New Sextortion Botnet Spotted in the Wild and Getting Out of Hand
- Cofense warns that a new sextortion campaign is growing out of proportion quickly.
- Already, it operates on a database of 330 million email addresses and 7.4 million unique domains.
- The recipients are asked to pay $554 in Bitcoin in 48 hours, otherwise, a video feed will supposedly go public.
Researchers from the Cofense Labs warn about a new threat that is based on sextortion scamming. The ongoing campaign that was spotted in the wild initiated operations in June 2019, using a list of 200 million email addresses. Right now, the botnet database counts 330 million email addresses, so the botnet is growing. The situation with the number of targeted web domains is similar, with a notable increase from 6 million domains in the summer to 7.4 million unique domains right now.
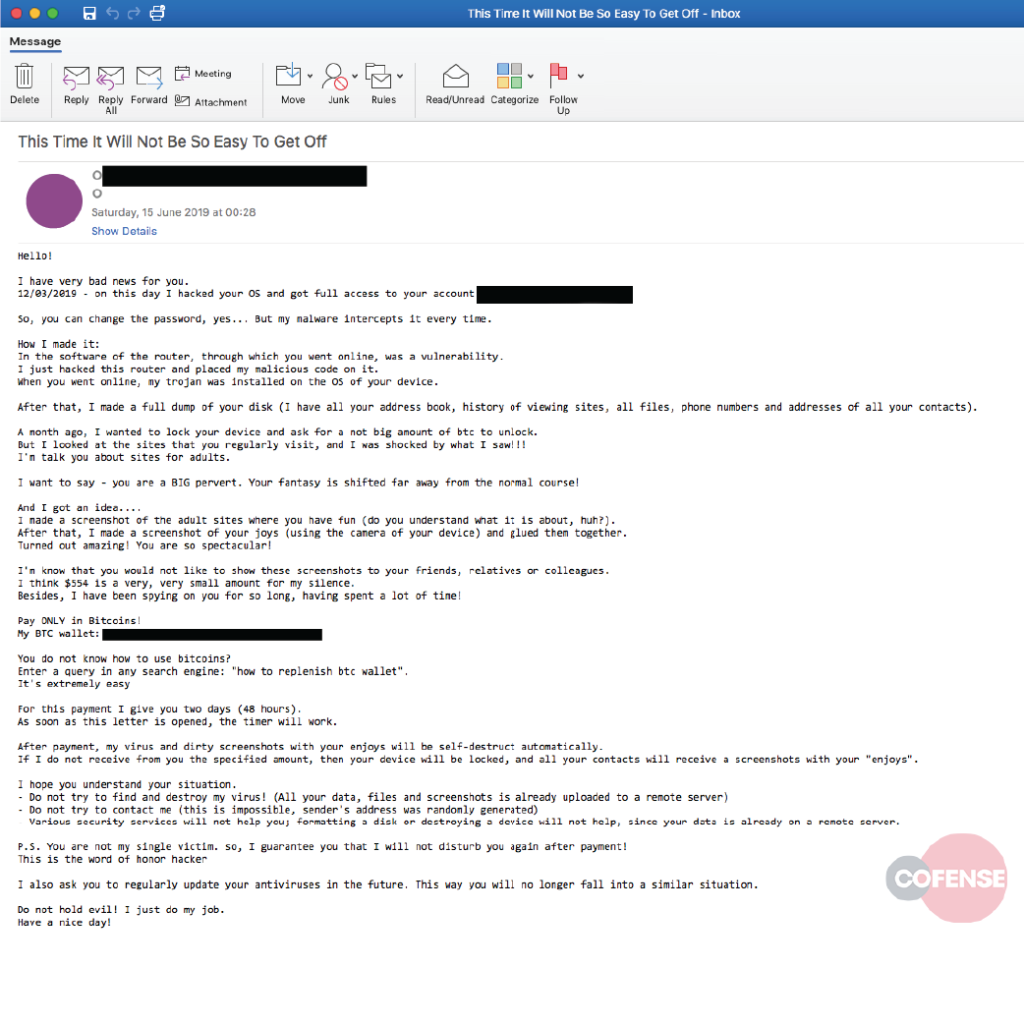
The message that is circulated is shown below, and it’s an empty threat trying to convince the recipient of an alleged password interception. The sender claims to have hacked the victim’s OS, fully accessing their account, and planting malware so that any subsequent password changes will be intercepted again. Where this turns into a “sextortion” is when the sender claims that he/she has seen the sites the recipient visits, and threatens to publicly release screenshots and webcam feeds of the person’s most embarrassing moments. To buy the scammer’s silence, the victim will have to pay $554 in Bitcoin, and the time margin for this is 48 hours.
Source: Cofense
The actor is even providing instructions on how to pay in Bitcoin and warns the victim not to try and find the malware or format the device, as the screenshots have already been uploaded to their server. Also, they promise not to disturb the victim after the payment has been made. Obviously, all of these are blatant lies. There are no files that have been stolen, no malware that has been planted, and no risks of having your personal moments exposed. That said, paying the actor would be a bad idea, as even if they had something tangible to substantiate their threat, it would be impossible to guarantee that paying will stop the extortion.
Back in August, we saw a sextortion campaign case involving the Varenyky malware, which did record people’s screens using FFmpeg tools. In that case, the amount to pay was 750 Euros in Bitcoin, and the timeframe was 72 hours. Even then, paying the actors resulted in repeated extortion rounds, as this was reflected in the actors’ BitCoin wallet. Sextortionists will try to make the most out of their victims, so no matter what they promise to you, paying them will only result in more threatening.
Have you ever fallen victim to a sextortion campaign? Let us know of the details in the comments down below, or help us spread the word by sharing this post through our socials, on Facebook and Twitter.