New SparkKitty Spyware Campaign Targets iOS and Android Devices Through Official App Stores
- Infected apps infiltrated the Google Play Store and Apple’s App Store to spy on users.
- These spyware-laced apps aim to steal user details, including crypto wallet seed phrases.
- Among them, a messaging app with crypto exchange features was installed over 10,000 times and is still available.
A concerning spyware campaign linked to the earlier-discovered SparkCat initiative is specifically targeting cryptocurrency enthusiasts by attempting to steal sensitive information like wallet seed phrases through malicious apps, including TikTok replicas.
What’s alarming is that these infected apps have infiltrated both the Google Play Store and Apple’s App Store, platforms typically trusted for secure downloads.
On Android, the malware appears as Java and Kotlin-based Trojans, with the latter using an Xposed module approach. On iOS, it hides within fake frameworks (e.g., AFNetworking.framework) or uses obfuscated libraries like libswiftDarwin.dylib.
This spyware relies on Optical Character Recognition (OCR) to scan images from users' photo galleries. It searches specifically for sensitive content such as cryptocurrency-related text, especially screenshots with wallet details.
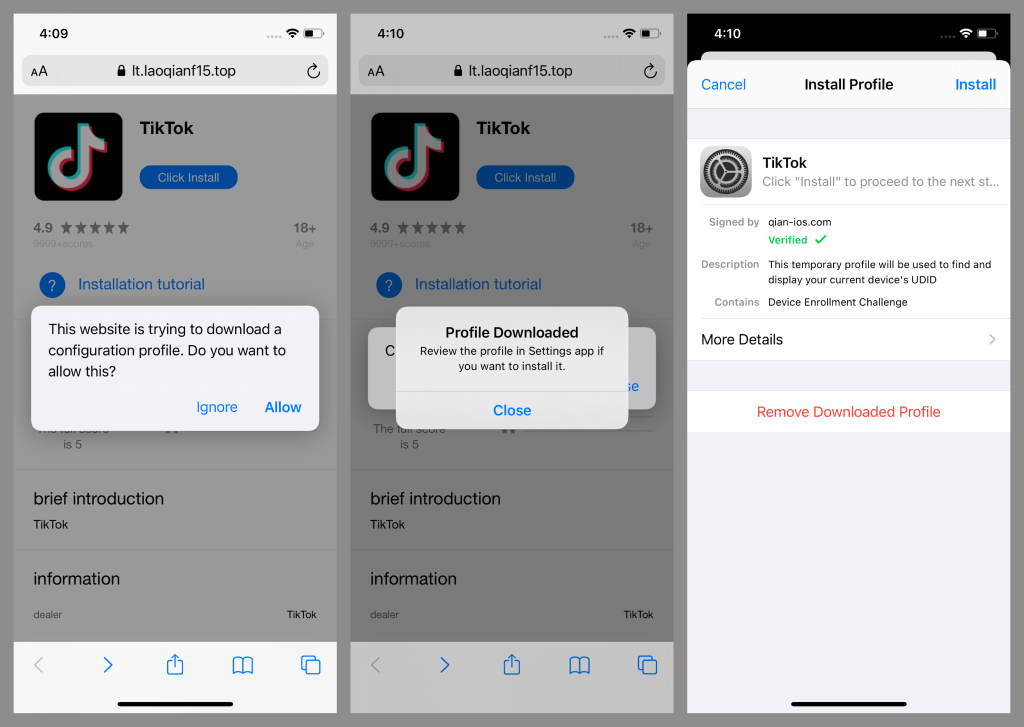
The spyware spreads through unofficial websites and official app stores, often disguised as mods or tools for popular applications, like TikTok. Some apps also came pre-configured to link users to sketchy online stores primarily accepting cryptocurrency payments.
Researchers have uncovered that the campaign has been active since at least February 2024, highlighting its persistence and evolution.
Attackers leverage enterprise provisioning profiles on iOS to bypass App Store restrictions, granting frictionless installation of malicious apps. Android users are equally at risk through APKs distributed on third-party sites.
Once installed, the malware exfiltrates images to attacker-controlled servers. Permission requests for gallery access often appear innocuous, but they indicate malicious intent. Additionally, the spyware’s use of encrypted communication with Command and Control (C2) servers adds sophistication to its functionality.
Security researchers notified Google about one of these apps, which is a still-availalbe messaging app with crypto exchange features that ontained a malicious payload and was download over 10,000 times.
Affected regions appear concentrated in Southeast Asia and China. However, the scope of the threat could easily expand globally.
Researchers also discovered many download pages for various scam iOS apps in the PWA (progressive web app) format, whose code strikingly resembled the pages distributing the malicious TikTok version.
Some of these PWA-containing pages also included a section prompting users to download a mobile app. For Android users, the link downloaded an APK file that opened the scam platform via WebView and requested access to read storage.
Kaspersky affirms with moderate confidence that this activity cluster could be connected to SparkyKitty due to the overlap in cryptocurrency theme focus, similar tactics, and distributing similar iOS PWAs.