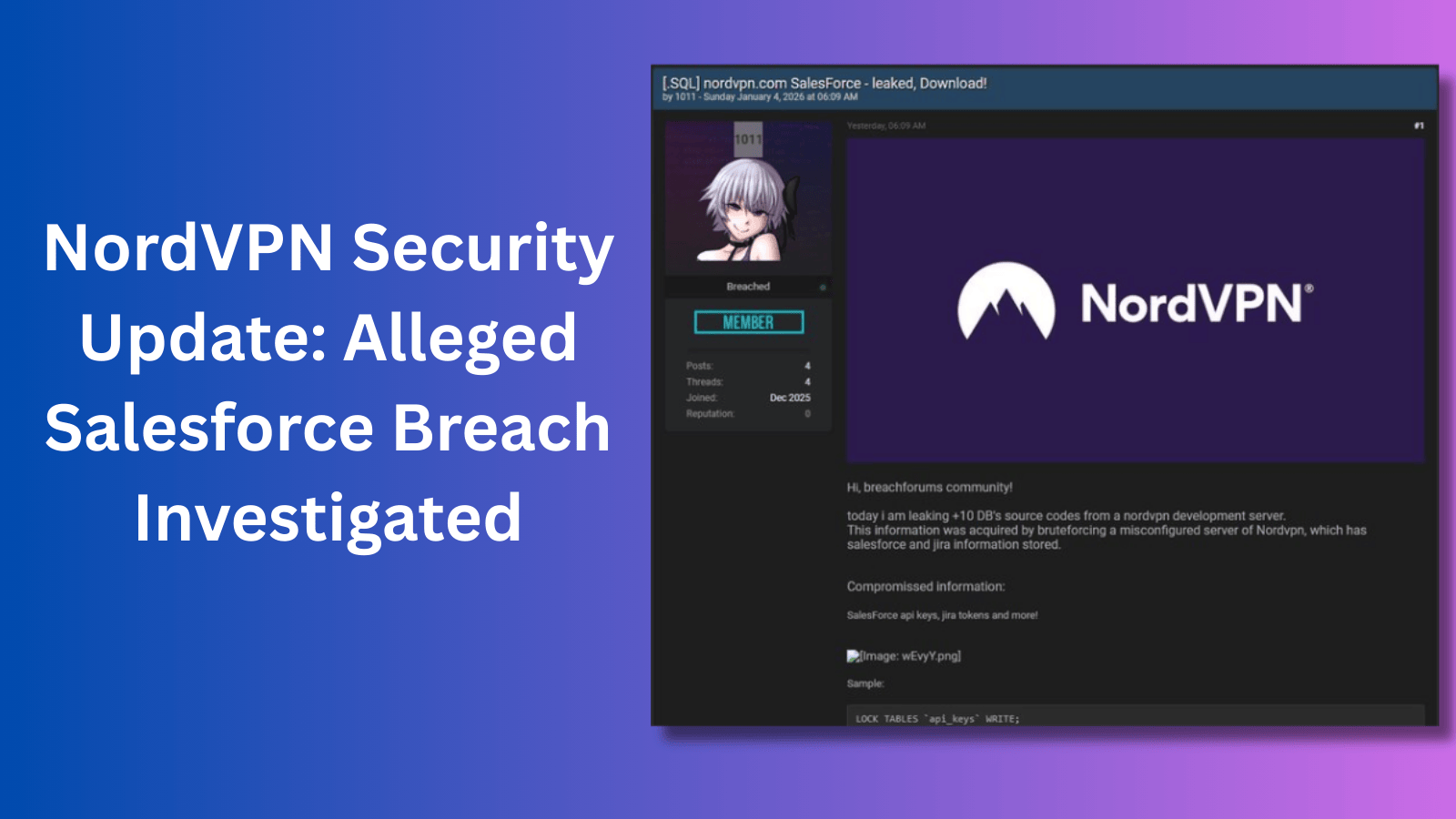
UK Government Admits Flaws in Cyber Resilience Strategy, Overhauls Cyber Policy with New Action Plan
Key TakeawaysPolicy Reset: The U.K. government has acknowledged failures in its previous cybersecurity approach and launched a new Government Cyber…