New Zero-Day Exploit by ‘Stealth Falcon’ Targets Middle East Government and Defense Entities
- Stealth Falcon APT targets government and defense entities in Turkey, Qatar, Egypt, and Yemen via a zero-day exploit.
- The group uses spear-phishing as an entry point to distribute a customized malware toolset.
- Keyloggers, credential dumpers, and passive backdoors are included in their arsenal.
A significant cyberespionage campaign conducted by the advanced persistent threat (APT) group Stealth Falcon utilizes a newly discovered zero-day flaw to execute a series of highly targeted attacks on significant government and defense entities in Turkey, Qatar, Egypt, and Yemen.
The new zero-day vulnerability, CVE-2025-33053, allows remote code execution through manipulation of the working directory.
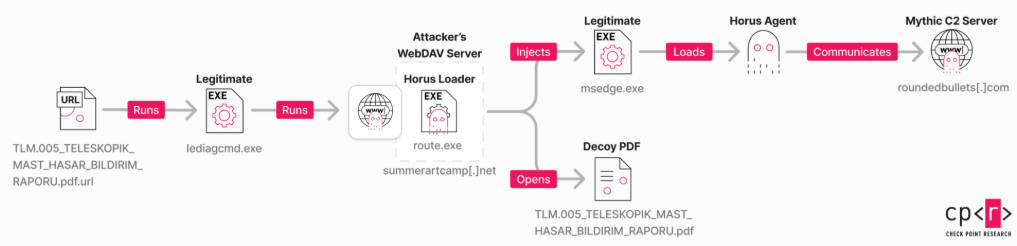
The exploitation was achieved via .url files linked to attacker-controlled WebDAV servers, Check Point Research (CPR) has revealed. Following disclosure, Microsoft issued a critical patch as part of its June Patch Tuesday updates.
The group employed stealth techniques, including tools like the Mythic framework-based Horus Agent. These tools featured obfuscation, anti-detection frameworks, and enhanced victim-specific targeting measures.
Stealth Falcon’s arsenal also includes keyloggers, credential dumpers, and passive backdoors, bolstering their espionage efforts.
Cyberattacks originated via spear-phishing emails containing malicious links or attachments, ingeniously leveraging legitimate executables, like iediagcmd.exe, to initiate infection chains.
Stealth Falcon’s focus on leveraging zero-day vulnerabilities, combined with its ability to bypass security mechanisms, underscores its sophistication. The use of advanced anti-analysis techniques and obscure infection chains demonstrates a concerning adaptability.
With Stealth Falcon operating as a persistent threat since 2012, organizations must remain vigilant. Immediate steps include deploying Microsoft's security patch for CVE-2025-33053, reinforcing endpoint protection, and conducting detailed employee training to recognize phishing attempts.