North Korean Hackers Targeting Security Researchers With Zero Days
- The white-hat community is actively targeted by elaborate campaigns launched by state-sponsored hackers.
- The actors tricked the security researchers with fake blog posts, phony exploits, and fabricated PoC videos.
- The compromise takes place either by voluntarily installing a DLL malware or via a click-less zero-day.
Google’s Threat Analysis Group has recorded the recent activities of a North Korean group of state-supported hackers who are reportedly focusing on targeting security researchers. The threat actors are interested in the particular category of professionals because they work in the vulnerability research and development space.
So their work is precious in the sense that it can reveal exploitable points the hackers can use. Accessing this kind of information is an amazing time-saver for the hackers, but they still need to invest some time in social engineering for this purpose.
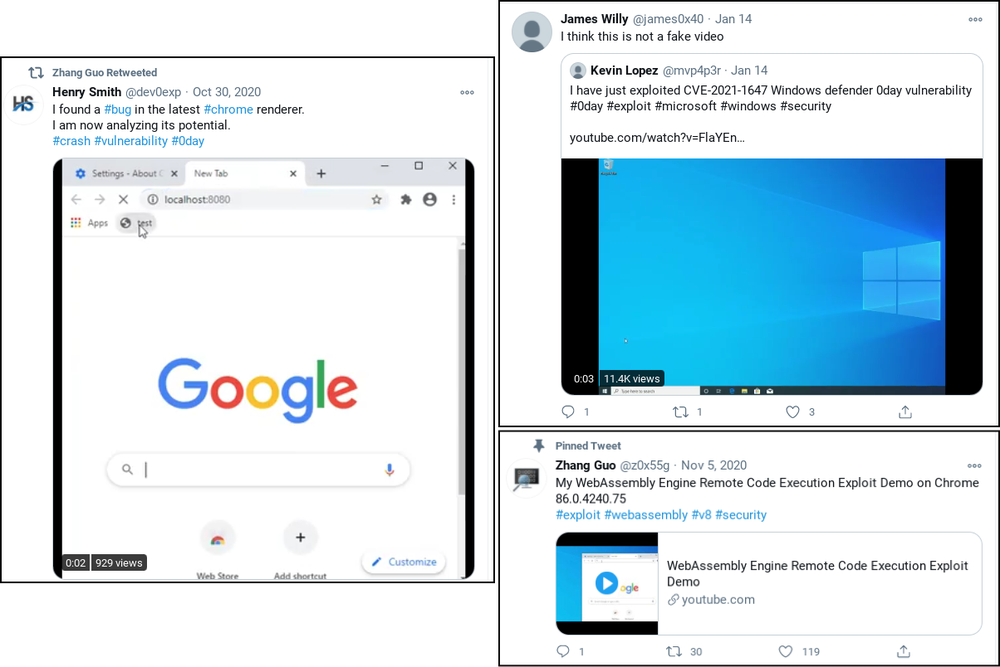
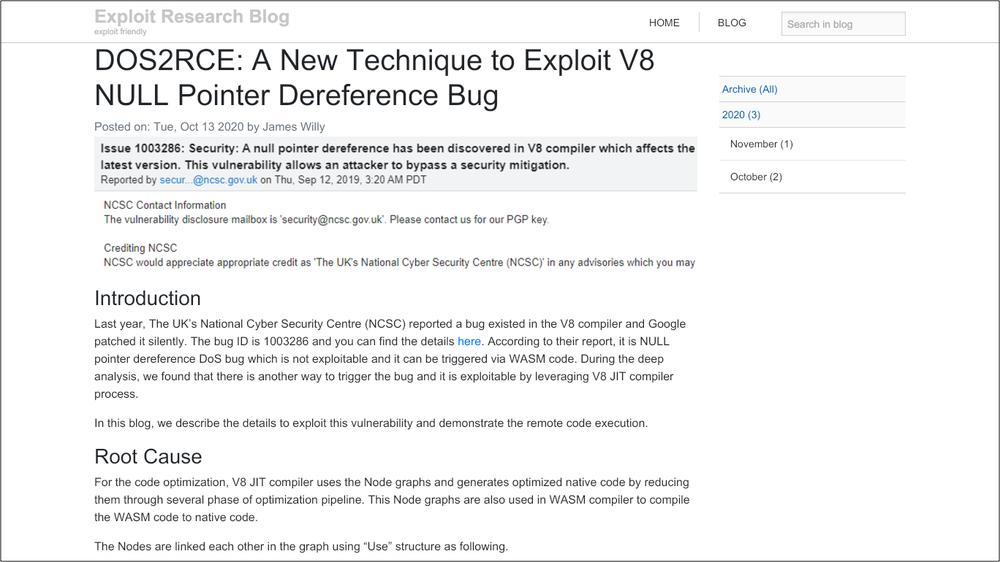
According to Google’s report, the actors are setting up Twitter accounts to interact with security researchers, research blogs where they post stuff relevant to exploits discussed in the white-hat community, PoC videos, and generally create a false sense of belonging to the “good” side. In several cases, the actors publish write-ups of exploits that aren’t working but are still made to appear functional using false evidence and/or fabricated videos. Their purpose is solely deception, so they’re not paying much attention to the actual “research” aspect.
What the actors do is approach prolific security researchers and ask them if they would like to collaborate. They then provide them with a Visual Studio Project, which supposedly contains the source code for exploiting a high-profile flaw. In reality, the pack contains a custom malware in the form of a DLL file, which links to actor-controlled C2 servers and begins exfiltrating whatever data it can pluck from the infected machine.
But direct infections aren’t the only trick up the actors’ sleeve. In some cases, Google noticed researchers being compromised after visiting the fake research blog, resulting in planting an in-memory backdoor that beacons to the C2.
This worked well even for researchers who were using the latest available Windows 10 and Chrome browser, and as Google explains, the mechanism of compromise remains unknown. Most likely, the actors are using some form of a zero-day to achieve this powerful backdoor planting, which underlines how dangerous and skillful these hacking groups are.
The domain used for the identified research blog has been taken offline, while the fake Twitter and LinkedIn accounts associated with the hackers have been reported and suspended by now. However, the actors may try the same tricks with different names and infrastructure soon, so if you’re a security researcher, beware. Faking identities on the internet is fairly easy, so when someone reaches out to you, always treat them with suspicion.