New WinRAR Trialware Vulnerability Allows MiTM Attacks
- WinRAR trialware has a new vulnerability marked CVE ID – CVE-2021-35052.
- The vulnerability is exploitable to launch a MiTM attack and gain remote device access.
- Users of WinRAR trialware version 5.7 or earlier should exercise caution.
A recent investigation of the WinRAR trial version has revealed a noticeable vulnerability marked as CVE ID – CVE-2021-35052 that potentially enables an attacker to intercept and modify requests intended for the application user. A hacker could use a Remote Code Execution (RCE) on the remote device.
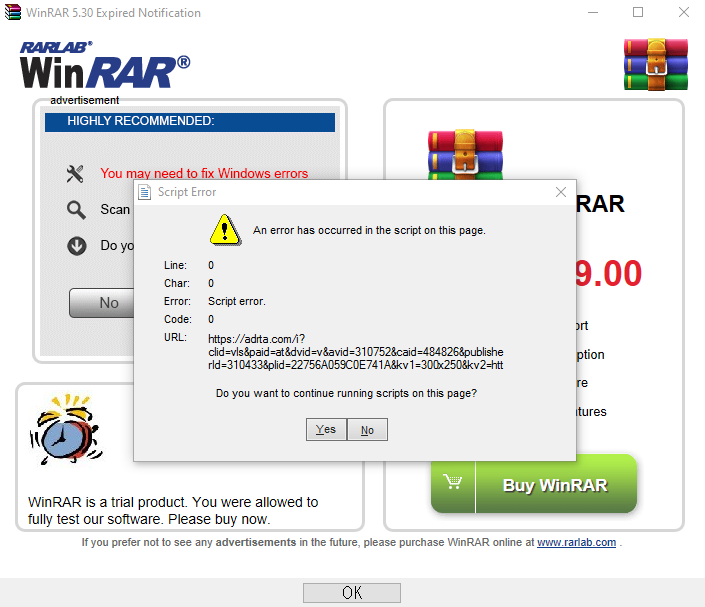
The actual discovery occurred as a matter of chance on WinRAR version 5.70. The app produced a JavaScript error indicating an issue with the WebBrowser JS parser within WinRAR. A little bit of digging allowed the researcher to discover an mshtml.dll file used for implementing Borland C++, WinRAR’s base code language. This file comes up only after the trial period has expired and once every three launches.
To investigate the error further, the researchers linked a Windows proxy setting up a local Burp Suite. The notification request is sent via HTTPS, which relays through the unsecured Burp self-signed certificate. Nevertheless, most users do not actually read the notification and just click ‘Yes.’ This can be a chance to launch a MiTM attack and compromise the user’s device.
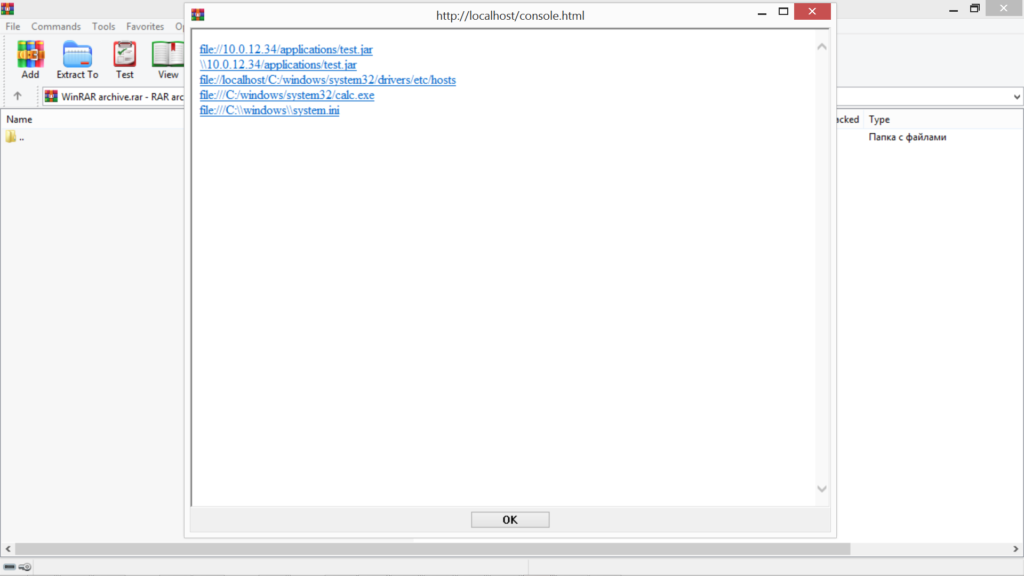
Anticipating this possibility, the researchers tried modifying intercepted responses. They altered the app’s native response code to “301 Moved Permanently” and set up a redirect “attacker.com.” This was a better alternative redirect to “notifier.rarlab.com” which led to the RAR website and all redirects after that went to the “attacker.com.”
Next, the researchers tried using several attack vectors to launch a Man-in-the-Middle attack. This usually requires ARP-spoofing and this put the researchers in Zone 1 of the IE security zones. The majority of these attacks vectors succeeded, but a majority also threw up an additional Windows security warning.
The success criterion was that the prompt option “Run” must be selected instead of “Cancel.” The security warning can be bypassed by simply using RAR files in a WinRAR version earlier than version 5.7. App users are recommended to use paid versions or the latest versions when using .rar files.