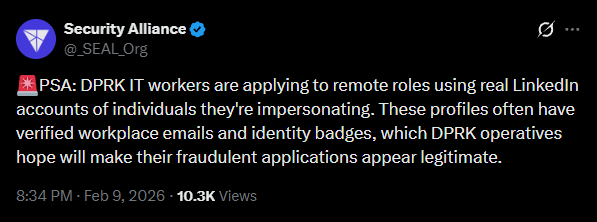
North Korean Operatives Impersonate Real Professionals on LinkedIn, the Security Alliance Warns
- Current Tactic: North Korean operatives are using verified LinkedIn profiles to impersonate professionals and establish trust with targets.
- Possible Goal: The primary objective for such campaigns is cyberespionage and intellectual property theft, with a focus on defense, IT, and government sectors.
- General Methodology: Operatives engage in prolonged social engineering campaigns, often culminating in the delivery of malicious payloads through seemingly legitimate job offers or professional collaborations.
Operatives from the Democratic People's Republic of Korea (DPRK) are conducting sophisticated social engineering campaigns by impersonating professionals on LinkedIn. The ultimate goal of these operations is usually to infiltrate target organizations, conduct cyber espionage, steal valuable intellectual property, and gain persistent access to corporate networks.
LinkedIn Cyberespionage
This DPRK LinkedIn impersonation scheme involves creating detailed, credible profiles that steal the professional identities of real people, often displaying verified workplace email addresses and identity badges, the non-governmental & nonprofit organization Security Alliance (SEAL) warned in a post on X.
The threat actors then use these credible LinkedIn profiles to apply for remote roles. Since these contain real details of the impersonated individuals, background verification checks out, and recruiters can be easily misled.
The known cyber espionage tactics employed by these North Korean threat actors in previous campaigns involve establishing a connection and building rapport with a target to create an opportunity to share a weaponized document.
Corporate Cybersecurity Implications and Defense
This campaign highlights a significant vulnerability in corporate cybersecurity: the human element. By leveraging professional networking platforms, these operatives bypass traditional technical defenses such as firewalls and email gateways.
Organizations must educate their staff to scrutinize unsolicited connection requests and be wary of job offers that seem too good to be true.
“Always validate that accounts listed by candidates are controlled by the email they provide,” SEAL wrote. “Simple checks like asking them to connect with you on LinkedIn will verify their ownership and control of the account.”
In the first half of 2025, reports highlighted that LinkedIn crypto job seekers could be North Korean cybercriminals, the North Korea-linked ‘DeceptiveDevelopment’ targeted freelance developers with infostealers, and North Korea-linked Lazarus Group (APT38) targeted Bitdefender Labs researchers with fake job offers.
In December, Amazon blocked 1,800+ suspected North Korean IT operatives from securing remote roles. In November, MI5 warned of Chinese spies posing as recruiters to access sensitive information from U.K. officials.