out of the container using chroot to peek outside the container and volume binding, which also binds the Docker socket and gives the container direct access to the Docker daemon on the host. After the deployed malware connects to its C&C server, the campaign starts deploying cryptocurrency miners using ‘curl’ or ‘wget’ commands via a shell script.
The malicious binary is packed using the UPX packer and is suspected to be ZiggyStarTux, an open-source IRC bot based on the Kaiten malware, also known as Tsunami. Attack indicators also include the use of DropBear SSH, a relatively small SSH server and client application on TCP port 3022.
Certain container security practices, like properly configuring containers and APIs and using trusted Docker images, help mitigate such attacks.