New Multi-Stage Malware Campaign Uses Fake CAPTCHAs to Deliver NetSupport RAT
- A novel malware campaign infects users with NetSupport RAT via fake Gitcode and Docusign pages.
- Hackers use phishing emails and social media, with spoofed document verification and tool-sharing prompts as initial lures.
- Attackers evade traditional signature-based detection and complicate forensic analysis via multiple script stages.
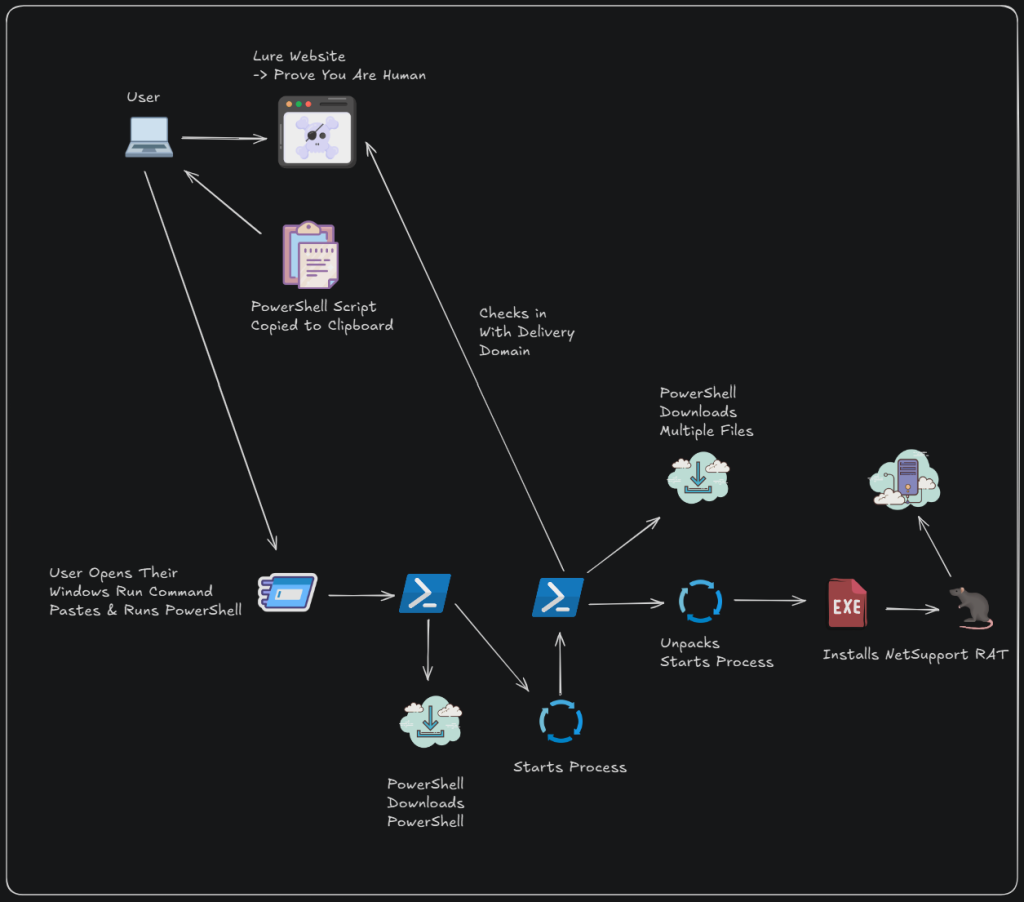
A sophisticated new cyber threat campaign has been uncovered, leveraging deceptive “Prove You Are Human” prompts and multi-stage PowerShell scripts to infect users with NetSupport RAT, a widely abused Remote Access Trojan.
Threat actors are actively deploying fake verification pages that masquerade as legitimate services like Gitcodes and Docusign. Users visiting these sites are tricked into copying and pasting malicious PowerShell scripts into their Windows Run prompt.
This simple act initiates a complex sequence. The downloaded script acts as a first-stage downloader, reaching out to external domains to fetch additional payloads, the latest The DomainTools Investigations (DTI) team security report said.
Each payload is a new downloader, designed to retrieve successive scripts, making 3 or more web requests to additional domains.
Ultimately, these scripts install NetSupport RAT on the target machine, establishing persistence by masquerading as a legitimate process and adding itself to the user’s startup applications.
A key component of this campaign involves clipboard poisoning delivered through fake CAPTCHA verifications.
Victims are instructed to copy a pre-filled, ROT13-encoded script into their systems. This script decodes itself, downloads further payloads (such as “wbdims.exe” from GitHub), and creates a scheduled task or registry entry for persistence.
The attackers employ a disposable and resilient infrastructure, including domains registered with providers such as Cloudflare, NameCheap, and NameSilo, the use of lookalike Gitcodes and Docusign domains, and multiple script stages to evade traditional signature-based detection and complicate forensic analysis.
These campaigns are propagated via phishing emails and social media, with spoofed document verification and tool-sharing prompts as initial lures. By segmenting the attack into many stages and rapidly rotating infrastructure, actors succeed in evading many conventional security controls.