A New Ransomware Group Is Calling Hackers to Join the “DarkSide”
- The “DarkSide” is a new RaaS group that is targeting high-profile companies that have economic stability.
- The group is preparing custom payloads, custom ransom notes, and even professional press releases.
- This is just another addition to an already populated and problematic space, making the situation even worse.
A new ransomware as a service (RaaS) group named “DarkSide” has emerged on the dark web, taking its first tentative but otherwise solid steps in August 2020. Digital Shadows has been following the new group’s first operations and confirms that the DarkSide is a fairly typical group of actors adding itself to the rising trend of “ransomware as a corporation.”
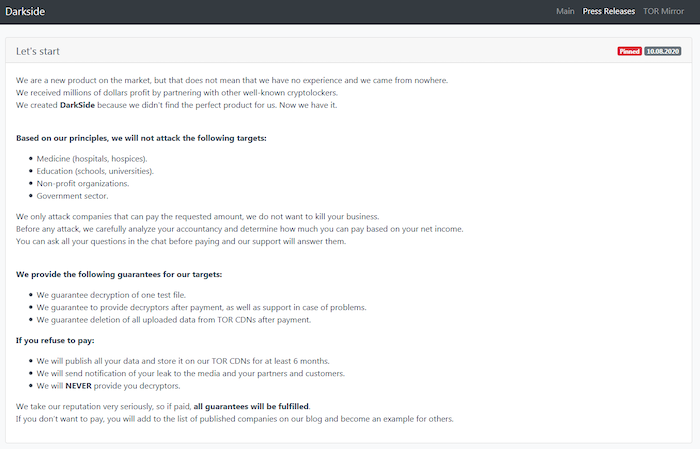
What makes DarkSide different is that the group wants to target economically strong entities, they are using custom executables for each target, and they also like to release pro-grade press releases.
So, the DarkSide operators’ guidelines make it clear that companies in the education, healthcare, non-profit, and the government sector are excluded, and so are firms that don’t have impressive revenue figures at this moment. This is something that points to attack efficiency, but also to the existence of an ethical compass for these actors.
Source: Digital Shadows
While the ransomware executable is customized depending on the target, it generally executes PowerShell commands and deletes Shadow Volume Copies to prevent data recovery attempts. Databases, applications, and mail clients are also terminated as the system is prepared for full encryption. In some cases, there have been indications that the DarkSide operators used TeamViewer to access the target computers.
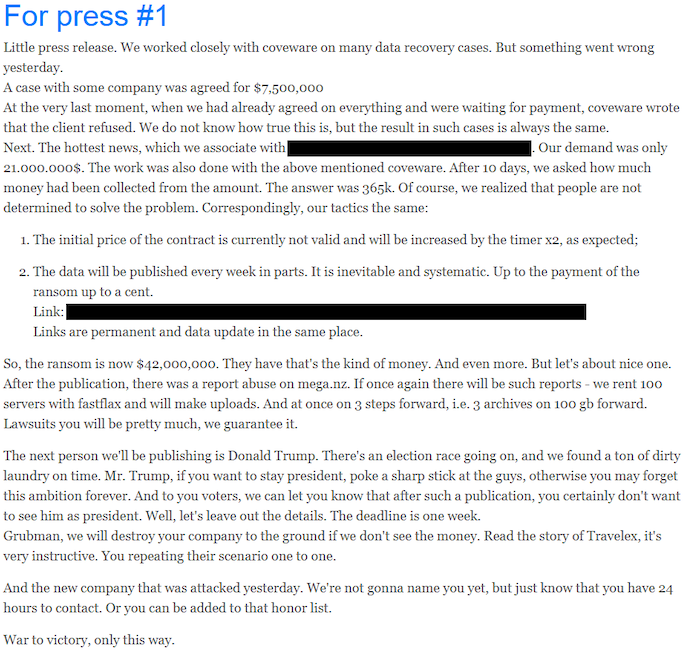
The ransom note is also highly personalized, containing many details about what data has been exfiltrated, a link to the corresponding leak site entry, and what will happen if the ransom demands aren’t met. As for the press releases, these help DarkSide maintain a professional image and convince the victims that they are dealing with serious actors. Moreover, press releases are further pulling the lever of pressure to the extorted entity, as the data leak is further publicized.
Source: Digital Shadows
Although still pretty young, it is estimated that the DarkSide ransomware group has already made about one million USD, although Digital Shadows couldn’t confirm this figure. As for the possibility of affiliations and collaborations, the group follows similar tactics as DoppelPaymer, Sodinokibi, Maze, and NetWalker, but there are no infrastructural overlaps or any other concrete evidence of a connection with other notorious groups.
DarkSide is just another entry in a growing list of RaaS actors, further magnifying a problem that the authorities have failed to find an answer for. The threat landscape is becoming more intricate and complex, and every addition in the RaaS space is pushing control efforts to the “futile” territory. Already, companies have to defend against armies of actors coming from every direction.
Read More:
- “Maze” Ransomware Adopts the “Ragnar Locker” VM Wrapping Trick
- New “SunCrypt” Ransomware Gang Joins the ‘Maze’ Cartel
- New RaaS “SMAUG” Wants to Take All the Ransomware Treasure
- The Role of Initial Access Brokers in the Ransomware Scene