Nine Apps on the Play Store Contained the ‘Clast82’ Trojan Dropper
- Researchers discovered a set of nine Android apps that can fetch malware from GitHub.
- The apps remain innocuous until Google approves them for publication on the Play Store.
- Most of the apps are free VPN solutions, audio recording, and music playing software.
Researchers from Check Point have discovered at least nine apps on the Google Play Store that contained a trojan dropper named Clast82. The finding and reporting happened at the end of January 2021, while Google confirmed removing all dangerous apps on February 9, 2021. However, there’s a good chance that many users out there are still using the dangerous apps, as their deletion from the store doesn’t automatically remove them from people’s devices.
The nine dropper apps are the following:
- Cake VPN
- Pacific VPN
- eVPN
- BeatPlayer
- QR/Barcode Scanner MAX
- eVPN (different package)
- Music Player
- tooltipnatorlibrary
- QRecorder
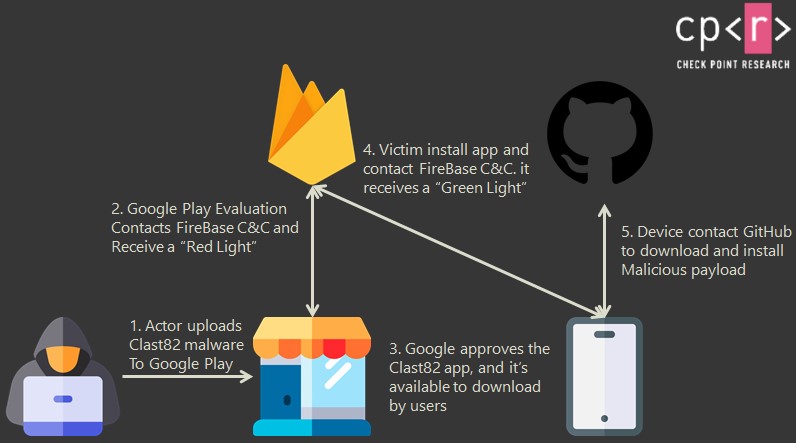
These apps managed to go through Google’s evaluation by keeping their malicious behavior deactivated until they are accepted. Once the app is published on the Play Store, an “enable” parameter is activated, and the dropper can begin fetching a variety of additional payloads onto the compromised device.
From banking trojans to remote access tools, there’s a wide range of things that are passed through Clast82. Check Point says they detected over 100 unique AlienBot payloads, a MaaS Banker that can steam 2FA codes and credentials.
The C&C platform relies on Firebase, while the hosting platform where the payload is fetched from is GitHub. The C&C servers used for this purpose reside on the following domains:
- boloklava87[.]club
- enegal-23[.]net
- balabanga90[.]online
- dsfikj2dsfmolds[.]top
- blakarda[.]site
- sponkisn[.]site
For the installation of the payload, the app has to pull out a special trick to get the user's permission, and that is to serve a fake prompt that is pretending to come from Google Play Services.
Some of the risky apps listed the email address "[email protected]," which is the same as the one used by the GitHub repository owner that hosts the payloads. This tells us that the actor has undertaken large chunks of the operation on his/her own.
To protect yourself from threats that become malicious after they have been approved for publication on the Play Store, you have to use some kind of a mobile protection suite from a reputable vendor. Google’s initial reviews are far from being enough, and no matter how trustworthy an app may appear to be, it can always let hell loose at any point in the future. Also, in this particular case, we see four out of the nine malicious apps being free VPNs, so this is just another example of why you should avoid this software category entirely.