Novel Chaos Ransomware Group Attacks Target Businesses Globally, Overlaps with BlackSuit
- New threat actor: A novel RaaS operation capitalizes on the Chaos name association with popular ransomware builder tool variants.
- TTPs overlap: Security researchers say Chaos TTPs overlap with BlackSuit (Royal) ransomware.
- Target demographics: The organizations targeted are predominantly located in the U.S., with a few also in the U.K., New Zealand, and India.
The newly formed Chaos ransomware group has surfaced as a major cybersecurity threat in 2025. This emerging ransomware-as-a-service (RaaS) operation targets organizations worldwide, utilizing advanced techniques to exploit local and network resources for maximum impact.
Tactics and Techniques
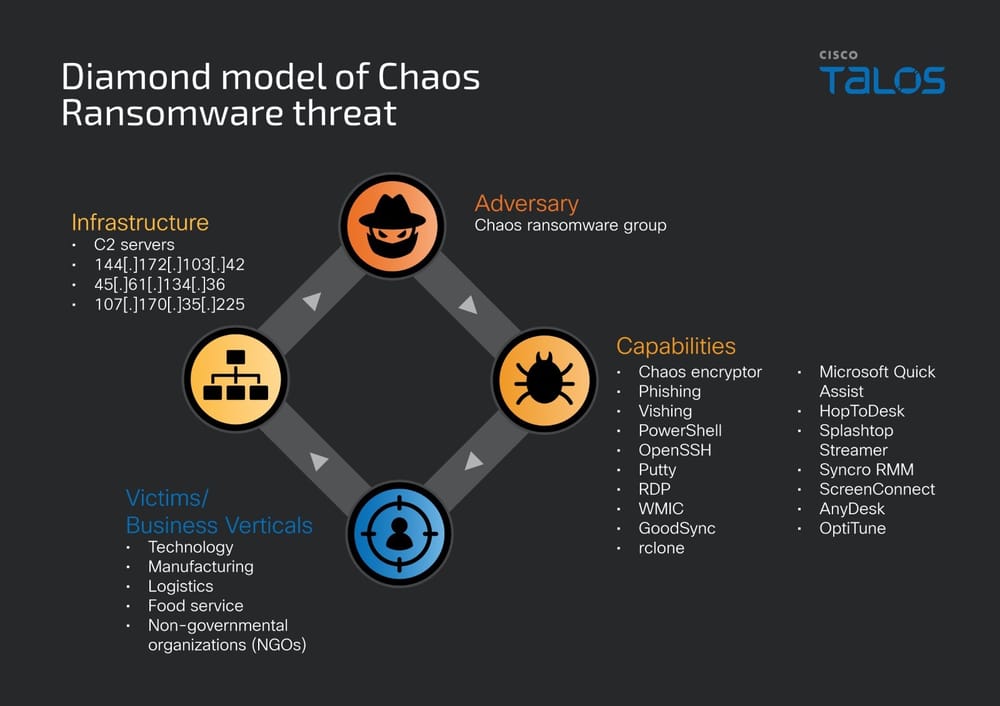
Emerged as early as February 2025, the Chaos ransomware employs double extortion attacks, encrypting files and simultaneously exfiltrating sensitive data, according to recent reports by researchers at Cisco Talos.
Importantly, it is not connected to the Chaos ransomware builder tool variants or its developers, but rides the confusion wave regarding the name.
However, similarities in Tactics, Techniques, and Procedures (TTPs), such as encryption commands, ransom note theme and structure, and the use of LOLbins and RMM tools, link it to BlackSuit (Royal) ransomware.
Attackers rely on social engineering, including sophisticated phishing and voice phishing (vishing), to infiltrate victim environments. They even leverage legitimate file synchronization and backup software, GoodSync, in the attack to extract data.
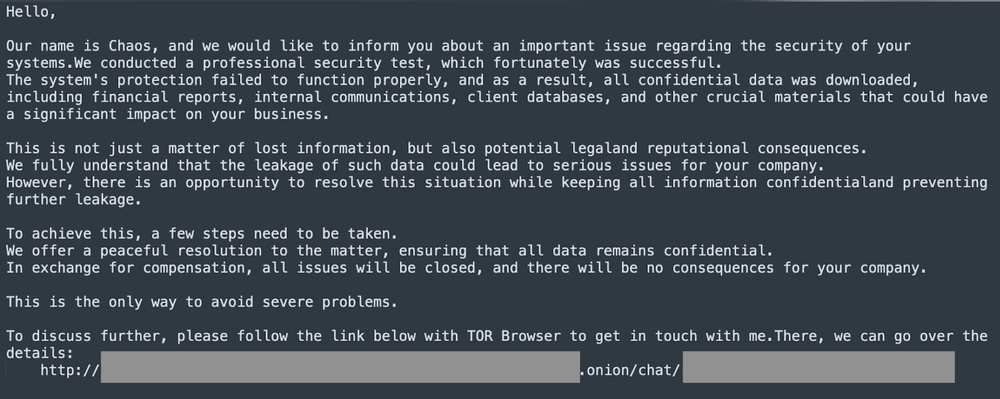
Their malware incorporates multi-threaded, rapid encryption and targets files both locally and across network infrastructures. The ransomware assigns the new ".chaos" file extension to encrypted items, leaving victims with a ransom note, "readme.chaos.txt," which details the demands.
Chaos integrates multi-layered anti-analysis measures, including window enumeration, process monitoring, and timing analysis techniques, to evade detection by virtual machine environments, automated sandboxes, and security analysis platforms.
It achieves persistence in compromised systems through the installation of remote management tools like AnyDesk, ScreenConnect, OptiTune, Syncro RMM, and Splashtop.
The Chaos ransomware group offers an automated management panel and uses Onion URLs for affiliate registration, as well as a refundable entry fee. It actively promotes its cross-platform ransomware on the dark web forum RAMP, targeting Windows, ESXi, Linux, and NAS systems with features like rapid encryption, individual file keys, and network scanning.
Targets and Global Reach
The Chaos ransomware group has specifically refrained from targeting government entities, hospitals, and organizations in BRICS (Brazil, China, Egypt, Ethiopia, India, Indonesia, Iran, Russia, South Africa, UAE) and Commonwealth of Independent States (CIS) nations.
However, businesses across sectors in the U.S., U.K., India, and New Zealand have been hit. Victim data is published on a dedicated leak site if the ransom demands are not met – $300,000 in this analysis.
Talos believes Chaos RaaS could be either a BlackSuit rebrand or run by some of its members. The most impactful cyber intrusion of the latter is the 2024 attack on CDK Global, which allegedly paid a $25 million ransom to the hackers.